Okta Identity Engine release notes (2022)
December 2022
2022.12.0: Monthly Production release began deployment on December 12
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta MFA Credential Provider for Windows, version 1.3.8
This version of the agent contains bug fixes and security enhancements. See Okta MFA Credential Provider for Windows Version History.
Identity Governance
Okta Identity Governance is a SaaS-delivered, converged, and intuitive Identity and Access management platform. Use it to simplify and manage your identity and access lifecycles across multiple systems and improve the overall security of your company.
Use Okta Identity Governance solutions, such as Access Certifications, Access Requests, and Reports to:
-
Efficiently create, protect, and audit access to critical resources.
-
Improve your company’s security. Increase employee productivity.
-
Improve IT efficiency by automating tasks to reduce the time taken and errors associated with manual data entry and provisioning tasks.
See Identity Governance.
Note that Okta Identity Governance is available to customers on a subscription basis. For more information, contact your Account Executive or Customer Success Manager.
Preview the token inline hook
Before implementing a token inline hook, you can now preview the hook request and the external-service response in the Admin Console. This feature aids in the development and testing of inline hooks before releasing to a production environment. See Preview an inline hook and Preview and test the token inline hook.
IE and Edge Legacy plugins
You can no longer download the Internet Explorer (IE) and Edge Legacy browser plugins from the Downloads page. These plugins aren't supported.
Improvements to the sign-in experience
When users create an account using the Sign Up link in the Sign-In Widget, they enter their first and family names along with their email address on the first page. The Sign-In Widget then displays the authenticators page, where users enter a password and configure any other mandatory authenticators. To streamline the sign-up process, the Self-Service Registration with Password feature allows you to show the password entry on the first page of the enrollment form instead. See Collect profile information and register users.
Manage embedded widget sign-in support
Okta provides the Okta Sign-In Widget out of the box so that customers can authenticate users by simply redirecting them to the widget. For customers who need a customized sign-in experience, Okta also provides a widget SDK that developers can embed within their applications. This embedded widget uses a custom authorization mode called the Interaction Code grant type to authenticate users. The Embedded widget sign-in support toggle allows super admins to disable the embedded sign-in option across all applications and authorization servers. This helps to create consistency and improves the security posture of your applications. See Configure embedded sign-in support.
Security enhancement of Okta Verify push notifications
To help users recognize and prevent phishing attacks, Okta Verify push notifications on mobile devices and Apple Watch include the name of the app to be accessed and the org URL.
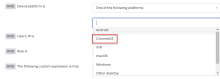
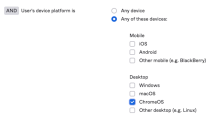
ChromeOS as a device platform
You can now select ChromeOS as a device platform in authentication policy rules or identity provider routing rules. This enables you to configure how users access Okta-protected resources from ChromeOS devices. See Add an authentication policy rule and Configure identity provider routing rules
Authentication policy rules:
Identity provider routing rules:
Certificate chain builder for Smart Card IdP
Admins can now upload individual certificate files to build a certificate chain for a Smart Card IdP. This eliminates the requirement to manually create a file that contains the certificate chain. See Add a Smart Card Identity Provider.
Telephony usage report
The Telephony usage report displays data about an org’s telephony events over time. The report can be filtered by voice or SMS events and helps admins quickly understand usage trends and troubleshoot deliverability or request issues. See Telephony usage report.
Email deliverability events in the System Log
Admins can now view the following email deliverability event types in the System Log:
- Delivered
- Deferred
- Dropped
- Bounce
This helps admins better monitor the email deliverability activity in their org. See System Log.
Enhancements
Single sign-out changes for custom domains
If an admin signs out from a custom domain, their Admin domain and subdomain sessions now remain active. If they sign out from the Admin domain or subdomain, their custom domain session is ended.
People page improvements
People page filter results are improved as follows:
-
Status > Password reset filter results now include users with both Password expired and Password reset status.
-
Status > Active filter results return only users with an active status.
Early Access Features
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-508888
Some orgs were unable to configure their global session policies to display the password-first Sign-In Widget.
OKTA-509453
Staged and provisioned user accounts received different error messages when they clicked Forgot password? on the Sign-In Widget. This occurred in orgs with User Enumeration Prevention turned on.
OKTA-527215
Routing rules incorrectly redirected some users to an IdP before they could enter their username.
OKTA-532720
Some YubiKeys didn't work for authentication even though they were successfully enrolled.
OKTA-534595
Admins with a custom role couldn't edit the users in a group if the group was assigned to an app with profile sourcing enabled.
OKTA-536037
When a DELETE request to the /api/v1/authorizationServers/<authServerID>/clients/<clientID>/tokens endpoint was called for large scale operations, an HTTP 500 error was returned.
OKTA-538402
Some admins weren't able to delete network zones after they upgraded to Identity Engine.
OKTA-541442
Errors during federation sometimes didn't display the cause of the error.
OKTA-542472
The authn_request_id information was missing from the user.authentication.auth_via_mfa System Log event for Okta Verify Push verifications.
OKTA-544783
The Norwegian translation of the end-user settings and preferences menu was incorrect.
OKTA-546310
Admin roles that were constrained to a group with group rules couldn't be assigned to a user or group.
OKTA-547525
The Welcome page, SMS reminder prompt, and security image prompt weren't displayed for users accessing Okta using AD SSO in incognito mode.
OKTA-549174
After upgrading to Identity Engine, orgs with custom domains couldn't use getRequestContext in the Sign-in page code editor.
OKTA-549537
The Box integration provisioning menu didn't display the correct settings.
OKTA-549886
Using an Agentless DSSO test endpoint without any routing rules configured to use ADSSO resulted in a 404 error.
OKTA-550773
Some orgs didn't correctly recognize a sign-in attempt using a smart card.
OKTA-550789
Provisioning new users from Okta to Office 365 failed.
OKTA-551130
The Email Authenticator challenge lifetime was sometimes set to five minutes regardless of its value in the authenticator settings.
OKTA-552637
Users were sometimes signed out of Okta right after signing in if the tokens returned were too large.
OKTA-552810
Customized sign-in pages for orgs using a custom domain didn't render properly.
OKTA-553284
When the full-featured code editor was enabled, updates to email customizations, custom error pages, and the sign-in page didn't trigger System Log events.
OKTA-557858
Internet Explorer 11 users were blocked from signing in to orgs that used custom domains.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Chase (OKTA-549904)
-
iAuditor (OKTA-549658)
-
MeridianLink Consumer (OKTA-541626)
-
Office 365 Dynamics (OKTA-549978)
-
Quickbooks (OKTA-549905)
Applications
Application Update
The Update user attributes feature is added to the Lucca Provisioning integration.
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Alibaba Cloud: For configuration information, see Synchronize users or groups in Okta by using SCIM.
- Condeco Software SCIM: For configuration information, see How to configure SCIM provisioning for Okta.
- Couchdrop: For configuration information, see Setup User provisioning between Couchdrop and Okta.
- Crewmojo: For configuration information, see Crewmojo Help.
- Greenhouse Recruiting: For configuration information, see Configuring Provisioning for Greenhouse Recruiting.
- Intercom: For configuration information, see Configure SCIM Provisioning with Okta.
- Totango: For configuration information, see Enable SCIM Integration in Totango.
- Zoominfo: For configuration information, contact Zoominfo.
SAML for the following Okta Verified applications:
-
Brex (OKTA-540264)
-
Loom (OKTA-551214)
-
NeuralLegion (OKTA-545950)
-
RudderStack (OKTA-552363)
-
ZoomInfo (OKTA-543975)
OIDC for the following Okta Verified applications:
- Aon Inpoint ClaimsMonitor: For configuration information, see Aon Inpoint ClaimsMonitor application and Okta Single sign-on Integration Guide.
- CoRise: For configuration information, see Logging in to CoRise with Single Sign-On (SSO) through Okta.
- FlexDesk: For configuration information, see How-to: Setup Single Sign-On through Okta.
- Ortto: For configuration information, see Add and configure the Ortto app in Okta.
- Sastrify: For configuration information, see Okta Configuration Guide.
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-508227
Admins could save a routing rule with an inactive IdP.
OKTA-534930
Some orgs had an identifier-first sign-in page despite setting up a password-first flow in their global session policy.
OKTA-537583
The System Log didn't display the policy.rule.update event when new condition types were added to a policy rule.
OKTA-537600
Email notifications were sent to users' secondary email address.
OKTA-537805
Deactivated users weren't displayed on the People page if their Username started with their user ID.
OKTA-540795
An error occurred when an admin searched for an ineligible group on the Edit resources to a standard role page.
OKTA-541582
The Custom OTP authenticator disappeared from the list of additional factor types in the authentication policy rule preview when Exclude phone and email authenticators was selected. Additionally, the Device bound characteristic wasn't displayed for the Custom OTP authenticator in Authenticators > Setup.
OKTA-549212
When a custom app used the /sso/idps/{idpId} endpoint for IdP routing with a login_hint parameter, the login_hint was ignored.
OKTA-549434
Admins couldn't update the username for an app.
OKTA-549687
Reimporting a CSV directory failed if the Deactivation field and Deactivation value were removed after the initial import.
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- GLS OnDemand SCIM Provisioning: For configuration information, see GLS OnDemand Okta SCIM Provisioning Integration.
SAML for the following Okta Verified applications:
-
Inclusivv (OKTA-534561)
-
Remote.It (OKTA-550812)
-
Silo (OKTA-543573)
OIDC for the following Okta Verified applications:
- babelforce.com: For configuration information, see SSO for Okta.
- Darzin: For configuration information, see Darzin Okta SSO.
- Openli: For configuration information, see ow to set up Okta Single Sign-On integration.
- Testfully: For configuration information, see Okta x Testfully.
Fixes
General Fixes
OKTA-476668
Sign-in redirect URIs couldn't be edited when their character limit was reached.
OKTA-534847
When users edited their sign-in methods from the User Settings page in a custom domain, the Back to settings link didn't appear.
OKTA-539174
The image icon for groups sourced from Slack was displayed as a broken link.
OKTA-539424
After an update was pushed from Okta, the Phone Number attribute wasn't removed from Workplace by Facebook as expected.
OKTA-548256
Groups assigned by group rules couldn't be removed from deactivated users.
OKTA-550088
New users didn't see the optional authenticators page during self-service registration if Show password field on the first page of the enrollment form was selected in a profile enrollment policy.
OKTA-550600
The Custom Authenticator didn't automatically send push verifications.
OKTA-551632
In Preview orgs, attempts to save sign-in page edits sometimes failed when using the full-feature code editor.
OKTA-553024
The Edit resources to a standard role page didn't indicate that only the first 5 groups or 10 apps appear when you search for a resource.
OKTA-555812
Super admins couldn't open the Edit resource set page for admin roles that were constrained to a deleted workflow or authorization server.
OKTA-558105
Authentication policies that required hardware protection as a possession factor constraint didn't correctly evaluate YubiKey OTP authenticators.
OKTA-558264
Authentication policies that used possession factor restraints required all active authenticators to support all constraints.
OKTA-558878
Incremental imports for Jabil didn't switch to full imports when there were large number of changes.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- babelforce.com: For configuration information, see Configuring SCIM.
- Bitwarden: For configuration information, see Bitwarden Okta SCIM integration.
- Pendo: For configuration information, see Pendo Configuration Guide (you'll need to sign in).
SAML for the following Okta Verified applications:
-
Flow of Work Co (OKTA-542871)
-
Quortex I/O (OKTA-542825)
Fixes
General Fixes
OKTA-527930
The Custom Authenticator couldn't disable user verification when the Okta Verify authenticator's user verification setting was set to required.
OKTA-528185
The admin reset password flow showed the New password field instead of the Enter code field when entering a phone/SMS code after enrolling a phone authenticator.
OKTA-550600
The Custom Authenticator didn't send push notifications even though the Send push automatically option was selected.
OKTA-554308
Selecting Sign out from all other devices/sessions on the End-User Dashboard didn’t work for AD/LDAP users.
OKTA-559113
Users whose orgs were upgraded to Identity Engine received an invalid credential error after successfully authenticating with the Okta Verify number challenge method.
Applications
New Integrations
SAML for the following Okta Verified application:
-
Please Share (OKTA-557897)
OIDC for the following Okta Verified applications:
- Kanbina AI: For configuration information, see Kanbina AI Documentation.
- LeadLander: For configuration information, see LeadLander Okta configuration guide.
- Riot Single Sign-on: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
- Tracxn: For configuration information, see Configure SSO between Tracxn and Okta.
November 2022
2022.11.0: Monthly Production release began deployment on November 14
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta AD Agent, version 3.13.0
This version of the agent contains the following changes:
- Health check of auto update service before auto update process is started
- Web proxy support for agent auto update feature
- Updated log category for existing logs from DEBUG to INFO
- Security fixes
Okta RADIUS Server agent, version 2.17.7
This version of the agent contains security fixes and resolves a memory leak that occurred when agents were configured for EAP-TTLS. See Okta RADIUS Server Agent Version History.
Improvements to the self-service password reset experience
Previously, the self-service password reset (SSPR) flow created unnecessary friction in the user experience. The newly enhanced SSPR feature introduces a seamless magic link experience for password reset emails. Users no longer need to provide consent when using the same browser. After a successful password reset where the password meets the application’s assurance policy, the user is signed directly to the app. See Configure the Email authenticator. This feature is currently enabled by default for new orgs only.
Improvements to the self-service unlock process
Earlier versions of the self-service unlock (SSU) flow created unnecessary friction in the end user experience. The newly enhanced SSU feature introduces a seamless magic link experience in emails sent out to unlock accounts. Users no longer need to provide consent when using the same browser. In addition, after successfully unlocking their account, clicking the email magic link counts towards the application's assurance policy. After the assurance requirements are met, the user is signed directly in to the application. See Configure the Email authenticator. This feature is currently enabled by default for new orgs only.
New permissions for custom admin roles
Super admins can now assign these new permissions to their custom admin roles:
- Manage authorization server
- View authorization server
- Manage customizations
- View customizations
The authorization server permissions can be scoped to all or to a subset of the org’s authorization servers. With these new permissions, super admins can now create custom admin roles with more granular permissions for managing their org’s customizations and authorization servers. See About role permissions.
New HealthInsight tasks
Two new HealthInsight tasks help admins improve the security of their global session policies. HealthInsight now provides guidance for increasing the required authentication frequency for specific resources, and for requiring high-risk users to provide MFA every time they sign in. See Change the authentication frequency and Evaluate a risk score for each request.
Event hooks for consent revocation
Consent revocation events are now selectable for use with event hooks. See Create an event hook . See Event Types for a list of events that can be used with event hooks.
Agentless Desktop Single Sign-on
With Agentless Desktop Single Sign-on (DSSO), you don't need to deploy IWA agents in your Active Directory domains to implement DSSO functionality. This reduces or eliminates the maintenance overhead and provides high availability as Okta assumes responsibility for Kerberos validation. See Active Directory Desktop Single Sign-on.
Polling support for Agentless Desktop Single Sign-on and Integrated Windows Authentication sessions
Agentless Desktop Single Sign-on (ADSSO) and Integrated Windows Authentication (IWA) authentication sessions now include polling to reduce the likelihood of service disruptions during periods of high bandwidth use. For users authenticating with ADSSO or IWA during peak periods, this change increases the likelihood that a server will be available to process their authentication request. See Active Directory Desktop Single Sign-on.
Agentless Desktop Single Sign-on authentication progress updates
Agentless Desktop Single Sign-on (ADSSO) authentication progress pages have been updated to make authorization and verification progress more visible and improve the user experience. See Configure agentless Desktop Single Sign-on.
Password expiration settings for Active Directory
You can specify the password expiration policies for Active Directory for all preview organizations to set the maximum password age in days and the number of days before password expiration when the user receives a warning.
JIT users from Active Directory
Just-In-Time (JIT) provisioning enables automatic user account creation in Okta the first time a user authenticates with Active Directory (AD) delegated authentication, Lightweight Directory Access Protocol (LDAP) delegated authentication, or Desktop SSO. JIT account creation and activation only works for users who aren't already Okta users. This means that users who are confirmed on the import results page, regardless of whether or not they were subsequently activated, aren't eligible for JIT activation. When JIT is enabled, users don't receive activation emails. See Add and update users with Active Directory Just-In-Time provisioning and Add and update users with LDAP Just-In-Time provisioning.
Service Principal Name functionality improvement
New Service Principal Name (SPN) functionality allows Agentless Desktop Single Sign-on (ADSSO) authentication to continue without interruption when an SPN is updated. A service account and an SPN are required for ADSSO Kerberos authentication. With this change, you can now update the SPN frequently as an additional security precaution. See Create a service account and configure a Service Principal Name.
Enhanced Okta LDAP integrations with Universal Directory
Okta LDAP integrations now feature custom mapping, schema discovery, and a fully extensible attribute schema that allows you to import or update any attribute stored in LDAP. With these enhancements, Okta LDAP matches the schema functionality already available to Active Directory integrations. See Profile Editor.
OpenLDAP support for Auxiliary Object classes
You can now input a comma-separated list of auxiliary object classes when importing users from LDAP. See Configuring Your LDAP Settings.
New rate limits dashboard filter
You can now filter the APIs listed on the rate limits dashboard by their rate limit multiplier eligibility status. See Rate limit monitoring.
Enhancements
Eligible authenticators in Security Methods list
The Security Methods list on the Settings page now displays only those authenticators that a user may enroll in as determined by the configuration of the org's authenticator enrollment policy. This improves the user experience by ensuring that users are only presented with options that lead to successful authenticator enrollment.
ISV Portal email address updated
The email address for ISV Portal communications is now oanapp@okta.com.
Invalid phone numbers rejected
Okta now rejects attempts to enroll a toll-free, premium, fixed-line (SMS), or any other invalid or unrecognized phone number. This ensures that only valid phone numbers are used for multifactor authentication or device enrollment. See Configure and use telephony.
Enhancement to System Log event
The USER_AUTHENTICATION_AUTH_VIA_MFA System Log event has been enhanced. It now records the URL and IP address of a suspicious website and the mismatched origin header from the HTTP request when Okta detects and blocks a phishing attempt. This enhancement enables admins to track patterns of suspicious activity.
Early Access Features
New Features
Phishing-resistant authenticator requirement
To enhance security, admins may now require users to authenticate using a phishing-resistant authenticator when enrolling additional authenticators. This feature protects the authenticator enrollment process from phishing attempts. See Require phishing-resistant authenticator to enroll additional authenticators.
Enhancements
Log Stream event structure update
For consistency the report structure for Log Stream events is now the same as that for System Log events. The following fields are changed and might need updating for any monitoring scripts in use:
-
Under devices, osPlatform is now platform.
-
The ipChain array is now correctly nested under request instead of client.
-
The extraneous field insertionTimestamp is removed.
Fixes
General Fixes
OKTA-476449
Admins could create resource sets that contained duplicate resources.
OKTA-512927
Two different Okta users could be linked to the same AD user through provisioning.
OKTA-515733
Users were sometimes signed out of Okta right after signing in if the tokens returned were too large.
OKTA-523330
Okta Provisioning Agent (x64 RPM) and Okta Provisioning Agent (Windows x64) were incorrectly swapped.
OKTA-526726
When admins deleted a property in an implicit app user schema, a property with the same name couldn't be recreated after the deletion.
OKTA-529966
Users couldn't enroll a Voice Call Authentication (MFA) factor if Twilio was used as the provider and the phone number had a comma in its extension.
OKTA-530843
Parallel JIT requests for the same username created duplicate users.
OKTA-532898
A long text string was displayed outside of the General Settings page in OIN Manager.
OKTA-532900
The Enter your Post Logout Redirect URI field for OIDC settings in OIN Manager didn't accept all valid URLs.
OKTA-533309
When signing in to a RADIUS app, users were sometimes shown the incorrect operating system in Okta Verify push messages.
OKTA-533753
Admins couldn't add more than 10 translations of a customized email template.
OKTA-533897
Google background service users received unrequested Okta Verify Push notifications.
OKTA-544628
Some orgs experienced internal server errors during outbound SAML federation.
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Zkipster: For configuration information, see Zkipster SCIM Configuration Guide.
SAML for the following Okta Verified applications:
-
Legl (OKTA-525334)
-
WorkOS (OKTA-527211)
OIDC for the following Okta Verified applications:
- Clearwave Scheduling: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
- Cvent: For configuration information, see the Cvent Okta Configuration Guide.
Weekly Updates
Fixes
General Fixes
OKTA-489101
Some orgs that performed multifactor authentication with the Custom OTP, Okta On-Prem MFA agent, or YubiKey OTP authenticators experienced internal server errors during outbound SAML and OAuth 2.0 authorization flows.
OKTA-513763
The Groups page showed an error when sorted with an invalid cursor.
OKTA-513767
Groups pagination incorrectly displayed a Next link when the remaining groups weren't visible due to permissions.
OKTA-521116
The End-User Dashboard Preferences didn't include appropriate accessibility values for the heading and subheading sections.
OKTA-522269
Delegated authentication was automatically checked after reenabling AD integration.
OKTA-528841
System log events for dropped emails didn't include the AppContextName.
OKTA-529450
Super admins could revoke their own admin role membership by removing a role from a group.
OKTA-538350
The Agentless Desktop Single Sign-on (DSSO) feature was incorrectly unavailable for some Okta SKUs.
OKTA-539418
Okta sign-in page didn't detect the locale correctly for Traditional Chinese (Hong Kong).
OKTA-541483
The authn_request_id field was missing from some System Log events for various authentication flows.
OKTA-542666
Admins could select an unsupported version of the Sign-In Widget on the Settings tab of Branding > Sign-in page.
OKTA-543716
Admins couldn't view the authorization server public clients that they had permission to view.
OKTA-544652
Admins couldn't enable User Enumeration Prevention when at least one Global Session Policy rule was using an Authentication Sequence.
OKTA-545007
Admins weren't able to save authentication enrollment policies that included the YubiKey authenticator in one-time password (OTP) mode.
OKTA-545162
When an end user sent an email request from the End-User Dashboard to add an app integration, the email template contained a link to a deprecated Okta Support email (support@okta.com).
OKTA-545242
For reports and the System Log, a field was improperly labeled Country rather than Country/Region.
OKTA-547483
The instructions to customize an access denied error message stated incorrectly that admins could use HTML to add links.
OKTA-554344
iFrame elements were visible on some custom sign-in pages.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Blue Shield CA (OKTA-544492)
-
Calendly (OKTA-542578)
-
Certify (OKTA-544699)
-
EmployeeNavigator (OKTA-541613)
-
OpenAir (OKTA-545505)
-
Zoom (OKTA-543469)
Applications
Application Update
The GitHub Enterprise Managed User Provisioning integration is updated:
-
The SCIM roles attribute has a new Restricted User value.
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Aon Inpoint ClaimsMonitor: For configuration information, see Aon Inpoint ClaimsMonitor application and Okta SCIM Integration Guide.
- FireHydrant: For configuration information, see User provisioning with SCIM.
- Mursion: For configuration information, see Configuring Provisioning with Okta.
- Profiles: For configuration information, see How to Configure Okta SCIM Provisioning for Profiles.
- Rootly: For configuration information, see Rootly Integrations: SCIM.
- Streamline AI: For configuration information, see How to Configure SCIM for Streamline AI.
SWA for the following Okta Verified application:
- ManageEngine SupportCenter Plus (OKTA-538460)
OIDC for the following Okta Verified applications:
- ChatFunnels: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
- Praetorian - Chariot: For configuration information, see Chariot SSO Integration: Okta Configuration Guide.
- Streamline AI: For configuration information, see How to Configure OIDC for Streamine AI.
October 2022
2022.10.0: Monthly Production release began deployment on October 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Feature
Okta LDAP agent, version 5.15.0
This version of the agent contains Security enhancements. See Okta LDAP Agent version history.
Okta RADIUS Server agent, version 2.17.6
This version of the agent contains security fixes. See Okta RADIUS Server Agent Version History.
Okta On-Prem MFA agent, version 1.6.0
This version of the agent contains security fixes. See Okta On-Prem MFA Agent Version History.
Lockout Prevention
This feature adds the ability to block suspicious sign-in attempts from unknown devices. Users who sign in to Okta with devices they’ve used before won’t be locked out. See Configure a password policy.
Non-deletable default authorization server
The default authorization server is a custom authorization server provided by Okta so that customers can quickly get started working with Okta. However, if a customer deletes the default authorization server, it can't be restored, causing confusion and disruption. This enhancement prevents you from deleting the default authorization server, although you can disable it if isn’t required. To aid in identification, Okta adds a Default label for the default authorization server in the Admin Console. See API access management.
ODSEE LDAP support
Okta now supports Oracle Directory Server Enterprise Edition (ODSEE) LDAP integrations with the upgrade to LDAP agent version 5.6.3 and later. See Oracle Directory Server Enterprise Edition LDAP integration reference.
eDirectory LDAP support
Okta now supports eDirectory LDAP integrations with the upgrade to the LDAP agent version 5.6.2 or later. See eDirectory LDAP integration reference.
Custom error message
Admins can now customize the error message that users receive when their access is denied. This allows admins to provide remediation steps and/or point users to documentation that helps resolve their access issues. See Customize the access denied error message.
Clone authentication policies
Creating an authentication policy from scratch is a manual, error-prone task because you need to visually copy existing rules into the new policy. Okta now offers the ability to clone a policy. You can use either the Admin Console or the new Clone a Policy operation on the Policy API. See Clone an authentication policy.
Dynamic routing rules
Org admins can now consolidate multiple IdP routing rules into a single dynamic routing rule. Dynamic routing rules use expression language to match users to any IdP, based on attributes of their login object. This reduces the volume and complexity of routing rules and the manual effort of managing them. See Configure dynamic routing rules.
App conditions in authentication policies
Admins can now apply an authentication enrollment policy rule to specific applications, to any application that supports MFA enrollment, or to Okta. This enables admins to configure their policies with more granularity, bringing even greater security and flexibility. This release brings this feature into parity with the functionality available in Classic Engine. See Configure an authenticator enrollment policy rule.
Enhancements
On-Prem MFA agent security provider
The On-Prem MFA agent now uses a FIPS-compliant security provider.
Generate private key in PEM format
You can now use either the PEM or JWK format for the private key when generating a public/private key pair from the Admin Console. The public key doesn't support PEM.
Enhanced SMS and Voice blocking
Additional measures are now applied to block suspicious SMS and Voice traffic from countries that are typically at risk of toll fraud attacks. Blocked transactions display a deny status in the System Log.
Email notifications for agent connection issues
Customers are now notified by email in cases of mass agent disconnect/reconnect issues.
Username match criteria
A new Organization Security setting determines how a user’s profile is matched when they sign in. Allow short match lets users sign in without their domain, while Match entire username requires the domain. See General Security.
OIN Manager enhancements
The OIN Manager landing page now includes a set of support links and a search bar to aid in integration submissions.
Improvements to API authorization server interface
Administrators working with OIDC client applications can now see a preview of the information contained in the refresh token and the device secret returned by the authorization server. See Build Custom Authorization Servers for API Access Management.
IdP logos added
Logos have been added to the existing IdPs.
Early Access Features
New Features
Passkey Management
Apple passkeys may be synchronized across multiple devices, including on unmanaged ones, and stored in Apple’s data centers. This may impact organizations whose security policies require that credentials never leave the device, or that only managed devices be allowed to connect. Okta now allows admins to block the enrollment of passkeys in their orgs. With the new Passkey Management feature, customers can ensure that security policies continue to be enforced, and potentially compromised devices can be kept from connecting. Existing passkey enrollments aren’t affected by turning this feature on.
New OIN app for Microsoft 365 GCC High
A new app is available for integrating Microsoft Office 365 Government Community Cloud (GCC) High. This Office 365 tenant type serves as a highly secure version of Office 365 built specifically for government entities, vendors, and contractors. The tenant provides built-in compliance with certifications and accreditations that are required by the U.S. public sector, including FedRAMP high-impact requirements.
With the new Okta Integration Network app, customers using the GCC High environment for Office 365 can securely deploy a consistent user experience for SSO and identity management. See Configure Office 365 GCC High Tenant.
Phishing-resistant authentication
Phishing-resistant authentication detects and prevents the disclosure of sensitive data to fake applications or websites. When users authenticate with Okta FastPass on managed devices, they’re protected from phishing attacks. See About MFA authenticators.
Enhancements
New column for the User app access report
The User app access report now includes the Recently Accessed column. This allows you to view when the user accessed the app in the last 90 days.
Fixes
General Fixes
OKTA-429940
Users were able to make unlimited attempts to activate their One-Time Password (OTP) based factors (such as SMS, CALL, EMAIL, Google OTP, and Okta Verify TOTP).
OKTA-516459
The RSA SecurId agent didn't use proxy settings during installation.
OKTA-518378
ADSSO functionality didn't working for UD, MFA, adaptive MFA, lifecycle management, and mobility management workforce.
OKTA-523494
AD-sourced users were able to sign in to Okta even when they moved out of a searchable OU.
OKTA-530753
The Help link on the Features page was incorrect.
OKTA-531308
An error message didn't appear when a deleted app instance was assigned to a role.
OKTA-532316
When a session.amr expression was used for SAML attribute statements, the attribute statement wasn't correctly populated.
OKTA-536457
AD-sourced users who reset their passwords in AD had to reset their passwords again when using IWA or ADSSO to sign in to Okta.
OKTA-537036
An inaccurate message appeared on the HealthInsights page when more rules were available to view.
App Integration Fixes
The following SWA apps weren't working correctly and are now fixed:
-
AdvancedMD (OKTA-534085)
-
Constellation Energy Manager (OKTA-532146)
-
HireRight (OKTA-536400)
-
MyFonts (OKTA-536268)
-
VitalSource Bookshelf (OKTA-529478)
Applications
Application updates
-
Coupa: OAuth/OIDC authentication is supported. API Key Authentication is deprecated for this app.
-
Google Apps: The following Google licenses have been added: Google Workspace Enterprise Starter, Google Workspace Enterprise Starter, Google Workspace for Education Fundamentals.
-
AngelPoints: Provisioning has been disabled for new AngelPoints integrations.
New Integrations
New SCIM integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Blink: For configuration information, see Blink/Okta: Set Up Guide for SCIM.
- Ivanti Neurons: For configuration information, see Ivanti Okta Authentication.
- MDScripts: For configuration information, see Configure user provisioning with Okta MDScripts app.
OIDC for the following Okta Verified applications:
- Corrata: For configuration information, see Corrata Okta Integration Guide.
- Entrustient: For configuration information, see Okta Configuration Guide.
- Foreman: For configuration information, see Foreman - Okta SSO Guide.
- Rybbon: For configuration information, see Rybbon Configuration Guide (you'll need credentials to access this documentation).
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-489052
Users received an access denied error message instead of an invalid username or password error message when signing in to an org with user enumeration prevention enabled and a global session policy set to deny access based on network zone or other criteria.
OKTA-512695
Custom app logos weren't shown correctly in a group's app list.
OKTA-514346
During the user activation flow, users were still prompted to sign in when the prompt property was set to none and the user had a valid session token.
OKTA-527228
Suspended users weren't shown on the Deactivate People page.
OKTA-530519
When an end user entered a one-time passcode (OTP) from a verification email into the Okta Sign-In Widget, pressing Enter didn't trigger the Verify action. This issue only occurred in orgs with the Email Magic Link feature enabled.
OKTA-533391
Some users received the Social transaction expired error message after successfully authenticating with the HYPR authenticator on mobile devices.
OKTA-537242
Email magic link didn't work for orgs with invisible CAPTCHA enabled.
OKTA-537408
The sign-in hint was passed to the Okta sign-in page when setting up Office 365 applications and signing in with the SP-initiated flow.
OKTA-537992
Users couldn't choose to sign in using PIV when ADSSO failed for orgs configured to use PIV.
OKTA-538996
Users on Windows devices without Windows Hello weren't able to authenticate if admins set the Lock screen condition in the device assurance policy to Password must be set and didn't select Windows Hello must be enabled.
OKTA-539396
For orgs using Active Directory delegated authentication and the Self-Service Unlock feature, when an end user with a locked AD account was removed from an AD-managed group, they could still launch an app integration assigned to that group.
OKTA-556609
When some users tried to access apps that required MFA, they were repeatedly prompted for MFA instead of gaining access to the app.
App Integration Fix
The following SWA app wasn't working correctly and is now fixed:
-
Meridian Link (OKTA-525429)
Applications
New Integrations
SAML for the following Okta Verified applications:
-
Cyber Ready (OKTA-530939)
-
Desana (OKTA-531285)
OIDC for the following Okta Verified applications:
- Clearwave Dashboard: For configuration information, see Clearwave Okta Integration.
- Josef: For configuration information, see Enable Single Sign-On with Okta (Okta Integration Network).
- Parmonic: For configuration information, see Instructions to Setup Okta SSO.
- Trova: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
Fixes
General Fixes
OKTA-491199
Orgs couldn't customize email templates if their technical contact was set to null.
OKTA-497764
On the Delegated flows page, the Filter by flow name field was labeled incorrectly.
OKTA-498519
When users were prompted for MFA to reset or recover their accounts, the Back to sign in option wasn't available. This occurred for orgs that used a custom sign-out page.
OKTA-500101
The Delegated flows page didn't have a help link.
OKTA-518536
Some token requests failed when the Groups Claim Type for the app integration was set to Expression and the number of groups matched exceeded 100.
OKTA-521634
Users were prompted to verify with Okta FastPass while attempting to enroll in Okta FastPass on a new device.
OKTA-523366
When admins added 20 users or more to an authentication policy rule, the Users field appeared blank.
OKTA-524980
Google Workspace user deprovisioning failed when Remove all G Suite licenses was selected as a Deactivations option.
OKTA-528806
The Edit resources to a standard role page displayed an Add button next to the resources that had already been added to the role.
OKTA-531605
Some access token refresh requests failed when the Groups Claim Type for the app integration was set to Expression or Filter and the number of groups matched exceeded 100.
OKTA-532293
When a user entered their credentials in the widget (version 6.6.1) during self-service registration, their information was cleared if the username didn't exist in the org.
OKTA-534847
The Back to settings option didn't appear on the sign-in page for orgs with a custom domain.
OKTA-535531
ADSSO SP-initiated sign-in attempts from SharePoint resulted in errors after upgrade to Identity Engine.
OKTA-536646
The default authentication policy for upgraded orgs contained a reauthentication frequency of 12 hours.
OKTA-537070
Some attributes were mapped incorrectly from Okta to Salesforce.
OKTA-537309
Users were prompted to verify their security question after they'd already done so earlier in the sign-in process.
OKTA-537581
The fix to the time.now function caused a NullPointerException issue.
OKTA-537929
In orgs with Phishing resistance for Okta FastPass enabled, an error occurred when admins selected Phishing resistant and Hardware protected in authentication policy rules.
OKTA-538736
Some users couldn't sign in with an external IdP after their org upgraded to Identity Engine.
OKTA-538762
NullPointerException resulted in an error for Agentless DSSO instead of failing.
OKTA-539141
The default rule in a global session policy wasn't editable.
OKTA-539219
AD users configured with non-expiring passwords were periodically warned that their passwords were going to expire and needed to be changed.
OKTA-541818
The Telephony usage report didn't show CSV export target names.
OKTA-541859
Custom app integrations didn't include the mfa and pwd factors in session.amr claims during federated sessions.
OKTA-542157
The Country/Region dropdown menu displayed incorrect labels in the SMS and Voice sections of the End-User Dashboard Settings page.
OKTA-545302
Styling issues appeared on customized sign-in pages for orgs with a custom domain.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
MoneyGram U.S. (OKTA-539829)
-
SurveyMonkey (OKTA-537617)
-
Unity (OKTA-532826)
Applications
Application Update
Fivetran provisioning integration is updated as follows:
-
Group management features are enabled for SCIM
-
SCIM FivetranRole attribute mapping is updated
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- OpsLevel: For configuration information, see Okta User Provisioning with SCIM.
- Perdoo: For configuration information, see Configuring SCIM with Okta.
- IQVIA SmartSolve: For configuration information, see the SmartSolve Administrator Guide.
- Showpad: For configuration information, see Okta user provisioning with SCIM.
SAML for the following Okta Verified applications:
-
Amplemarket (OKTA-531035)
-
Island Management Console (OKTA-539175)
-
Metaview (OKTA-536815)
-
Ox (OKTA-534114)
-
QueryLayer (OKTA-534539)
-
SmartCompany (OKTA-537534)
SWA for the following Okta Verified application:
-
ManageEngine SupportCenter Plus (OKTA-538460)
OIDC for the following Okta Verified application:
- Saltalk: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
September 2022
2022.09.0: Monthly Production release began deployment on September 6
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta ADFS plugin, version 1.7.11
This version of the plugin contains bug fixes, security enhancements, and support for an additional top-level domain. See Okta ADFS Plugin version history.
Okta MFA Credential Provider for Windows, version 1.3.7
This version of the agent contains fixes, security enhancements, and support for an additional top-level domain. See Okta MFA Credential Provider for Windows Version History.
PKCE validation for OIDC app integrations
You can now require Proof Key for Code Exchange (PKCE) as an additional verification step for any OIDC app integration except service apps. The OAuth Security Best Current Practice recommendation is to use PKCE for all uses of the authorization code flow, regardless of the client type. See Create OIDC app integrations.
Validation and verification of signed SAML requests
Using signed SAML requests ensures that incoming requests are from genuine applications. When this is configured, Okta only accepts SAML requests signed using the certificate associated with the app integration. Having signed SAML requests also resolves scenarios where the Assertion Consumer Service (ACS) URL requested after authentication can be one of several domains or URLs. When a Service Provider sends a signed authentication request, Okta can accept dynamic ACS values as part of the SAML request and posts the SAML assertion response to the ACS value specified in the request. See the Advanced Settings section of Create SAML app integrations.
Shared SWA app accounts, password restriction
For SWA apps with an account sign in option set to Users share a single username and password set by administrator, only Super admins or App admins with permissions for that app can view the password.
Device assurance for unmanaged devices
While you can secure access to your corporate resources with passwordless MFA using Okta FastPass, you can’t ensure the security posture of the device itself before granting access. This is especially true for unmanaged devices, where a complementary device management agent isn’t present to validate the compliance status of that device. Device Assurance policies enable you to define device security posture requirements that must be satisfied in order for a user to access a protected resource. This allows you to protect your organization's data and services by ensuring access is only granted to secure devices, even if those devices aren’t managed. See Device assurance.
LDAP real-time synchronization
With real-time synchronization, user profiles, groups, and group memberships can now be updated when LDAP-sourced users sign in to Okta, or when they refresh their People page. Admins no longer need to perform full or incremental imports of user attributes, and user profiles, groups, and group memberships are always up to date. Real-time synchronization also reduces the burden on system resources because user attributes are imported and updated individually and not in large groups. See Manage your LDAP integration.
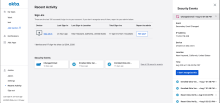
New Recent Activity page on the new Okta end-user dashboard
The Recent Activity page provides end users with a summary of recent sign-in and security events for their Okta account. End users can also report suspicious activity to their Okta admin by clicking I don’t recognize this. See Recent Activity.
Enhancements
Custom domain status
On Customizations > Domain, a new Status field indicates whether the Custom URL Domain configuration is active, pending, or certificate expired. See Customize the Okta URL Domain.
Clarified sign in widget text
The instructions on the Verify with your email page of the Sign-In Widget now specify that the end user must click the action button for Okta to generate and send the verification email.
OIN Manager user interface changes
The OIN Manager includes the following updates:
- The UI has been updated to match the current Okta style.
- The Okta logo has been updated.
- A note that lists the time required to process new submissions is displayed.
403 error for rate limit violations
When an org reaches its operational rate limit for SMS requests, a 403 Forbidden error is now displayed instead of a 429 Too many requests error. See Configure client-based rate limiting
Early Access Features
New Features
SSO apps dashboard widget
The new SSO apps widget displays the number of user sign-in events across each of your org’s apps over a selected period of time. You can use it to see which apps are used most frequently and to easily monitor the authentication activity across your org. See Monitor your apps.
Enhancements
SAML app support added for email magic links
The Email Magic Link feature now supports SAML applications for self-service registration, self-service password reset, and self-service unlock operations.
Fixes
General Fixes
OKTA-482997
The Custom Authenticator sent push notifications even when the Send push automatically checkbox wasn't selected.
OKTA-496347
The password field in the Add Person widget was incorrectly truncated.
OKTA-499408
The help link for Automatically update Okta Active Directory (AD) agents on the Early Access page pointed to an outdated help topic.
OKTA-506480
AD agent emails incorrectly indicated that agents already running the latest version had recently been auto-updated.
OKTA-515159
When an admin customized an email template not used for sign-in flows, the app.id, app.name, and app.label variables didn't resolve correctly.
OKTA-518347
Some Org2Org users had the same ExternalID on the target org.
OKTA-522912
The text in the Sign-In Widget implied that the verification code was sent in a email but Okta hadn't generated that email yet.
OKTA-523033
Inline enrollment of additional authenticators asked users to enroll authenticators based on global session policy settings.
OKTA-523140
When Salesforce provisioning was configured using OAuth, Salesforce Community Profiles weren't displayed.
OKTA-523607
Users could sign in with ADSSO after delegated authentication was disabled.
OKTA-524632
Searching for users on the Assign People page returned an Invalid Search Criteria error if the secondary email was marked as a sensitive attribute.
OKTA-529018
The catch-all rule in the default authentication policy required password only.
App Integration Fixes
The following SAML app was not working correctly and is now fixed:
-
Salesforce (OKTA-516730)
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-504222
When users signed in to apps with SWA, the Sign In To App dialog contained a typo.
OKTA-507794
User attributes that weren't mapped in the Okta to Salesforce integration were overwritten.
OKTA-510101
No error message was displayed on the Branding page when favicon uploads failed.
OKTA-514047
Unexpected routing behavior occurred when orgs with ADSSO created a PIV Identity Provider.
OKTA-516740
The origin header validation on the /token endpoint for cross-origin requests was case-sensitive, which returned an error for redirect URIs using upper-case.
OKTA-524742
Some super admins received an error when they enabled Security Notification emails.
OKTA-525344
Viewing an app target instance where the app instance was deleted resulted in an error.
OKTA-525725
Velocity Template Language wasn't supported in the custom email subject editor.
OKTA-527486
System Log events weren't logged when users attempted to access an app that they weren't assigned.
OKTA-527789
The Re-authentication frequency time range was incorrect in authentication policy rules.
OKTA-528822
An exception occurred during Agentless DSSO authentication which resulted in a 500 error.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Google apps (OKTA-529613)
-
Google Workspace (OKTA-527949)
-
QuickBooks (OKTA-525562)
-
Tenable.io (OKTA-526328)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Agora Console: For configuration information, see Log in to Agora through Okta.
- CultureHQ: For configuration information, see Configuring Provisioning for CultureHQ.
- domainIQ: For configuration information, see Single Sign-On (SSO) through Okta.
- Kintone: For configuration information, see Kintone-Okta Provisioning Guides.
- LaunchDarkly Federal: For configuration information, see Configuring Okta to Manage LaunchDarkly Federal Users with SCIM.
- Retrium: For configuration information, see Okta user provisioning integration with SCIM.
SAML for the following Okta Verified applications:
-
Legal Force (OKTA-517182)
-
MD Scripts (OKTA-525126)
-
Outage (OKTA-525313)
-
Spyderbot (OKTA-502986)
OIDC for the following Okta Verified application:
- Brex: For configuration information, see Single Sign-On (SSO) Integration.
Generally Available
Fixes
General Fixes
OKTA-484162
Admins whose custom role contained the Manage applications permission couldn't view apps with custom client IDs.
OKTA-505595
Some users of Metacompliance experienced timeouts with group push without receiving an error response.
OKTA-516161
When admins applied the Not managed filter on the Devices inventory page, some enrolled devices were missing from the list.
OKTA-518141
Imports from the Solarwinds Service Desk app to Okta failed.
OKTA-523908
The token preview interface didn't refresh when admins changed any of the values.
OKTA-524058
The Sign-In Widget displayed the identifier-first mode in orgs that used a Deny rule in the global session policy.
OKTA-524198
Single API POST calls to /api/v1/domains resulted in a concurrency rate limit notification when the token limit was set to less than 100%.
OKTA-525155
The Global Session Policy was not properly evaluated when resetting a password using Forgot Password? link on the Okta Sign-in Widget.
OKTA-529188
Some deleted app groups were visible on the groups page.
OKTA-532126
When admins customized an access denied error message, the Save button didn't work.
OKTA-532129
Push updates for Org2Org with OAuth2-based integrations failed to push non-default profile attributes.
OKTA-532394
The secondEmail attribute was returned only when it was explicitly requested, but not returned when all user attributes were requested.
OKTA-535162
Users were unable to load the browser plugin configuration page due to an internal error.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Concur (OKTA-528500)
-
Inbox by Gmail (OKTA-530128)
-
Slack (OKTA-530240)
Applications
Application Update
The Inbox by Gmail app is deprecated.
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Canva: For configuration information, see Configuring Okta provisioning for Canva.
- Money Forward IT Management Cloud: For configuration information, see How to setup SCIM (Okta Integration Network).
- SimplyMeet.me: For configuration information, see Getting started with Okta integration.
SAML for the following Okta Verified applications:
-
Canva (OKTA-517203)
-
Datto Workplace (OKTA-485785)
Generally Available
Fixes
General Fixes
OKTA-499781
An incorrect error message was displayed when a certificate with an invalid or blocked CRL location was uploaded.
OKTA-500258
When admins built a certificate chain, an internal error was displayed instead of a specific error.
OKTA-514927
Some languages appeared as decimal code in the custom email template editor.
OKTA-522887
Read-only admins weren't able to see the signing keys that were used for SAML applications.
OKTA-522911
Active Directory users experienced a password expired warning immediately after a password reset.
OKTA-523265
Persistent cookies were allowed for Okta admins.
OKTA-525507
Refined search results weren't displayed when users pasted a username in the People search box.
OKTA-526728
Some users were able to sign in with valid one-time passwords even though they were locked out of their accounts previously because they used an invalid one-time password.
OKTA-528905
When admins added a global session policy rule, the Exclude users and Identity Provider fields didn't display default values.
OKTA-532008
In the System Log, the user.session.start event displayed the wrong browser when users signed in to Okta on iPhones.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Abacus (OKTA-526877)
-
American Express (OKTA-530064)
-
Google apps (OKTA-535039)
-
Manage Engine (OKTA-529921)
-
Multiple Google apps (OKTA-530156)
-
ProTrav (OKTA-532932)
-
Slido (OKTA-530559)
-
Unity (OKTA-532826)
Applications
New Integrations
SAML for the following Okta Verified applications:
-
Flipsnack (OKTA-531284)
-
Sketch (OKTA-528798)
August 2022
2022.08.0: Monthly Production release began deployment on August 8
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Customize Okta to use the telecommunications provider of your choice
While Okta provides out of the box telephony functionality, many customers need the ability to integrate their existing telecommunications provider with Okta to deliver SMS and Voice messages.
The Telephony Inline Hook allows customers to generate one-time passcodes within Okta and then use their existing telecommunications provider to deliver the messages for MFA enrollment/verification, password reset, and account unlock using SMS or Voice. This allows customers to use their existing telephony solution within Okta, due to the time they've already invested in their existing telephony solution, the need to use a specific regional provider, or simply the desire to maintain flexibility. See Customize your telephony service provider.
Configurable API token rate limits
Admins can now configure a percentage rate-limit capacity for individual API tokens. Previously, when a token rate limit violation occurred, it wasn’t clear which token consumed the limit. Setting a maximum capacity for each token solves this problem and gives admins a new tool to investigate rate-limit violations and plan for future deployments. See API token management.
Salesforce REST OAuth
Admins can now upgrade to the latest version of our Salesforce integration. OAuth authentication will be now used for Provisioning and Imports. See Configure OAuth and REST integration. This feature is now enabled by default for all orgs.
Merge tool for duplicate authentication policies
Admins can simplify policy management by merging duplicate authentication policies. The merge tool finds authentication policies with the same rules, moves their apps to a single policy, and then deletes the duplicates. After the automated process runs, admins can then make edits and app assignments in a single policy. See Merge duplicate policies.
Custom Administrator Roles
The standard admin roles available today don’t always meet all the granular delegated administration requirements, which may result in admins having either more or less permissions than they need.
The Custom Administrator Roles feature allows super admins to:
-
Create admin assignments with granular roles, which include specific user, group, and application permissions.
-
Constrain these admin assignments to resource sets.
Use Custom Administrators Roles to:
-
Increase admin productivity.
-
Decentralize the span of access that any one admin has.
-
Grant autonomy to different business units for self-management.
Some important things to note:
-
The Administrators page has been updated with a new, more intuitive interface for managing roles and permissions. See About the Administrators page.
-
Your pre-existing roles are referred to as “standard roles”. The standard role functionality is the same as earlier but the UI is different. See Use standard roles.
-
You can continue using the pre-existing roles and your existing assignments remain the same.
-
You can also assign custom roles to users who have standard roles assigned.
See Custom admin roles and Best practices for creating a custom role assignment.
Bulk assign users to groups
Admins can now use bulk import functionality to assign multiple users to specific Okta groups. Bulk user import significantly reduces the time admins spend managing user group assignments. In addition, this functionality makes it easier for large enterprise orgs to adopt Okta as their access management provider. See Bulk assign people to a group. This feature will be gradually made available to all orgs.
Okta Admin Console Groups page enhancements
The Okta Admin Console Groups page has been updated to simplify the addition of large numbers of users to groups and reduce the likelihood that all users can be accidentally removed from a group. In addition, search functionality has been significantly improved to make adding and removing users from groups quicker and easier. See Manage groups. This feature will be gradually made available to all orgs.
Advanced search for users and groups
To make it easier for admins to quickly locate and manage users and groups, enhanced people and group search functionality is now available. Admins can limit search results to specific criteria using the SCIM protocol to query. They can also use Created On and Last Updated On in their queries to identify when users or groups were created or last modified, and search for groups and users using both base and custom attributes. These advanced search options optimize search results and help reduce the time spent searching for specific information. See View group members. This feature will be gradually made available to all orgs.
Trusted Origins for iFrame embedding
You can now choose which origins can embed Okta sign-in pages and the Okta End-User Dashboard using Trusted Origins for iFrame embedding. This feature offers a granular control over iFrame embedding compared to the existing embedding option in Customization, which doesn't let you distinguish between secure and non-secure origins. Trusted Origins under Security > API allows you to selectively configure the origins you trust. It also provides enhanced security as it uses a more secure frame-ancestors directive in Content Security Policy that protects your data from web attacks such as clickjacking. You can also migrate your existing iFrames to Trusted Origins. See Trusted Origins for iFrame embedding.
Okta AD agent, version 3.12.0
This version of the agent contains the following changes:
-
Improved group membership information logging
-
Security enhancements
Okta RADIUS Server agent, version 2.17.5
This version of the agent contains security fixes and resolves a memory leak that occurred when agents were configured for EAP-TTLS. See Okta RADIUS Server Agent Version History.
Okta On-Prem MFA agent, version 1.5.1
This version of the agent contains security fixes. See Okta Okta On-Prem MFA Agent Version History.
Event hooks for log streaming
To provide better visibility into changes in the state of Okta log streams, event logs pertaining to log stream management, such as stream deactivation, are now eligible for event hooks. Event hooks allow you to automate detection and responses to changes in the state of a log stream. See Log streaming.
Rate Limits dashboard includes API Token data
The Rate Limits dashboard now includes API Token data on the Rate limit usage over time graph. You can view bar graph data from API tokens or by IP address to review any spike in traffic. See bar graph and API rate limits by token.
Enhancements
System Log events for Report CSV actions
For enhanced security and auditing, the System Log now records new events when CSVs of reports are requested, generated, and downloaded.
System Log update for authentication policy
Authentication policy update events include a new DebugData field with details about how the rule was changed.
System Log update for telephony operations
The system.operation.rate_limit.violation event is no longer fired when SMS or Voice messages are blocked due to telephony operational rate limit violations. Instead, telephony system.sms.send.* and system.voice.send.* events are issued as a DENY System Log message.
Microsoft Azure Join documentation
Help documentation is now available for users integrating Azure Join and Okta. See Typical workflow for integrating Hybrid Azure AD Join.
AD Agent auto-updates only when operational
The AD agent auto-update scheduler no longer automatically updates non-operational agents. See Schedule agent auto-updates.
The YubiKey authenticator renamed
The YubiKey authenticator is renamed YubiKey OTP. See Configure the YubiKey OTP authenticator.
OIN Manager enhancements
The contents of the automated email sent when an integration has been moved to Draft after a period of inactivity have been updated.
Dynamic issuer mode for identity providers
You can configure the dynamic issuer mode for an identity provider using the Identity Provider API. When you set issuerMode to DYNAMIC, Okta uses the domain from the authorizeURI as the domain for the redirect URI when returning the authentication response.
Clock skew requirement removed
Users can now access the End-User Dashboard without syncing their device clock to the server time. See End-user experience.
Early Access Features
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-454135
The pending user action status was unclear on the new group membership page.
OKTA-466964
The Edit icons on the Application > Provisioning tab were visible to admins who didn't have the Manage applications permission.
OKTA-492931
Admins couldn't edit the MFA requirement and session expiration settings in the default rule of a global session policy.
OKTA-494505
Okta Expression Language worked incorrectly in app pages after the page was saved and reloaded.
OKTA-505852
AD agents running versions prior to 3.8.0 were displayed in existing auto-update schedules.
OKTA-508762
Workday incremental imports with a pre-hire level set prematurely picked up some updates from within the pre-hire interval.
OKTA-509105
Upgrading to Identity Engine resulted in AWS Redshift connectivity issues.
OKTA-509671
When a custom admin role was deleted, users with no other assigned admin roles could still see the Admin button on the Okta End-User Dashboard.
OKTA-511909
When admins applied the Not managed filter on the Devices inventory page, some unmanaged devices were missing from the list.
OKTA-511933
LDAP agents failed to parse queries when group names had special characters.
OKTA-512433
On the Admin Dashboard, the Items count for the Applications can be updated to use SAML task wasn't correct.
OKTA-515783
Sometimes, in the Groups page Description column, an equals sign (=) replaced the forward slash ( / ) in LDAP-sourced group names.
OKTA-518090
The Authentication Policies page didn't load if a policy name contained an apostrophe.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Accredible (OKTA-511942)
-
SurveyMonkey (OKTA-509109)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Talking Talent: For configuration information, see Okta Configuration Guide for Talking Talent.
OIDC for the following Okta Verified applications:
- Doccly Lender: For configuration information, see the Okta Integration Guide.
- Mux: For configuration information, see How to set up an Okta Single Sign-On integration for Mux.
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-493980
The OK button on the post-import screen didn't work after AD imports were completed.
OKTA-499402
Some AD users couldn't be confirmed and activated using the Create Users API.
OKTA-516724, OKTA-517915
If an end user didn't select the checkbox for a required boolean attribute on the self-service registration form, they received an error. If the attribute was optional and the end user didn't select the checkbox, the user was created with the attribute value set to false.
OKTA-518622
The Office 365 app sometimes failed to save Sign On tab changes in WS-Federation Auto mode, when multiple domain federation was enabled.
OKTA-518709
On the Device integrations page, the AAD tenant in the delegated SCEP configuration details was mislabeled AAD secret.
OKTA-521207
The Security Events section on the Recent Activity page became unresponsive if user agent information was missing from event logs.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
SurveyMonkey (OKTA-517783)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Juro: For configuration information, see the Juro SCIM Configuration Guide.
SAML for the following Okta Verified applications:
-
Plumm (OKTA-472978)
-
RecruitBot (OKTA-520397)
-
Talking Talent (OKTA-501296)
Generally Available
Fixes
General Fixes
OKTA-482997
Custom push notifications were sent even though the Send push automatically option was cleared.
OKTA-497457
On the Enrollment tab of the Authenticators page, the authenticator enrollment policy was incorrectly labeled as multifactor enrollment policy, and the Add a policy button was incorrectly labeled as Add Multifactor Policy.
OKTA-507358
Admins received an error when they tried to delete an authentication policy with no apps assigned to it.
OKTA-507957
When admins added a fromURI to the sign-out flow, users were still redirected to their dashboard.
OKTA-508490
Okta Verify push notifications originating from Okta RADIUS agent version 2.17.4 displayed the RADIUS server's location instead of the user's (client) location.
OKTA-516184
Devices were enrolled in Okta Verify even if the user scanned the QR code after its expiration.
OKTA-518573
Admins whose custom role only contained the Edit application's user assignments permission couldn't view the Application page for OIDC apps.
OKTA-520325
Users couldn't enroll in the Custom Authenticator if the FIPS compliant devices only option was enabled in their org.
OKTA-520653
An error message appeared when admins attempted to upload the Symantec VIP certificate on the Symantec VIP Settings page.
OKTA-521640
The Contact your administrator message wasn't displayed on custom error pages.
OKTA-522376
On the End-User Dashboard, users couldn't close an app drawer by clicking the menu on the app tile.
OKTA-526305H
An error occurred when running scheduled profile sync jobs for provisioned apps.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Blackblaud (OKTA-516841)
-
Bloomberg (OKTA-517367)
-
The Hartford EBC (OKTA-521645)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- FiveTran: For configuration information, see Fivetran SCIM configuration guide for Okta.
- Island: For configuration information, see Island Configuration Guide (you'll need Island permissions to access this documentation).
- Observe: For configuration information, see Observe + Okta | SCIM Instructions.
- Smartsheet: For configuration information, see Directory integration with Okta.
SAML for the following Okta Verified applications:
-
Island (OKTA-508653)
-
Money Forward IT Management Cloud (OKTA-520399)
Generally Available
Fixes
General Fixes
OKTA-409804
Users were able to change the primary and secondary email address in the User Profile settings without satisfying an MFA challenge.
OKTA-474140
When an admin added a custom SMS translation that exceeded the maximum character length, the list page displayed the newly added translation even though the API request failed. After the page was refreshed, this newly added translation disappeared.
OKTA-485674
App-level roadblocks weren't triggered for AD instances when org-level roadblocks were disabled.
OKTA-499602
Despite having insufficient permissions, a report admin was able to use the Mappings API to edit the UD mappings for an Identity Provider configured in Okta.
OKTA-502227
Imported passwords with a malformed bcrypt hash format caused an error during the password reset flow.
OKTA-505861
App user lists weren't updated on the page after they were edited and saved.
OKTA-509216
In SAML sign-in flows, routing rules didn't automatically redirect users to an external Identity Provider based on the login hint.
OKTA-517168
SAML IdPs and certificates weren't displayed properly in the Admin Console.
OKTA-517781
Office 365 roles weren't properly provisioned in Okta for some users in AD groups.
OKTA-520158
The sign-in page became unresponsive if users entered the same incorrect credentials twice.
OKTA-522531
Okta didn't verify location information for network zone validation when users signed in.
OKTA-523031
Users were redirected to a fromURI that wasn't configured as a trusted origin redirect.
OKTA-523541
Shared authentication policies weren't upgraded if an Office 365 app was created after an org started to upgrade but before Identity Engine was fully activated.
OKTA-525242
When admins applied the Not managed filter on the Devices inventory page, some managed devices were erroneously included in the list.
OKTA-527939H
A Deny All authentication policy was sometimes erroneously applied to the Okta Dashboard app during org creation, which prevented users from signing in.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Ray Wenderlich (OKTA-524067)
-
Team Grantt (OKTA-522984)
-
Travelers Insurance (OKTA-518696)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- CloudGate: For configuration information, see How to configure SCIM for CloudGate.
- Grayscale: For configuration information, see Okta SCIM Guide for Single Sign-On.
- LUSID: For configuration information, see Provisioning LUSID using Okta and SCIM.
- Wayleadr: For configuration information, see SCIM Integration with Okta.
SAML for the following Okta Verified application:
-
LUSID (OKTA-524169)
OIDC for the following Okta Verified application:
- BeyondTrust Privilege Management Cloud - Windows and Mac: For configuration information, see BeyondTrust Add PMC Instance to Okta.
July 2022
2022.07.0: Monthly Production release began deployment on July 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Server-generated secret keys lengthened
Server-generated secret keys have been lengthened to enhance security. These keys are used to generate one-time passwords for multifactor authentication in FIPS-enabled environments and orgs.
Introducing the Progressive Enrollment experience
Typically, collecting end-user data during the initial sign-up process creates friction and abandonment. The addition of the Progressive Enrollment feature helps you to capture the minimum user information required to create a profile and then expand and enhance those user profiles during subsequent sign-in operations. Admins can control what information is collected, validate those input values, and trigger inline hooks during the self-service registration and progressive enrollment flows. See Registration of end users.
Password synchronization for LDAP-sourced users
When the passwords of LDAP-sourced users are reset in Okta and LDAP delegated authentication is enabled, the new password is now immediately synchronized to the user's assigned applications that are configured for password synchronization. This change makes sure that user passwords remain current and reduces the likelihood that users will be unable to access their applications. See Application password synchronization.
Configure sign-on policies based on identity providers
Admins now have the option to configure a sign-on policy based on a specific identity provider. This allows admins more flexibility to dictate which IDP can be used to obtain an Okta session. See Add an authentication policy rule.
Additional detail now provided on the Sign-In Widget
The Verify it’s you with a security method page on the Sign-In Widget now indicates whether a security method is used for authentication, recovery, or both.
Remember my last-used MFA authenticator
Okta now remembers all MFA authenticators that the user selected the last time they successfully signed in. On subsequent sign-in attempts, the last-used authenticator is automatically selected by default. Users can still select another authenticator by clicking Verify with something else. This feature will be gradually made available to all orgs.
SSO capability to OIN apps
Customers who subscribe to the MFA-only package of services now have basic single sign-on functionality to Okta Integration Network apps.
Legacy user group ID support
Validation rules have been relaxed to support user group entity legacy ID formats created prior to 2012.
FIDO2 security key enrollment
Admins may now enroll a FIDO2 security to a user’s account, on their behalf, from the Okta user interface. This enables admins to provide extra levels of assistance in the event that a user is unable to complete the enrollment themselves. See Configure the FIDO2 (WebAuthn) authenticator.
New catch-all rule conditions
The catch-all rule in new authentication policies now allows access with any two factor types and requires re-authentication after 12 hours. See Add a global session policy rule.
OIN Manager developer terms
OIN Manager pages now include links to developer terms and conditions. See Developer Terms.
Enhancements
Session management section for adding a global session policy rule
A new Session management section is available when adding a new global session policy rule or editing an existing one.
The section includes two new options:
-
Maximum Okta session lifetime: Set time limit for user sessions.
-
Persist session cookies across browser sessions: Allow the user to continue a session after reopening a closed browser.
These options were previously only available through the Okta API, but now they can be configured from the Admin Console also.
Session Expires After is now renamed Expire session after user has been idle on Okta for.
Additional warnings and descriptions clarify the functionality of the fields and how to better configure them.
User.session.start System Log events
A user.session.start System Log event is fired after successful app-specific DelAuth sign-in events.
Default policy new conditions
The default authentication now allows access with any two factor types and requires re-authentication after 12 hours. See Add an authentication policy rule.
Default policy name change
For new and upgrading orgs, the default authentication policy has been renamed Any two factors. This policy allows access with any two factor types and requires re-authentication after 12 hours. See Preset authentication policies.
OIN App Catalog user interface changes
The Languages Supported section of the app details page has been removed.
Improvements to API authorization server interface
Administrators working with OIDC client applications can now see a preview of the information contained in the refresh token and the device secret returned by the authorization server. See API access management.
Updated System Log event
The authenticatorKey data now appears in the System Log when an authenticator is created, updated, activated, or deactivated.
New HealthInsight security task
A new MFA Requirements task appears if admins set up a global session policy with New Device behavior but don't select At every sign-in.
The purpose of this security task is to ensure that the MFA requirements configured by the admin aren’t in conflict with Okta’s Behavior Detection functionality, and that the MFA policy rule isn’t bypassed unintentionally. When users select the security task, recommendations appear for correcting the configuration. See MFA requirements
Organization settings name change
The Organization section of the Security > General page is renamed Organization Security. See General Security.
Early Access Features
New Features
Improvements to the self-service registration experience
Earlier versions of the self-service registration (SSR) flow used a complicated array of templates to send activation emails to end users. The simplified SSR flow reduces this to only two email templates with customized welcome messages. If your application requires immediate verification of the end user’s email address, Okta uses the Registration - Activation template. This template includes a magic link for a smoother sign-in experience. If email verification isn't immediately required to sign in to the application, Okta uses the Registration - Email Verification template. This template includes a link for end users to complete email verification at any time after they successfully sign in to the application. See Customize email notifications and the Okta email (magic link/OTP) integration guide.
Fixes
General Fixes
OKTA-449159
In the Add Identity Provider - Microsoft UI, the Microsoft Scopes help link pointed to an incorrect URL.
OKTA-480772
AD-sourced users who reset their passwords in AD had to reset their passwords again when using IWA or ADSSO to sign in to Okta.
OKTA-498957
When configuring SAML signing certificates for a SAML 2.0 app, admins were unable to right-click and copy the Identity Provider metadata link in the Admin Console.
OKTA-500367
Unique properties associated with non-existent users weren't cleared when user validation failed during user creation.
OKTA-502678
Users who enrolled Okta Verify on multiple devices and clear the Send push automatically checkbox didn't receive a push notification when they selected Get a push notification.
OKTA-506002
Since uniqueness requires exact value matches, making schema properties of type Number unique was an issue and is no longer supported. Use Integer or String properties instead.
OKTA-506333
Warning messages appeared on the Global Session Policy - Add Rule and Edit Rule page even though the relevant fields weren’t visible.
OKTA-507888
On the Pages panel of Customizations > Branding, the Okta defaults appeared instead of an org's selected theme.
OKTA-509079
The Welcome page, SMS reminder prompt, and security image prompt weren't shown for users who accessed Okta using AD SSO in Incognito mode.
OKTA-510254
The profile enrollment form didn't permit more than 10 allowed attributes.
OKTA-510483
Sometimes an error occurred when an admin attempted to edit a resource set that included a deleted app.
OKTA-515057H
Clicking the Force Sync button resulted in a 404 error with an incorrect message.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
GetFeedback (OKTA-505764)
-
GoToWebinar (OKTA-502955)
-
NordLayer (OKTA-505977)
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-500649
Sometimes Identity Engine users couldn't sign in using the Classic Engine /authn API.
OKTA-511954HF
Refreshing the LDAP schema attribute list ignored CaseIgnoreString type attributes from AD LDS.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
QuickBooks (OKTA-508237)
Applications
New Integrations
New SCIM Integration application
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Millie: For configuration information, see Provisioning Setup - Okta.
Generally Available
Fixes
General Fixes
OKTA-465268
Sometimes, the session object was missing in the payload sent to a token hook.
OKTA-472638
Operations that assigned custom roles to a user or group and included a nonexistent resource returned an HTTP 500 Internal Server Error.
OKTA-478496
LDAP incremental imports were converted to full imports when the wrong ModifyTimestamp was set.
OKTA-481255
To check user status, Okta had to connect to Active Directory too frequently.
OKTA-482003
After an org upgraded to Identity Engine, users accessing a SAML application weren't redirected to an IdP if the routing rule looked for data in a login_hint.
OKTA-496351
When an admin selected a customized display language, some text on the Admin Dashboard was misaligned and some links remained untranslated.
OKTA-498010
Some users were unable to authenticate with an external IdP on an iPad.
OKTA-500540
Some admins couldn't add Velocity macros to their custom email templates.
OKTA-500633
The Sign-In Widget indicated that Okta Verify could be used for access and recovery even though Okta Verify Push was disabled for recovery.
OKTA-502195
The formatting for the last updated timestamp was inconsistent on the Email and Error pages code editors.
OKTA-508008
Authentication policy UI strings were inconsistent in read and edit views.
OKTA-509046
IP addresses weren't rendered correctly when users clicked See All on the Networks page.
OKTA-509722
The dropdown menu that appears when an admin clicks their username wasn't aligned properly.
OKTA-513592
In some Preview orgs, admins couldn't successfully generate password health reports.
OKTA-514634
The layout of the Error pages code editor was inconsistent with other code editors.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
Meetup (OKTA-513999)
Applications
Application Updates
-
The BombBomb OIDC integration is updated to use the following URLs:
-
Additional Redirect URI: https://auth.bombbomb.com/login/callback
-
Post Logout Redirect URI: https://app.bombbomb.com/app/index.php?actn=logout
-
-
The Airtable SCIM integration is updated to support Push user updates. See How to manage users via IdP sync - ELA only for more info.
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Plumm: For configuration information, see Configuring Provisioning for Plumm.
SAML for the following Okta Verified applications:
-
iCIMS Talent Cloud (OKTA-507875)
-
NexTraq (OKTA-454943)
-
Torq (OKTA-511525)
-
Vanta (OKTA-514567)
June 2022
2022.06.0: Monthly Production release began deployment on June 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Hyperdrive agent, version 1.2.0
Okta for MFA provides more security for Electronic Prescribing for Controlled Substances (EPCS) clinician flows when using the Epic Hyperdrive platform. This plugin is compatible with both Classic Engine and Identity Engine orgs (EPCS clinician flows for customers still using the deprecated Epic Hyperspace platform aren't supported on Identity Engine). See MFA for Electronic Prescribing for Controlled Substances - Hyperdrive and Okta Hyperdrive agent version history.
Okta LDAP agent, version 5.13.0
This version contains:
-
An upgraded version of Amazon Corretto
-
Security fixes
-
Improved handling of exception in poller thread
-
Bug fixes
This agent will be gradually made available to all orgs.
JIRA Authenticator Toolkit, version 3.1.9
This version contains:
-
Support for Jira 8.22.2
-
Bug fixes
Okta Browser Plugin, version 6.10.0
This version includes the following fixes:
- Some elements weren't accessible in the Okta Browser Plugin Change password dialog.
- The Okta Browser Plugin briefly displayed a prompt when users opened SWA apps from the dashboard.
Expose groups in the LDAP interface directory information tree (DIT)
To simplify access control decisions for their orgs, admins can now select the groups they want to expose in the LDAP interface directory information tree (DIT). In addition to Okta groups, admins now have the option to view the application groups that are significant to their orgs, including Active Directory (AD) and LDAP groups. See Expose app groups in the LDAP interface directory information tree.
Symantec VIP authenticator now available
The Symantec VIP authenticator is now available in Okta Identity Engine. Enterprises that use Symantec VIP to verify their users’ identities may now integrate this authenticator into their Okta environments and use it to protect access to their Okta orgs and apps. See Configure the Symantec VIP authenticator.
Password as optional authenticator
Passwords are weak authenticators and prone to security issues. Currently all users are required to enroll a password. This also causes friction during the self-service registration process. You can now create a password-optional or passwordless sign-in experience for your end users. It makes the registration process quicker by removing the need to set up a password. It also provides a safer and more secure sign-in experience as users can instead use stronger authenticators such as possession-based authenticators or biometrics. Okta gives you the flexibility to target specific groups of users in your organization with passwordless flows, allowing you to gradually roll out the experience across your entire user base. See Set up passwordless sign-in experience.
Improved email magic link authentication experience
Email magic links have been enhanced to allow end users to authenticate in two different contexts. They can authenticate in the same location where they click the link and quickly return to the application context. Or, if the end user clicks the link in a different browser, they can enter a one-time password to proceed with authentication. Previously when using email magic links to sign in to an application, end users had to return to the original browser location where they initiated the sign-in attempt. Okta ensures that end users can prove ownership of both the originating tab and the tab where they clicked the email magic link. See Configure the Email authenticator and Sign in to resources protected by Okta.
Enhancements
New System Log events
Two new System Log events track when a new authenticator is created and when an existing authenticator is updated:
-
security.authenticator.lifecycle.create: This event is recorded when an admin creates a new authenticator for the org. It can be used to identify who created an authenticator and which authenticator was created. The actor specifies the user who created the authenticator and the target specifies the authenticator name and the ID. This event may also contain some authenticator-specific information.
-
security.authenticator.lifecycle.update: This event is recorded when an admin updates an authenticator in the org. It can be used to identify who updated an authenticator and which authenticator was updated. The actor specifies the user that updated the authenticator and the target specifies the authenticator name and the ID. This event may also contain some authenticator-specific information.
System Log events for telephony rate limit violations
Telephony system.sms.send.* and system.voice.send.* events are now issued with a DENY System Log message when SMS or voice messages are blocked due to telephony operational rate limit violations. The system.operation.rate_limit.violation event is still fired but will be deprecated in the 2022.08.0 release.
See System Log.
Enhancements to the base OIDC IdP connector
The generic OpenID Connect (OIDC) identity provider (IdP) connector offers PKCE as an additional verification mechanism. You can also define a regular expression to match Okta usernames when authenticating through this connector. See Create an Identity Provider in Okta.
OIN Manager user interface changes
The OIN Manager includes the following updates:
-
The App categories field has been renamed to Use cases to be consistent with the OIN catalog.
-
Single Sign-On is the default use case.
JWT claim enhancement
For custom JSON Web Token (JWT) claims, the name portion now supports the URI format, including the slash and colon characters. Any name containing a colon character must be a URI.
System Log enhancement for inline hook types
The inline hook type is now included in the debug data for a System Log debug context event.
Unique names enforced for custom admin roles
When a super admin creates a custom admin role with a duplicate role name, the following error message now appears: There is already an admin role with this name. See Custom admin roles.
Improved text for resource set constraints
On the Create new resource set and Edit resource set pages, the Constrain to all check box labels now include the selected resource type (Constrain to all groups, for example). See Work with the resource set component.
User interface label change
The Device Bound checkbox label on the Authentication Policy Add Rule modal has been changed to Exclude phone and email authenticators. See Add an authentication policy rule.
Additional detail now provided on the Sign-In Widget
The Verify it’s you with a security method page of the Sign-In Widget now displays the name of the app under each security method listed.
User interface help text changes
Enhancements to the help text on the Identity Provider pages align with product changes and improve user experience. See Identity Providers.
User Activation template update
Admins can now add the fromURI to the User Activation email template. This enables user activation from any registered OIDC app in the org.
Help menu updates
In the global help dropdown menu, help links are renamed and now contain resource descriptions.
Global session policy UI updates
UI strings for the global session policy’s authenticator requirements were updated. SeeAdd a global session policy rule.
Policy condition text changes
Enhancements were made to the multifactor authentication items on the Global Session Policy Add Rule modal to improve user experience. See Add a global session policy rule.
Revised error message for password policy rule updates
Admins now see a clearer error message if they attempt to require additional verification in a password policy rule in which the Email, Phone, or Okta Verify authenticator are used for recovery and no other authenticators are enabled.
Early Access Features
New Features
Run delegated flows from the Admin Console
With delegated flows, admins can be assigned the ability to run Okta Workflows directly from the Admin Console. Flows that are delegated to an admin appear on the Delegated Flows page where they can be invoked without signing in to the Workflows Console. This gives super admins more granular control over their admin assignments. See Delegated flows.
Fixes
General Fixes
OKTA-471339
Creating a new LDAP integration from the App Catalog resulted in a Resource not found error.
OKTA-479711
When a user added or removed from a group with a custom admin role, the System Log displayed a Grant user privilege event.
OKTA-480925
Admins didn’t receive timely email notifications when users locked themselves out of their accounts.
OKTA-482826
Some users imported from Active Directory were stuck in one-time password mode if they were activated more than once.
OKTA-488912
When a super admin searched for a group on the Edit resources to a standard role page, the search results didn’t appear until the admin typed in at least three characters.
OKTA-489049
When admins clicked the Tasks tab on the End-user Dashboard, the page took too long to load and the web browser became unresponsive if there were a large number of entitlements.
OKTA-491194
Deleting a custom attribute created a job that consistently timed out for orgs with a large number of users.
OKTA-491583
When using an OIDC app with refresh tokens, clients could obtain an access token through an existing refresh token if the user consent to the offline_access scope was revoked.
OKTA-493059
Admins couldn't upload certificate chains in tree format.
OKTA-493075
The Admin Role Assignments report sometimes included duplicate records.
OKTA-493119
Some users who attempted to sign in through an external IdP received a rate limit error and couldn't return to the sign-in page.
OKTA-496025
The Delete dialog in the LDAP interface was missing a question mark.
OKTA-497934
The Group Search endpoint didn't reflect the last membership update.
OKTA-498383
Some read-only admins could edit policy assignments.
OKTA-501623
Simultaneous user profile updates and deactivations sometimes resulted in a permanent DEACTIVATING status for the user.
OKTA-501729
When an admin created a new user with the User must change password on first login option selected, the user's status was mistakenly set to ACTIVE instead of PASSWORD_EXPIRED.
OKTA-502404
Users couldn’t temporarily sign in if their org subdomain was changed.
OKTA-502620
In Assign People, users who were removed from the permitted group were still available.
OKTA-503017
On the Profile Enrollment page, admins could delete the Default Policy. After refreshing the page, the default profile enrollment policy was restored, but attempting to edit that policy resulted in a blank page.
OKTA-503377
Users could use ADSSO to sign in to Okta when delegated authentication was disabled.
OKTA-503378
Users could continue to use the Okta IWA Web agent to sign in to Okta when delegated authentication was disabled.
OKTA-503715
The file sizes and hash values displayed on the Downloads page for the Linux RADIUS installers were incorrect.
OKTA-505960H
Admins who clicked the Resources > Help Center link from the Admin Console weren’t automatically signed into the Okta Help Center.
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Rivet: For configuration information, see How To Configure Okta SSO with Rivet.
SAML for the following Okta Verified applications:
-
Briq (OKTA-495218)
-
Uber for Business (OKTA-499842)
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-398717
End user input values weren't properly escaped in some fields of the self-service registration form.
OKTA-479211
The Settings page displayed an error message when users removed Okta Verify from the Extra Verification list, even though the removal was successful.
OKTA-480064
The ADSSO login flow resulted in a 403 error when initiated on the default URL if a vanity URL was configured.
OKTA-480442
The Max Okta session lifespan setting for Global Session Policy was ignored.
OKTA-487409
When the maximum number of trusted origins with iFrame embedding was reached, the limit wasn't displayed in the Admin Console.
OKTA-488510
Admins and developers couldn't add a role=“presentation” attribute to the HTML table tag for custom email templates. This caused accessibility issues for screen readers.
OKTA-492197
The messages explaining the Registration Activation email template were incorrect.
OKTA-494008
Long group descriptions weren't displayed properly on the Edit resources to a standard role page.
OKTA-494490
Password health reports couldn't be generated if user sign-in data was missing.
OKTA-495068
For non-English locales, some buttons were misaligned.
OKTA-496486
Admins couldn't change the Okta domain field on an OIDC custom app instance's General tab. This field was read-only by design but caused confusion during custom domain creation.
OKTA-499597
When token inline hooks were used in embedded flows, the hook request URL didn't contain the complete path. When token inline hooks were used in redirect flows, the hook request didn't always contain the user object.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
iCloud (OKTA-500366)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Common Room: For configuration information, see OKTA SCIM Setup guide.
- Oracle Cloud Infrastructure IAM: For configuration information, see User Provisioning from Okta to Oracle Cloud Infrastructure IAM.
- Teampay: For configuration information, see Teampay documentation, here (you need Teampay credentials to view this doucmentation).
- Vault: For configuration information, see SSO setup OKTA - SCIM integrations.
SAML for the following Okta Verified application:
-
Agora (OKTA-500061)
Generally Available
Fixes
General Fixes
OKTA-484374
The error message for the Create Users API contained unnecessary information.
OKTA-494619
If an admin modified the credentials for an OAuth client that used a client secret or a JSON Web Key (JWK), the System Log didn’t record the event.
OKTA-497143
The Admin Roles Assignments report was called Custom Admin Roles report in the report email and CSV file.
OKTA-499267
In apps that required registered devices, users were denied access if they canceled their sign-in attempt when prompted for verification.
OKTA-503545
Users weren’t able to delete an authenticator when a password policy required multifactor authentication for self-service reset.
OKTA-505147
The fromURI app link in User Activation messages didn’t work.
OKTA-506333
Warning messages appeared on the Global Session Policy - Add Rule and Edit Rule page even though the relevant fields weren’t visible.
OKTA-506570
After admins disabled the Recent Activity Early Access feature, users who accessed the https://org-name.okta.com/enduser/recent-activity page received a 404 error instead of being redirected to the home page.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
eVerify (OKTA-502426)
-
Orion Advisor (OKTA-503428)
Applications
New Integrations
SAML for the following Okta Verified application:
-
Vault Platform (OKTA-502036)
Generally Available
Fixes
General Fixes
OKTA-490308
Read-only admins were unable to view IdP details.
OKTA-504696
Long role names weren't displayed properly on the Administrators > Admins tab.
OKTA-504710
ThreatInsight reported sign-in attempts from IP addresses that weren't blocked as a threat and generated unnecessary MFA challenges.
OKTA-505471
IdP routing rules didn't work with the webfinger API.
OKTA-507188
When a create user API request failed due to non-compliant user credentials, the Add user to application membership events were listed incorrectly in the System Log.
OKTA-508174
The edit menus on the Branding page were misaligned.
Applications
Application Update
The Australian Access Federation application integration is removed from the OIN Catalog.
New Integrations
SAML for the following Okta Verified application:
-
Time By Ping (OKTA-493080)
May 2022
2022.05.0: Monthly Production release began deployment on May 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta AD agent, version 3.11.0
This version of the agent contains the following changes:
-
Increased minimum .NET version supported to 4.6.2. If the installer doesn't detect .NET 4.6.2 or higher, it won't be installed.
-
Security enhancements
-
Removed unsupported libraries
Okta ADFS plugin, version 1.7.10
This version of the plugin contains bug fixes and security enhancements. See Okta ADFS Plugin version history.
Okta RADIUS agent, version 2.17.4
This version of the agent contains bug fixes and security enhancements. See Okta RADIUS Server Agent Version History.
Okta On-Prem MFA agent, version 1.5.0
This version of the agent contains security enhancements. See Okta On-Prem MFA Agent Version History.
Jira Authenticator, version 3.1.8
This release contains bug fixes. See Okta Jira Authenticator Version History.
Okta Resource Center access
The Okta Resource Center is a collection of product tours, step-by-step guides, and announcements that helps you learn about new features and how to perform tasks within the Admin Console. You can launch the Okta Resource Center by clicking the blue icon from anywhere in the Admin Console. See Okta Resource Center.
Use Okta MFA for Azure AD Conditional Access and Windows Hello for Business Enrollment
You can use Okta MFA to:
- Satisfy Azure AD Conditional Access MFA requirements for your federated Office 365 app instance.
- Enroll end users into Windows Hello for Business.
Sign-In Widget enhancements for self-service password reset and default registration page
Okta has enabled the self-service password reset function for embedded authorization on all new and upgraded Identity Engine orgs. For integrations using embedded authentication, client applications can now use a recovery token when launching the Sign-In Widget to start the recovery flow. In addition, a new endpoint at /{orgurl}/signin/register gives you the ability to point your Sign-In Widget directly to the registration page for default applications.
Client secret rotation and key management
Rotating client secrets without service or application downtime is a challenge. Additionally, JSON Web Key management can be cumbersome. To make client secret rotation a seamless process and improve JWK management, you can now create overlapping client secrets and manage JWK key pairs in the Admin Console. You can also create JWK key pairs from the admin console without having to use an external tool. See Manage secrets and keys for OIDC apps.
Personal Identity Verification
Personal Identity Verification is now supported on Okta Identity Engine. See Add a Smart Card IdP.
Okta API access with OAuth 2.0 for Org2Org
Previously, the Org2Org integration only supported token-based access to the Okta API. You can now configure the Org2Org integration to access the Okta API as an OAuth 2.0 client. This increases security by limiting the scope of access and providing a better mechanism to rotate credentials. See Integrate Okta Org2Org with Okta.
Enhancements
Custom help links in the Sign-In Widget
Admins can add a custom help link on the authenticator page of the Sign-In Widget. This link can provide just-in-time help with multifactor authentication and can point to an in-house resource or other location. See Customize text on your sign-in page.
PKCE is a verification method for OIDC SPA and Native app integrations
The OIDC App Integration Wizard now identifies that PKCE is not a client authentication method. Instead, for SPA and Native apps, the AIW creates apps listing PKCE as a verification method. See Create OIDC app integrations.
Add agent permissions to custom admin roles
Custom admins can perform AD agent auto-updates for AD instances they have access to. They can also view the agents dashboard page to see the statuses of all agents associated with app instances they can manage. See Automatically update Okta Active Directory agents.
Group count tooltip on the Admin Dashboard
On the Admin Dashboard, the Overview section now provides an "Includes only Okta sourced groups and excludes those sourced externally, such as AD groups" tooltip for the Groups count. The new tooltip helps you understand how your groups count is calculated. You can view the tooltip by hovering your cursor over the Groups count on the Overview section. See View your org at a glance.
Okta End-User Dashboard enhancements
-
Unread notifications are more visible to users.
-
The End-User Dashboard Preview function bar has moved to a separate dialog. See Preview an end user's dashboard.
-
The Last sign in link at the bottom of the Okta End-User Dashboard now includes the entire text of the message in the hyperlink.
-
The title of the copy password dialog in the Okta End-User Dashboard is more specific.
System Log enhancements for block zone events
-
The zone.make_blacklist event in the System Log now encompasses two actions: when an admin creates a blocked network zone, and when an admin marks an existing blocked zone as unblocked. Previously, this event was only recorded when a pre-existing network zone was converted into a block list.
-
The zone.remove_blacklist System Log event now encompasses two actions: when a network zone is converted into an allow list, and when an admin deletes a blocked zone. Previously, this event was only recorded when a pre-existing network zone was converted to an allow list.
System Log enhancement for network zone events
A network zone ID is now added as a target for all network zone events in the System Log.
Enhancements to ThreatInsight
ThreatInsight is improved to further protect rate limit consumption from malicious actors. Requests from actors with a high threat level continue to be logged and/or blocked depending on the org's configuration. Now, additional requests that seem malicious but have a lower threat level no longer count towards org rate limits.
Enhancements to multifactor authentication validation in authentication policies
When creating authentication policies, admins can only select authenticators that are enabled in their org and available to the associated group of users.
OIN Catalog enhancements
Integrations in the OIN Catalog help end users address issues across a variety of industries. Okta has added the ability to filter integrations by industry to help both prospective and current Okta users identify the OIN integrations that best meet their needs. Additionally, the OIN Catalog interface has been updated with the following enhancements for improved navigation:
-
The search interface has been updated and popular search terms can now be selected.
-
Details pages for integrations have been updated for usability.
-
Navigation breadcrumbs have been added to the OIN Catalog.
-
Integrations can now be sorted alphabetically and by recently added.
OIN Catalog search functionality and filter updates
-
OIN Catalog search results now prioritize complete word matches from the search phrase.
-
Integrations in the OIN Catalog can now be filtered by RADIUS functionality.
OIN Manager enhancements
The OIN Manager now requires that ISV submissions for SCIM integrations confirm that the integration meets API response timing requirements. See Publish an OIN integration.
Early Access Features
New Features
New permissions for custom admin roles
Super admins can now assign these new permissions to their custom admin roles:
-
Manage authorization server
-
View authorization server
-
Manage customizations
-
View customizations
The authorization server permissions can be scoped to all or to a subset of the org’s authorization servers. With these new permissions, super admins can now create custom admin roles with more granular permissions for managing their org’s customizations and authorization servers. See About role permissions.
Fixes
General Fixes
OKTA-386570
If an LDAP interface bind request failed, subsequent searches failed with an internal server error instead of a permissions denied error.
OKTA-435855
Web and SPA app integrations created with an Authorization code or Interaction code grant type incorrectly returned an error if the Login Initiated By Either Okta or App option was selected.
OKTA-476570
The System Log didn’t display the app name when users entered invalid credentials during an SP-initiated flow.
OKTA-476896
On the Administrators page, deactivated users with assigned admin roles were included in the Individually assigned count.
OKTA-477494
Some invalid EL expressions incorrectly passed validation.
OKTA-477634
Some users experienced delays when searching for an app on the Okta End-User Dashboard.
OKTA-481752
When users tried to enroll in Okta Verify, VoiceOver screen readers didn't highlight the mobile device type correctly or allow users to select a device. It also selected the iPhone option even though the Android option was also available.
OKTA-482266
During PIV authentication where no certificate or an expired certificate was provided, a 404 error was displayed.
OKTA-482435
When admins upgraded an app to SAML 2.0, the SAML 2.0 setup instructions used the org-scoped certificate instead of the app-scoped certificate.
OKTA-483062
Custom application access error pages redirected to the default Okta error page.
OKTA-484366
Admins couldn’t use the objectGuid attribute as a unique identifier when integrating AD LDS LDAP servers with Okta.
OKTA-486141
If an inline hook was registered and in use under a profile enrollment policy, admins could deactivate or delete the hook. This resulted in an error when that policy was used for self-service registration.
OKTA-486974
An internal ID incorrectly appeared in a policy System Log event.
OKTA-488233
Parallel JIT requests for the same username created duplicate users.
OKTA-488234
The sign-in page didn’t load correctly for some orgs after they upgraded to Identity Engine.
OKTA-488428
Some users lost the ability to reveal passwords for an app when the app drawer feature was enabled.
OKTA-488663
When Full Featured Code Editor was enabled, the full screen toggle on the error page code editor didn’t change to a minimize icon.
OKTA-489050
Sometimes an error message was displayed when admins viewed applications in the Admin Console.
OKTA-489448
In SP-initiated flows, the message instructing users to create their accounts was formatted incorrectly.
OKTA-490811
When an unenrolled device attempted to access an app that required device management, the sign-in request didn't fail gracefully.
OKTA-491164
Some admins weren’t assigned the Admin Console when they were added to a group with assigned admin roles.
OKTA-491264
Sometimes when a super admin deleted a custom admin role that contained email notifications, admins couldn’t update their email notification settings.
OKTA-495549
When groups were exposed in the LDAP interface directory information tree, some filters referencing the entryDn attribute returned the incorrect result code if the group wasn’t found.
OKTA-495598
AD-sourced users who reset their passwords in AD had to reset their passwords again when using IWA or ADSSO to sign in to Okta.
App Integration Fix
The following SWA app was not working correctly and is now fixed:
-
NDFR/SDU (OKTA-485335)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Cisco Umbrella User Management: For configuration information, see Cisco Umbrella - Provision Identities from Okta.
- Dialpad: For configuration information, see Dialpad + Okta | SCIM Instructions.
- Heap Analytics: For configuration information, see SCIM Provisioning: Okta.
SAML for the following Okta Verified applications
-
Common Room (OKTA-483683)
-
Datto Workplace (OKTA-487599)
-
Sounding Board (OKTA-489395)
Weekly Updates
Early Access
Fixes
General Fixes
OKTA-385107
When User Profile Mappings were configured with invalid EL expressions, the validity check returned unwanted text.
OKTA-468575
Attempting to upload a new or replacement certificate to an existing RADIUS application resulted in an error.
OKTA-478259
When a super admin assigned an admin role to an ineligible group, the resulting error message was unclear.
OKTA-478844
Token endpoint events weren't logged as expected by the System Log and Splunk.
OKTA-482807
Admins received a ${request.date} is required error when they tried to add a translation for the New Sign-On Notification email template.
OKTA-485981
Admins were able to save a Global Session Policy rule to deny sign-in attempts from specified zones even though no zones were selected.
OKTA-491554
The Client Secret UI didn't render properly when users switched between authentication methods in an app instance.
OKTA-492337
The Authentication Policy dropdown menu was slow to load large numbers of policies on the Sign-On tab of an app instance.
OKTA-493632
A hyphen was incorrectly added to an app's tooltip when an end user hovered over the app on the End User Dashboard.
OKTA-496728
Client-side access tokens and ID tokens weren't revoked and cleared from an Okta domain's localStorage when a user signed out from a custom OIDC application.
OKTA-498263H
The Activate/Deactivate button for Password Policy didn't work.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
CUES (OKTA-486595)
-
GetFeedback (OKTA-488495)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Britive: For configuration information, see Integrating Okta for Provisioning.
- Uber for Business: For configuration information, see Configuring Okta Provisioning for Uber.
SAML for the following Okta Verified applications:
-
Britive (OKTA-487233)
-
OpsLevel (OKTA-484506)
-
Planview ID (OKTA-487235)
Generally Available
Fixes
General Fixes
OKTA-468400
After an org upgraded to Identity Engine, users who tried to sign in with an external IdP received an access denied error message.
OKTA-468948
The Authenticator Enrolled email template displayed variable placeholder text instead of the name of the Okta Verify app in email notifications to users.
OKTA-477341
On some pages, the help text incorrectly showed Manage people and Manage apps instead of Assign people and Assign apps.
OKTA-489341
Customers couldn't deactivate agents that hadn't completed the configuration process.
OKTA-492864
Okta Verify didn't process the secret key correctly when using one-time passwords to access non-FIPS-compliant orgs.
OKTA-494778
If a user tried to remove a read-only group from their profile page, an error resulted but no error message was shown.
OKTA-495159
When an authentication policy contained a custom expression for evaluating behavior, clicking the email activation link resulted in an Internal Server Error (HTTP 500).
OKTA-497940
When a custom OIDC app integration was created with the Login flow set to Redirect to app to initiate login, sign-in attempts returned an access denied error instead of directing the user to the correct Initiate login URI.
App Integration Fixes
The following SWA apps weren't working correctly and are now fixed:
-
Indeed (OKTA-489451)
-
Mutual of Omaha (OKTA-489714)
-
Telus Mobility (OKTA-489114)
Applications
Application Update:
-
Amazon AWS: The OIDC Client ID for CLI access property is now available in the default version of the Amazon AWS app in Preview orgs.
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Forma: For configuration information, see Forma Scim Integration Guide.
SAML for the following Okta Verified application:
-
eLearnPOSH (OKTA-491201)
Generally Available
Fixes
General Fixes
OKTA-432200
Icons in the Sign-In Widget were repositioned when users clicked Sign in.
OKTA-477637
Unique properties weren't deleted when the group they were associated with was deleted.
OKTA-487291
Password requirements disappeared when the Password Reset page was refreshed.
OKTA-488513
Links for app notes weren't properly converted in the new app settings drawer.
OKTA-493308
Office 365 user provisioning tasks sometimes failed if certain properties were mapped to an empty string in Okta.
OKTA-496981
A data limitation prevented the MFA Enrollment by User report from including group membership.
OKTA-497009
The Authentication policies page returned an error when admins reached the last policy in the list.
OKTA-498070
If a new language code attribute was added as a required attribute to the Okta default profile, the Sign-In Widget wasn’t displayed and the user couldn’t sign in.
OKTA-498118
Admins weren’t properly notified about an invalid inline hook in a profile enrollment policy.
OKTA-499251
Admins couldn’t delete the Okta Verify authenticator from the list of authenticators even though it wasn’t required by any enrollment or authentication policies.
OKTA-500096H
On-premises AD agents weren’t automatically updated to the latest AD version by scheduled updates, and progress banners for manual updates displayed inaccurate agent versions.
OKTA-502045H
Some events didn’t display GeoLocation client data in the System Log.
Applications
Application Update
ModernHealth SCIM functionality has been deprecated and can no longer be used by customers. SAML is still supported.
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Dashworks.ai: For configuration information, see Configure Provisioning for Dashworks.ai.
- Forma: For configuration information, see Forma Scim Integration Guide.
- Parkable: For configuration information, see Parkable SCIM configuration.
April 2022
2022.04.0: Monthly Production release began deployment on April 4
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta On-Prem MFA Agent, version 1.4.9
This version of the agent contains security enhancements. See Okta On-Prem MFA Agent Version History.
Okta Browser Plugin, version 6.9.0 for all browsers
This version includes the following changes:
- Keyboard navigation didn't work properly when users attempted to switch to a new app list in the plugin popover window. Users were unable to close the plugin popover window with keyboard input.
- Version 6.8.0 of the plugin caused issues for some users when they attempted to sign in to an SWA app in an iframe.
Admin Experience Redesign toggle removed
The toggle that allowed super admins to switch between the Admin Experience Redesign and the old experience has been removed. All Okta admins now benefit from our restyled Okta Admin Dashboard, responsive navigation side bar, and modern look and feel.
Allow or deny custom clients in Office 365 sign-on policy
You can filter specific clients in an Office 365 app sign-on rule to allow or deny them access to Office 365 resources. This filter can be used to deny access to untrusted clients or to only allow trusted clients. See Allow or deny custom clients in Office 365 sign on policy
Endpoint integrations
The Device Integrations page now includes an Endpoint Security tab, which allows Admins to manage endpoint integrations with Windows Security Center and CrowdStrike. Endpoint Detection and Response (EDR) integration extends device posture evaluation by enabling Okta Verify to capture signals collected by your EDR client running on the same device. See Endpoint security integrations.
Okta FastPass enhancement
With Okta FastPass, an error now appears in the Sign-In Widget if User Verification is not provided when it is required.
Improved AD group membership synchronization
The ADAppUser distinguished name field is now updated when a user is added to an Okta group and a matching group exists in AD. When an Okta provisioning request moves a user to a new organizational unit, the change is quickly duplicated in AD. This new functionality helps ensure the accuracy and integrity of AD group membership information. Manage Active Directory users and groups.
New App Drawer
The updated app settings panel on the Okta End-User Dashboard allows end users to see all app details in a single view without having to expand multiple sections. End users can quickly differentiate between SWA apps where they have set a username and password and SAML / OIDC apps that are admin-managed with no additional user settings. The updated app settings panel also provides accessibility improvements with better screen reader support and color contrast. See View the app settings page.
ShareFile REST OAuth
Admins can now upgrade to the latest version of our ShareFile integration. OAuth provides more secure authentication and will be now used for Provisioning and Imports. See Configure ShareFile OAuth and REST integration. This feature is made available to all orgs.
Enhancements
Recent activity page link for end users
If Recent Activity is enabled, users can click Last sign in in the footer of the left navigation bar to go directly to the Recent Activity page.
Burst rate limits available on Rate Limit Dashboard
The Rate Limit Dashboard, available from the Admin Console, now includes data on burst limits in your Okta org, in addition to rate limit warnings and violations. The Violations dashboard was renamed Events to acknowledge the increase of scope, and includes the ability to filter on timeline as well as the type of event (warning, burst, and violation). Hovering over the burst rates in the graphs provides more detail and links to the system log for individual endpoint calls. The individual Usage graphs provide details on bursts for the individual API. See Rate limit dashboard and Burst rate limits.
New ThreatInsight enforcement action
If you configure ThreatInsight to log and enforce security based on the threat level detected, ThreatInsight can either limit or block authentication requests from suspicious IP addresses. For example, if a specific IP address is suspected of malicious activity but the threat level is considered low, authentication requests from the IP address are not denied access but might be subjected to a rate limit. See Configure Okta ThreatInsight.
PIV IDP user profile mapping
You can now use idpuser.subjectUid in an Okta user profile when mapping IDP Username for Personal Identity Verification (PIV) IDPs. See Add a Smart Card Identity Provider.
Default policy updates
The Default Global Session Policy and the default authentication policy now allow access to users with any two factors. See Global session policies.
Global Session Policy default rule
Admins can now edit the primary factor condition in the default rule of their org’s Default Global Session Policy. See Edit a global session policy.
Custom app logo preview
Admins can now preview a custom logo before applying it to an app. See Customize an application logo.
Updated error message for Microsoft Graph API
An error message for Microsoft Graph API has been updated to include more details and a possible workaround.
Debug logging for token exchange
The following fields have been added to the System Log for assistance in debugging OAuth2 token exchange events:
- requested_token_type
- subject_token_type
- actor_token_type
- resource
Updated SAML setup instructions
Setup instructions for SAML 2.0 apps now use per app SHA2 certificate during the app creation.
Change to the number of free SMS messages allowed
To balance growing costs of SMS usage while maintaining a commitment to developer and free trial orgs, Okta is changing the number of free SMS messages these orgs are allowed each month. Beginning April 4, 2022, orgs may send a maximum of 100 messages per month. For more information about this change, visit the Okta Developer Community.
Early Access Features
Enhancements
Splunk available for Log Streaming
Many organizations use third-party systems to monitor, aggregate, and act on the event data in Okta System Log events.
Log Streaming enables Okta admins to more easily and securely send System Log events to a specified system such as the Splunk Cloud in near real time with simple, pre-built connectors. Log streaming scales well even with high event volume, and unlike many existing System Log event collectors, it doesn't require a third-party system to store an Okta Admin API token. See Log streaming.
Fixes
General Fixes
OKTA-442031
Some Okta Mobile sign-in flows didn’t work for admins when the Okta Admin Console app required step-up authentication.
OKTA-456484
When more than one authenticator appeared on the authenticator enrollment page, the Return to authenticator list link didn’t appear.
OKTA-460284
SAP Litmos imports failed with an unexpected error.
OKTA-467278
If an error occurred in Okta Verify during authentication or if authentication was cancelled, a delay occurred before the user was prompted again to select a security method.
OKTA-472816
When app admins selected the Agents tab, the error message “Error rendering agents monitor table” appeared and no agents were listed.
OKTA-473180
Sometimes AssertionId for SAML1.1 assertions was poorly formatted.
OKTA-475767
Sometimes, in the Groups page Description column, an equals sign (=) replaced the forward slash ( / ) in LDAP-sourced group names.
OKTA-475774
Users could use ADSSO to sign in to Okta when delegated authentication was disabled.
OKTA-478467
Admins who didn’t have permission to view the Agent monitors page received agent auto-update email notifications.
OKTA-478537
When admins searched for an authentication policy, only the first 100 policies were visible. This occurred on both the Applications page and the Authentication policies page.
OKTA-479110
The sender email address on the Customizations > Emails page was inconsistent with the sender email address on individual templates.
OKTA-479701
Admins were shown events that were unrelated to their account in the Security Events section of the Recent Activity page.
OKTA-482086
Some admins saw an error if they tried to run a report using resource sets created more than a year ago.
OKTA-483011
Sometimes, Okta IWA agent authentications failed during deployment when IWA replay attack detection was enabled.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
MyFonts (OKTA-476809)
-
Quickbooks Time Tracker (OKTA-476695)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Snow Atlas SSO: For configuration information, see Okta as SSO provider.
- Transform: For configuration information, see Configuring Provisioning for Transform.
SAML for the following Okta Verified applications:
-
Atomic Console (OKTA-479344)
-
Intra-mart Accel Platform (OKTA-476864)
-
Mulesoft - Anypoint Platform (OKTA-461170)
-
OfficeTogether (OKTA-476827)
-
QTAKE Cloud (OKTA-480924)
OIDC for the following Okta Verified application:
-
ResoluteAI: For configuration information, see ResoluteAI: Setting up Okta.
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-476780
If an app’s profile enrollment policy didn’t require email verification, end users who started the sign-up process but abandoned it before setting a password weren’t able to use the Forgot password option when they resumed the process.
OKTA-479171
When admins selected older versions of the Sign-In Widget, messages about the latest version were inconsistently displayed.
OKTA-482299
When a super admin removed all admin role assignments from a user, a time-out error sometimes appeared.
OKTA-482472
Admins with view permissions could see the Edit button in the User Account section of Customizations > Other.
OKTA-483063
After some orgs upgraded to Identity Engine, their users received an internal server error when they attempted to sign in.
OKTA-483335
When users signed in to Salesforce with the OAuth app, they weren't prompted to Allow Access. This only occurred if the Salesforce app was configured and the user already had an active session.
OKTA-483338
When users signed in to Google with the OAuth app, they weren't prompted to Allow Access. This only occurred if the Google app was configured and the user already had an active session.
OKTA-484416
In orgs that included OMM apps, Okta RADIUS agents weren’t able to service authentication requests after restart.
OKTA-484474H
The IdP and ADSSO authentication times weren't reflected in the AuthInstant attribute of SAML assertions, which resulted in a failed SAML app sign-in flow.
OKTA-484971
The Recent Activity section of the Okta End-User Dashboard didn't load properly for Internet Explorer users.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
A Bead Store (OKTA-481911)
-
Adobe (OKTA-479001)
-
Adobe Stock (OKTA-483342)
-
American Express Business (OKTA-482556)
-
Mutual of Omaha (OKTA-481802)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
fax.plus: For configuration information, see SCIM - OKTA.
-
PubHive Navigator: For configuration information, see PubHive Navigator - Okta Configuration Guide.
-
Tailscale: For configuration information, see User & group provisioning for Okta.
SAML for the following Okta Verified applications:
-
CardinalOps (OKTA-482262)
-
Curator by InterWorks (OKTA-481345)
-
ModernLoop (OKTA-482260)
Generally Available
Fixes
General Fixes
OKTA-389310
The nonce length for WebAuthn challenges didn't have enough characters for the recommended level of entropy.
OKTA-474861
Users couldn't enroll in Okta Verify Push for recovery even though it was enabled as a primary recovery method.
OKTA-477017, OKTA-486532
When admins added an app to an authentication policy and then searched for an app that didn't exist, the Add button reappeared by the name of their newly added app.
OKTA-483982
Users could enroll the Phone authenticator even though it was disabled in MFA enrollment policies and wasn't available as a recovery option.
OKTA-484105
When an end user manually appended their username to the End-User Dashboard URL, their username wasn't relayed as a login_hint to the Sign-In Widget.
OKTA-486672
When SP-initiated SSO requests for Bookmark apps used the app's embed link, incorrect parameters were passed to the SP.
OKTA-486952
Performance issues occurred for Simple Certificate Enrollment Protocol (SCEP) deployments that used dynamic challenge.
OKTA-488718
The Authentication Policies page failed to load for some orgs.
OKTA-488985
The setup instructions for a manual WS-Federation configuration for Office 365 incorrectly displayed an SHA-2 certificate instead of the SHA-1 org-scoped certificate.
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Applauz: For configuration information, see Integrating Applauz with Okta.
SAML for the following Okta Verified applications:
-
Axiad Cloud (OKTA-465658)
-
BizLibrary (OKTA-438712)
-
Greene King (OKTA-480468)
-
SendGrid (OKTA-485059)
-
SourceWhale (OKTA-472980)
-
TestRigor (OKTA-486166)
Generally Available
Fixes
General Fixes
OKTA-468644
When a super admin scoped a standard role to a group or app and then saved the resource set, any unsaved role assignments were removed from the Administrator assignment by role page.
OKTA-483742
When admins deleted Okta AD agents, scheduled agent auto-updates continued and caused exception errors.
OKTA-484482
The iframeControlHideCatalog option didn't hide the Add Apps link when the Okta End-User Dashboard was embedded.
OKTA-485860
Admins whose custom admin role contained the Edit users' authenticator operations and Edit users' lifecycle states permissions could create API tokens.
OKTA-487293
SAML inline hooks with an AuthNRequest sometimes failed.
OKTA-487334
The SWA copy password window on the Okta End-User dashboard contained UI issues for Internet Explorer users.
OKTA-487453
Deleted users were reindexed in Elasticsearch when admins deleted user data.
OKTA-488616
The doctype declaration wasn't displayed in the default template for error pages code editor.
OKTA-495596H
Admins couldn't customize the End-User Dashboard layout.
OKTA-495695H
A Classic Engine org couldn't upgrade to Identity Engine if its users were enrolled in Okta Mobile.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Carta (OKTA-486196)
-
Chartbeat (OKTA-485773)
-
Rippe and Kingston LMS (OKTA-482602)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
-
Axiad Cloud: For configuration information, see OKTA Axiad Cloud App Document.
-
Loadmill: For configuration information, see Loadmill Okta SSO integration.
-
Torq: For configuration information, see Configure SSO with Okta Open ID from App Catalog.
SAML for the following Okta Verified applications
-
Heap Analytics (OKTA-486230)
-
Secure Code Warrior (OKTA-476859)
March 2022
2022.03.0: Monthly Production release began deployment on March 7
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta Active Directory Password Sync agent, version 1.5.0
This version of the agent includes:
-
Security enhancements.
-
Making .NET Framework 4.6.2 the minimal supported version. Earlier versions are automatically upgraded during agent installation.
-
Okta Military Cloud support.
See Okta Active Directory Password Sync Agent version history.
Okta AD agent, version 3.10.0
This version of the agent contains:
-
Okta Military Cloud support.
-
Bug fixes.
Okta LDAP agent, version 5.12.0
This version of the agent contains support for Okta Military Cloud. See Okta LDAP Agent version history.
Event hooks for custom admin roles
Custom admin role events are now available for use as Event Hooks. This provides more security to admins by ensuring that they have the correct permission to perform tasks. See Event hooks.
Enforce limit and log per client mode for OAuth 2.0 /authorize and /login/login.htm endpoints
The default client-based rate limit for OAuth 2.0 /authorize and /login/login.htm endpoints is now elevated to Enforce limit and log per client (recommended) mode. This means that if your org’s client-based rate limit was previously set to Do nothing or Log per client, the setting is changed to Enforce limit and log per client (recommended) mode.
Note that based on the email communication sent out on Feb 3, 2022 and Feb 25, 2022, these changes are not applicable to certain orgs. See Default client-based rate limit mode change.
New ThreatInsight enforcement option
ThreatInsight evaluates authentication requests to detect potentially malicious activity from IP addresses exhibiting suspicious behavior. If you enable the Log and enforce security based on threat level option, ThreatInsight can limit or block authentication requests from suspicious IP addresses based on the threat level detected. For example, if a specific IP address is suspected of malicious activity but the threat level is considered low, authentication requests from the IP address are not denied access but might be subjected to a rate limit. The rate limit helps ensure that requests from a suspicious IP address don't overload authentication services and affect legitimate traffic. However, if an IP address is suspected of malicious activity and the threat level detected is high, authentication requests from the IP address are blocked. See Configure Okta ThreatInsight.
Validation for custom message templates
If you customize the default SMS message template, the Admin Console checks the message to determine whether it contains GSM or non-GSM characters and enforces the GSM or non-GSM character limit before saving the message. This check ensures that you don't create custom SMS messages that exceed the GSM or non-GSM character limit for message segments.
If you change existing custom templates, the new restrictions are enforced if your messages contain non-GSM characters.
For more information about customizing SMS templates, see Configure and use telephony.
Custom Administrator Roles
The standard admin roles available today don’t always meet all the granular delegated administration requirements, which may result in admins having either more or less permissions than they need.
The Custom Administrator Roles feature allows super admins to:
-
Create admin assignments with granular roles, which include specific user, group, and application permissions.
-
Constrain these admin assignments to resource sets.
Use Custom Administrators Roles to:
-
Increase admin productivity.
-
Decentralize the span of access that any one admin has.
-
Grant autonomy to different business units for self-management.
Some important things to note:
-
The Administrators page has been updated with a new, more intuitive interface for managing roles and permissions. See About the Administrators page.
-
Your pre-existing roles are referred to as “standard roles”. The standard role functionality is the same as earlier but the UI is different. See Use standard roles.
-
You can continue using the pre-existing roles and your existing assignments remain the same.
-
You can also assign custom roles to users who have standard roles assigned.
See Custom admin roles and Best practices for creating a custom role assignment.
System Log events for group app assignments
When an admin role is assigned to a group, the Okta Admin Console is now assigned to the group members much faster, and an Add assigned application to group event (group.application_assignment.add) appears in the System Log. This helps super admins monitor the event activity in their org. See System Log.
Immutable unique data types for Okta LDAP and AD agent actions
Immutable unique data types can now be used with Okta LDAP and AD agent actions. The use of immutable unique data types lets admins locate users when a username is updated, or when the user is moved to another OU. Immutable unique data type support reduces the time admins spend managing users and makes sure they can always locate user profiles after an update or when a username changes. .
ShareFile REST OAuth
Admins can now upgrade to the latest version of our ShareFile integration. OAuth provides more secure authentication and will be now used for Provisioning and Imports. See Configure ShareFile OAuth and REST integration. This feature is currently enabled by default for new orgs only.
Group Push enhancements
Group Push now supports the ability to link to existing groups in NetSuite. You can centrally manage these apps in Okta. This is important because it allows you to set up and push Okta groups into NetSuite instead of recreating them in NetSuite. See About Group Push.
Support for additional social Identity Providers
Social login is a form of SSO that uses existing information from a service such as Facebook, Twitter, or Google to sign in, instead of creating a new account specifically for a third-party website. Social Identity Provider (IdP) popularity varies by industry and region. We're making it easy for Okta admins to add new IdPs with out-of-the-box integrations for GitHub, GitLab, Salesforce, and Amazon, with more to come. These integrations add to our existing social IdP catalog in the OIN, allowing users to quickly sign up or sign in to your application without entering their email or creating a new password. See External Identity Providers.
Risk and behavior evaluation
To improve the visibility of risk scoring and behavior detection, all sign-in requests are evaluated for risk factors and changes in behavior. Impacted orgs can view the results of the evaluation in the System Log. See Identity providers.
Enhancements
Sign-In Widget updates for Okta FastPass
The Sign in with Okta FastPass button no longer appears on the Sign-In Widget when users access Android Native apps that use Webview. Webview doesn't support this functionality.
Copy button updates
In the app settings panel of the Okta End-User Dashboard, the copy buttons for the username and password fields are renamed Copy username and Copy password.
Early Access Features
New Features
Automatically update public keys in the Admin Console
Using private_key_jwt as your app's client authentication method requires that you upload public keys to Okta and then use the private keys to sign the assertion. Then, you must update the client configuration each time you rotate the key pairs. This is time-consuming and error-prone. To seamlessly use key pairs and rotate them frequently, you can now configure private_key_jwt client authentication in the Admin Console for OAuth clients by specifying the URI where you store your public keys. See Manage secrets and keys for OIDC apps.
Enhancements
Incremental Imports for the Org2Org app
Okta now supports incremental imports for the Org2Org app. Incremental imports improve performance by only importing users that were created, updated, or deleted since your last import. See Okta Org2Org.
Fixes
General Fixes
OKTA-447833
Admins couldn’t set up a custom domain URL with a top-level domain of .inc.
OKTA-455641
The Edit Assignment page for the Box app didn’t handle non-alphabetical characters properly.
OKTA-466022
Admins whose custom role contained the Run imports permission couldn’t view their org’s LDAP integrations.
OKTA-468707
The System Log didn't display ThreatSuspected=false for authentication events when no threat evaluation was done.
OKTA-468751
When Okta Verify was the only enrolled authenticator, time-based one-time password (TOTP) wasn’t automatically selected even though it was the last-used authentication method.
OKTA-471299
When ThreatInsight evaluated sign-in attempts for unknown users, the threat level was incorrectly displayed as threatLevel=UNKNOWN in the System Log.
OKTA-471605H
In SP-initiated flows, users' sessions ended when they closed the browser even if they selected Keep me signed in.
OKTA-471815
Some customers noticed duplicate Windows devices on the Devices page when users re-enrolled with Okta Verify.
OKTA-471605H
In SP-initiated flows, users' sessions ended when they closed the browser even if they selected Keep me signed in.
OKTA-472304H
Group push for some customers resulted in a timeout error after one minute.
OKTA-473512
When the Custom Admin Roles feature was enabled, super admins were called Super Organization Administrators.
App Integration Fixes
The following SWA app were not working correctly and are now fixed:
- Asana (OKTA-467306)
- Dashlane Business (OKTA-466333)
- Guardian Insurance (OKTA-470966)
- Loop11 (OKTA-471181)
- Names & Faces (OKTA-468537)
- Nord Layer (OKTA-469771)
- Optum Health Financial (OKTA-465956)
- QuickBooks (OKTA-467864)
- Twitter (OKTA-470889)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- ArmorCode: For configuration information, see Armorcode - How to configure Armorcode app on Okta.
- Cognism: For configuration information, see Okta SCIM Configuration setup.
- Indi: For configuration information, see Okta SSO integration with Indi.
- strongDM: For configuration information, see Set up an App in Okta for User & Group Provisioning.
- Trusona: For configuration information, see Integrating Trusona and Okta SCIM.
SAML for the following Okta Verified applications:
-
Happeo (OKTA-461895)
-
ScreenMeet (OKTA-466613)
-
Shortcut (OKTA-461249)
-
Wonderwerk (OKTA-454149)
-
Zero Networks (OKTA-472331)
OIDC for the following Okta Verified applications:
- Artificial: For configuration information, see Using Okta to log in to Artificial.
- strongDM: For configuration information, see SSO with Okta.
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-374857
When admins searched for groups in the new LDAP interface, results weren’t returned if the search query contained all lowercase characters.
OKTA-440514
Sensitive attributes were exposed when Identity Provider routing rules contained Boolean expressions.
OKTA-452618
Admins whose custom role contained the Edit users' lifecycle states permission but not the View users and their details permission could view the Profile tab on the user page.
OKTA-457354
Updating an access policy rule through the Admin Console sometimes resulted in a browser error. This occurred if the rule was created using the Authorization Server API without an include array in the User Condition object.
OKTA-459720
Some apps that require admin configuration appeared on the App Catalog page of the End-User Dashboard.
OKTA-464002
Admins with two active Okta orgs linked together by the same company name were unable to sign in to the OIN Manager portal.
OKTA-469953
Sometimes, when users signed in with Okta FastPass, Okta Verify continuously requested an authentication factor until they clicked Cancel.
OKTA-470268
If tasks were pending, users experienced slow or unresponsive web browsers after navigating to the Tasks page of the End-User Dashboard.
OKTA-470384
Screen readers didn't properly read text in the App Settings page the when user set focus on Username or Password fields.
OKTA-470541
Sometimes importing from the SuccessFactors app integration failed after timing out.
OKTA-470701
Keyboard navigation and screen readers occasionally lost focus while in the App Settings page of the End-User Dashboard.
OKTA-471668
Button labels were inconsistent on the Global Session Policy page and help links were missing from the Authentication policies page.
OKTA-472593
When the Custom Admin Roles feature was enabled, the Administrator assignment by admin, Edit resources to a standard role, and Edit resource set pages didn’t display group details for imported AD/LDAP groups.
OKTA-472895
When modifying the custom email activation template, an admin could save the template without either of the required verificationLink or verificationToken elements.
OKTA-472928
When modifying the custom email challenge template, an admin could save the template without either of the required emailAuthenticationLink or verificationToken elements.
OKTA-474143
A new public key was displayed in the UI despite the new key generation operation being canceled.
OKTA-476453
Displaying the App Catalog in List View on the End-User Dashboard caused UI errors in Internet Explorer browsers.
OKTA-477943H
Admins couldn’t change the version of the Sign-In Widget for custom domains.
OKTA-478421H
When AD/LDAP users were imported into groups with assigned admin roles, the resulting admin role updates were delayed, and the Grant user privilege event didn’t appear in the System Log.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Data.ai (OKTA-472317)
-
Google Play (OKTA-470657)
-
Zenefit (OKTA-472199)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
SmartHR: For configuration information, see Okta user provisioning integration with SCIM.
-
Wonderverk: For configuration information, see Wonderverk's Okta documentation.
OIDC for the following Okta Verified applications:
-
ePMX: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Marvin: For configuration information, see Okta Configuration Guide.
-
Pretaa: For configuration information, see Pretaa Integration with Okta- OpenID Connect.
Generally Available
Fixes
General Fixes
OKTA-414109
Admins who only had the View application and their details permission could see the Self Service section on the Application > Assignments tab.
OKTA-417477
Making valid changes to the device_sso or online_access scopes in the Edit Scope dialog incorrectly returned an error message.
OKTA-441233
When a super admin saved the email notification settings for a role without making any changes, the settings weren’t restored to their default values for existing admins with that role.
OKTA-463551
Lengthy app names weren't fully listed in the search index of the Okta End-User Dashboard.
OKTA-464217
Onboarding guides were still shown to new users after admins disabled the feature in Customizations > Other > Display Options.
OKTA-467278
If an error occurred in Okta Verify during authentication or if authentication was cancelled, a delay occurred before the user was prompted again to select a security method.
OKTA-469449
Admins couldn’t change their custom sign-in page, and the wrong error message was displayed.
OKTA-469451
Send test email failed with a 500 error for some email templates.
OKTA-471120
For profile enrollment using the Sign-In Widget, the field labels for most base attributes weren't localized.
OKTA-471670
The ThreatSuspected field was missing in the user.session.start event for Radius sign-in requests.
OKTA-472914
Self-service password reset resulted in an incorrect exception message when users attempted to set a password that contained a single-space character.
OKTA-473387
Variables didn’t work in the subject lines of some email templates.
OKTA-476019
Unsaved edits appeared in the read-only view of Identity Provider routing rules.
OKTA-476469
On the Authentication policies page, the preset policies didn’t have descriptions.
OKTA-476480
During self-service password resets or account unlocks, users received an internal server error if they provided an invalid username and selected Okta Verify Push. This occurred in orgs with User Enumeration enabled.
OKTA-478605
During OAuth app creation, EC public keys weren't recognized and couldn't be validated.
OKTA-479004
Some Preview orgs experienced Office 365 import failures with the error message, “An error occurred while creating the Azure Active Directory Graph API client.”
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
MyAtt (OKTA-473277)
-
Nationwide Financial (OKTA-473149)
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Qapita QapMap: For configuration information, see How to configure SSO between Qapita and Okta.
SAML for the following Okta Verified application:
-
Ashby (OKTA-470597)
Generally Available
Fixes
General Fixes
OKTA-409838
When the Custom Admin Roles feature was enabled, admins without the View users and their details permission could see the Profile tab on the user page.
OKTA-448751
The Admin Dashboard sometimes displayed an inaccurate number of user groups.
OKTA-448946
Updating a Salesforce app username created a new user instead of pushing a profile update.
OKTA-456820
If users authenticated with a custom IdP factor, their client details weren't captured in the System Log.
OKTA-461147
The Remember My Last Used Authenticator functionality didn’t display all available authenticators, and the authenticator that was automatically selected hadn't been previously used.
OKTA-472294
When using Branding or Custom Domain features, admins who clicked a button multiple times received an error even though the action completed successfully.
OKTA-472467
Screen readers couldn't tell whether Password input field was hidden or revealed.
OKTA-474997
The Registration - Email Verification and Registration - Activation email templates didn't support translated text.
OKTA-477938
Using Okta Expression Language in an IdP Username to authenticate with PIV resulted in an "application not assigned" error.
OKTA-477943
Admins couldn’t change the version of the Sign-In Widget for custom domains.
OKTA-479799
When the Custom Admin Roles feature was enabled, some admins couldn’t view groups on the Administrators > Admins tab.
OKTA-479983
The Client Secret page didn't render the UI correctly for orgs with the Client Secrets Management feature enabled.
OKTA-480151
Some Expression Language variables still appeared in automated emails.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Angie's List (OKTA-477233)
-
FortiCloud (OKTA-478241)
-
Lutron (OKTA-476161)
-
Tableau (OKTA-471013)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
EZOfficeinventory: For configuration information, see Implement User Provisioning via SCIM with EZOfficeInventory and Okta.
-
Qapita QapMap: For configuration information, see How to configure SSO between Qapita and Okta.
SAML for the following Okta Verified application:
-
Perdoo (OKTA-472102)
OIDC for the following Okta Verified application:
-
Jira SAML SSO by miniOrange: For configuration information, see OAuth/OpenID Single Sign On (SSO) into Jira using Okta.
February 2022
2022.02.0: Monthly Production release began deployment on February 7
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta AD agent, version 3.9.0
This version of the agent contains bug fixes. See Okta Active Directory agent version history.
Okta LDAP agent, version 5.11.0
This version of the agent contains:
-
Support for Proxy Authorization Control version 2 (2.16.840.1.113730.3.4.18). Users who are required to change their password after it is reset by an admin are no longer prompted twice for their password when accessing the End-User Dashboard. This new functionality is available only with LDAP services that support Proxy Authorization Control version 2. To enable this feature, contact Okta Support.
-
Internal improvements and bug fixes.
Endpoint integrations
The Device Integrations page now includes an Endpoint Security tab, which allows admins to manage endpoint integrations with Windows Security Center and CrowdStrike. Endpoint Detection and Response (EDR) integration extends device posture evaluation by enabling Okta Verify to capture signals collected by your EDR client running on the same device. See Endpoint security integrations.
New Custom OTP Authenticator released on a Limited Availability basis
The Custom OTP Authenticator enables admins to deploy a wide variety of one-time password solutions in their Okta environment. See Configure the Custom OTP authenticator.
Sign-In Widget User Identifier
Admins can now customize whether the user’s identifier appears on authentication and enrollment steps of the sign-in page. See Customize text on your sign-in page.
OIN catalog replaces categories with use cases
Integrations in the OIN catalog address multiple use cases beyond SSO, such as LCM, social login, and identity proofing. Okta helps prospective and current orgs identify the OIN integrations that best meet their needs by highlighting the use cases that the integrations address and the functionality that the integrations use. This information is provided on both the OIN Catalog landing page and the integration details page. Okta also provides calls to action to help users immediately find value with these integrations across the Okta product platform. Use cases and functionalities replace app categories and filters, which were previously used to sort integrations. This feature will be gradually made available to all orgs.
Provisioning to Office 365 now requires Admin Consent for Microsoft Graph API
Admins are now required to grant consent for Okta to call Microsoft Graph API to enable provisioning features for Office 365 app instances. This change prepares Okta to migrate provisioning operations to Microsoft Graph API in 2022, which will improve performance and reliability for Office 365 provisioning operations. It also enhances security for Okta customers by limiting Okta's permissions in the customer's Azure Active Directory to only those operations which are required for provisioning. Okta customers who previously configured provisioning to Office 365 are required to grant admin consent in order to make any changes to their existing provisioning settings. See Provide Microsoft admin consent for Okta.
Configure a custom error page
You can customize the text and the look and feel of error pages using an embedded HTML editor. When used together with a custom URL domain (required) and a custom Okta-hosted sign-in page, this feature offers a fully customized error page. For details, see Configure a custom error page.
Configure a custom Okta-hosted sign-in page
You can customize the text and the look and feel of the Okta-hosted sign-in page using form controls and an embedded HTML editor. When used together with a custom URL domain (required) and a custom Okta-hosted error page, this feature offers a fully customized end user sign-in experience hosted by Okta. For details, see Configure a custom Okta-hosted sign-in page.
Custom domains with Okta-managed certificates
When you customize an Okta URL domain, your Okta-hosted pages are branded with your own URL. Okta-managed certificates automatically renew through a Let’s Encrypt integration, a free certificate authority. Okta-managed certificate renewals lower customer developer maintenance costs and reduce the high risk of a site outage when certificates expire. See Customize the Okta URL domain.
Secondary email option for LDAP-sourced users
Admins can now enable a secondary email option for LDAP-sourced users in new orgs. When the secondary email option is enabled, LDAP-sourced users who haven’t previously provided a secondary email are now prompted to provide it on the Okta Welcome page. The prompt continues to appear until a secondary email is provided.
A secondary email helps reduce support calls by providing LDAP-sourced users with another option to recover their password when their primary email is unavailable. See Configure optional user account fields.
Password expiry for AD LDS-sourced users
Admins can now expire the passwords of AD Lightweight Directory Services-sourced users. Forcing users to change their password when they next sign in to Okta keeps passwords updated and enhances org security. See AD LDS LDAP integration reference.
Improved password status accuracy for LDAP-sourced users
The status of LDAP-sourced users is now accurately displayed on the user’s profile page. Previously, the user status incorrectly displayed Password Reset when a password was active. This update reduces the time admins need to spend monitoring and managing user passwords. See About user account status.
New features for HealthInsight
- Administrators can now enable end user email notifications when an end user changes or resets their password. See General Security and HealthInsight.
- HealthInsight now includes a recommendation for admins to enable Password Changed email notifications if the notification isn't yet enabled for the org. See Password changed notification for end users.
- HealthInsight now displays a suspicious sign-in count within the recommendation that users enable ThreatInsight in block mode. See Okta ThreatInsight
Risk scoring improvements
Risk scoring has been improved to detect suspicious sign-in attempts based on additional IP signals. See Risk scoring.
Enhancements
Custom URL domain certificate expiration reminders
Email reminders for custom URL domain certificate expiration are now sent to super admins and org admins only.
Sign-In Widget error messages
If multiple errors occur during a sign-in event, the Sign-In Widget displays all error messages together.
OIN Manager enhancements
Users can now select a maximum of five app categories for ISV submissions. If an app category isn't selected, the app is placed in the all integrations category. See App information.
Email and SMS notification renamed
The New Device Notification email and SMS messages have been renamed New sign-on notification.
App notes
App notes written by an admin are now displayed for users who hover over the app on the Okta End-User Dashboard.
Masking for eight digit phone numbers
The masking algorithm now reveals fewer digits for shorter phone numbers. For example, if the phone number has eight digits, the first five digits are masked and the final three digits are visible.
Early Access Features
New Features
Additional Okta username formats for LDAP-sourced users
Three additional Okta username formats are now available for LDAP-sourced users. In addition to the existing options, admins can now select Employee Number, Common Name, and Choose from schema to form the Okta username. These new options allow admins to use both delegated authentication and Just-In-Time (JIT) provisioning with LDAP directory services. With these new provisioning options, it is now easier for admins to integrate their LDAP servers with Okta. See Configure LDAP integration settings.
Fixes
General Fixes
OKTA-419847
On-Prem MFA API tokens contained scopes beyond what was required for agent operation.
OKTA-433751
End users received errors when accessing SWA apps through the Okta End-User Dashboard if their app passwords contained ampersands.
OKTA-436486
Some orgs couldn’t save email templates containing Velocity variables. This occurred for orgs with Enhanced Email Macros enabled.
OKTA-442296
Some end users received a 400 error after signing in to the Okta End-User Dashboard.
OKTA-443777
Admins couldn’t use the objectGuid attribute as a unique identifier when integrating AD LDS LDAP servers with Okta.
OKTA-451206
When admins enabled LDAP real-time synchronization, the system.agent.ad.realtimesync event erroneously appeared in the System Log.
OKTA-455372
If the information required to evaluate behavior was not available, the System Log displayed BAD_REQUEST for rules that included behavior detection.
OKTA-456046
When upgrading to Identity Engine, orgs received an error stating that they had Sharepoint On-Premises app instances that weren't supported by Identity Engine.
OKTA-459571
In the admin console, the status of RADIUS agents randomly changed from Operational to Disrupted.
OKTA-459778
Customized Sign-In Widgets didn’t match the preview on the Sign-In Widget code editor.
OKTA-460366
On Security > Networks > Add IP Zone, proxy IP addresses weren't explicitly identified as trusted proxy IP addresses.
OKTA-461015
Event information was missing from the Report Suspicious Activity page after users changed their password in the Sign-In Widget.
OKTA-461198
When the Custom Admin Roles feature was enabled, read-only admins could see the Assign to People, Assign to Groups, and Edit User buttons on the Applications page.
OKTA-462025
Admins who refreshed a page in the custom URL domain wizard weren’t returned to the correct step.
OKTA-462114
The ${user.login} variable appeared in default email templates.
OKTA-467470H
When the Okta Browser Plugin was installed, applications opened from the new End-User Dashboard into pop-up windows instead of regular browser tabs. This occurred for Internet Explorer users only.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
- AppSplit (OKTA-462294)
- Auth0 (OKTA-456042)
- Dockerhub (OKTA-463515)
- FinServ (OKTA-463959)
- LoansPQ (OKTA-462410)
- MeridianLink LoansPQ (OKTA-460940)
- New Relic (OKTA-464710)
- ProtonMail (OKTA-463545)
- Salto Keys (OKTA-464469)
- WePay (OKTA-462296)
- Wikispaces (OKTA-462300)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- BrightHire: For configuration information, see Okta SCIM Integration Guide.
- CertCentral: For configuration information, see CertCentral integration with Okta-OpenID.
- Compliance Genie: For configuration information, see Compliance Genie: Setting up SSO with OKTA.
- UniPrint InfinityCloud: For configuration information, see Configuring Okta for InfinityCloud via App Catalog.
- VidCruiter: For configuration information, see Configuring SCIM with Okta.
SAML for the following Okta Verified applications:
-
Compliance Genie (OKTA-456834)
-
SecureCodeWarrior (OKTA-455728)
OIDC for the following Okta Verified application:
- Atomic Console: For configuration information, see Atomic Console OKTA OIN App Configuration Guide.
Weekly Updates
Generally Available
Self-service registration using unverified email
When email is set up as an optional authenticator, end users can complete the self-service registration process without verifying their email address. They can also use the unverified email to reset their password, if required. However, they still must verify the email if it's used for authentication. You can configure this setting in the profile enrollment policy. See Manage Profile Enrollment policies.
Fixes
General Fixes
OKTA-422710
When the Custom Admin Roles feature was enabled, admins who didn’t have the Manage groups permission could view the Actions drop-down menu on the Groups > Rules tab.
OKTA-425072
When a user’s session expired, they weren’t returned to the app sign-in page.
OKTA-439826
Windows Server 2008 R2 was identified as a supported operating system on the Set Up Active Directory page.
OKTA-452937
Admins experienced page scrolling errors when approving requests for Salesforce apps.
OKTA-455572
End users were unable to see their existing password when editing sign-in information for an SWA app.
OKTA-456429
On the App Access Locked page, the contact your administrator link was broken.
OKTA-458310
The Groups page displayed the Admin roles tab for non-AD/LDAP groups. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-460374
When a default application was configured for the Sign-In Widget, no banner indicated to users which app they were signing in to.
OKTA-460647
UI elements for app settings on the Okta End-User Dashboard were inconsistent for admins and end users.
OKTA-460719
The Add Log Stream and Add Identity Provider pages were improperly rendered in Internet Explorer 11.
OKTA-461134
Tooltips didn't wrap properly on the Okta End-User Dashboard.
OKTA-461604
The Username field was missing for admins in the self-service app request workflow.
OKTA-462025
Admins who refreshed a page in the custom URL domain wizard weren’t returned to the correct step.
OKTA-462639
Some international SMS messages had the wrong country code displayed in the System Log.
OKTA-463010
Users who were migrated with a Password Import Inline Hook couldn't reset their passwords through self-service.
OKTA-463346
In Internet Explorer 11, apps on the Okta End-User Dashboard displayed incorrect titles.
OKTA-463622H
Self-service email verification failed if the email contained a redirect to the Okta Dashboard and the user already had an active session.
OKTA-463905
Super admins didn't receive an error if they saved the Administrator assignment by resource set or Administrator assignment by role page without selecting a resource set/role. This occurred for orgs with the Custom Admin Role feature enabled.
OKTA-465050
The app settings drawer incorrectly displayed a password field for SAML apps.
OKTA-466901
Custom attributes identified as cn (Common Name) were automatically mapped as username in Okta.
OKTA-471193H
Group push from Okta to Office 365 didn’t work.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
- Schwab Retirement Plan Center (OKTA-464739)
- SquareSpace (OKTA-466252)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Happeo: For configuration information, see Configuring Okta Provisioning for Happeo.
-
Orca Security: For configuration information, see Okta SSO Configuration SCIM 2.0.
-
Perimeter 81: For configuration information, see Okta (SCIM).
-
Rolebot: For configuration information, see How to configure Single Sign On (OIDC) with Okta.
-
SafeGuard Cyber: For configuration information, see SafeGuard Cyber Okta Configuration Guide.
SAML for the following Okta Verified application:
- CloudAlly (OKTA-453596)
Generally Available
Remember my last-used MFA authenticator
Okta now remembers which MFA authenticator the user selected the last time they successfully signed in. On subsequent sign-in attempts, if the last-used authenticator is WebAuthn, Okta Verify Push, or Okta Verify FastPass, that authenticator appears in the list on the Sign-In Widget. Otherwise, the last-used authenticator is automatically selected by default. Users can still select another authenticator by clicking Verify with something else.
Fixes
General Fixes
OKTA-449722
There was a spelling error in the Help link (Optional) section of the Settings > Account > End User Information page.
OKTA-456339
Admins whose custom admin role contained the Run imports permission couldn't click Back to Applications on the Applications page.
OKTA-465665
End users saw a blank page if they signed in to the Okta End-User Dashboard with a custom domain that ended with com.com.
OKTA-466301
The following issues occurred in the OIN App Catalog on Internet Explorer 11:
- The app details page wasn't shown when an app was selected from the Browse Integration Catalog search results.
- App details pages didn't render correctly.
- Users weren't able to use the up and down arrow keys to navigate search results.
OKTA-466425
On the Okta End-User Dashboard, the app setting drawer's Reveal password wasn't accessible by keyboard commands.
OKTA-466790
Landing on the Reset Password page from /signin/forgot-password URL and clicking the Back to sign in link did not take the user back to the sign-in page.
OKTA-468607
When the Custom Admin Roles feature was enabled, newly added admins didn't always appear on the Administrators page.
OKTA-469099
When orgs enabled both Branding and Custom Domain URL, the default domain displayed customized error pages.
OKTA-471196H
Some end users were unable to reset their password for an embedded flow using the self-service password reset process.
January 2022
2022.01.0: Monthly Production release began deployment on January 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta On-Prem MFA agent, version 1.4.8
This version of the agent contains security fixes. See Okta On-Prem MFA Agent Version History.
Okta Active Directory agent, version 3.8.0
This version of the agent contains:
- Agent auto-update support
- Improved logging functionality to assist with issue resolution
- Bug fixes
Okta RADIUS Server agent, version 2.17.2
This version of the agent contains security fixes. See Okta RADIUS Server Agent Version History.
Admin Console user interface changes
On the Device Integrations page, the Endpoint Management tab now includes an Activate/Deactivate action for legacy Device Trust desktop configurations. It also includes a warning message if an admin attempts to deactivate Device Trust when their Identity Engine app sign-on policy is not configured correctly for devices that are not trusted.
Delivery status of SMS messages in the System Log
Administrators can now view the delivery status for SMS messages in the System Log. For information about the new event type, see Configure and use telephony.
Feature name change: New Sign-On Notification
The New Device Notification functionality is renamed to New Sign-On Notification in the Admin Dashboard, the email notification title, and elsewhere. It refers to the email notification a user receives when there’s a sign-in event from an unrecognized device.
New permissions for custom admin roles
The following new permissions can now be assigned to a custom admin role:
-
Activate users
-
Deactivate users
-
Suspend users
-
Unsuspend user
-
Delete users
-
Unlock users
-
Clear user sessions
-
Reset users' authenticators
-
Reset users' passwords
-
Set users' temporary password
-
Run imports.
The new permissions give super admins more granular control over their delegated org permissions. See About role permissions.
YubiKey OTP authentication now available
YubiKey one-time-password (OTP) mode authentication is now available to Okta Identity Engine users. See Configure the YubiKey OTP authenticator
Service Principal Name functionality improvement
New Service Principal Name (SPN) functionality allows Agentless Desktop Single Sign-on (ADSSO) authentication to continue without interruption when an SPN is updated. A service account and an SPN are required for ADSSO Kerberos authentication. With this change, you can now update the SPN frequently as an additional security precaution. See Create a service account and configure a Service Principal Name.
OAuth Dynamic Issuer option
An authorization server’s issuer URL can be used to validate whether tokens are issued by the correct authorization server. You can configure the issuer URL to be either the Okta subdomain (such as company.okta.com) or a custom domain (such as sso.company.com). See API access management.
When there are applications that use Okta’s subdomain and other applications that use the custom domain, the issuer validation breaks because the value is hard-coded to one domain or the other.
With Dynamic Issuer Mode, the issuer value in minted tokens is dynamically updated based on the URL that is used to initiate the original authorize request.
For example, if the authorize request is https://sso.company.com/api/v1/authorize, the issuer value is https://sso.company.com.
Dynamic Issuer Mode helps with:
-
Split deployment use cases
-
Migration use cases when customers migrate from the Okta domain to a custom domain
-
Support with multiple custom domains
Rate limit dashboard
The new rate limit dashboard helps you investigate the cause of rate limit warnings and violations. You can also use it to view historical data and top consumers by their IP address.
This helps you:
-
Isolate outliers
-
Prevent issues in response to alerts
-
Find and address the root cause of rate limit violations
You can access the dashboard using the link provided in the rate limit violation event in the System Log. See Rate limit dashboard.
You can also open the dashboard in the Admin Console to monitor API usage over a period of time, change rate limit settings, and customize the warning threshold. See Rate limit monitoring.
Error response updated for malicious IP address sign-in requests
If you block suspicious traffic and ThreatInsight detects that a sign-in request comes from a malicious IP address, Okta automatically denies the user access to the organization. The user receives an error in response to the request. From the user’s perspective, the blocked request can’t be identified as the result of ThreatInsight having identified the IP address as malicious.
Make Okta the source for Group Push groups
Admins can now make Okta the profile source for all members of a group that is used for Group Push. When this feature is enabled, integrated apps can't change app group memberships. This functionality allows admins to maintain the accuracy of app group membership and prevents changes to group membership after a push. See Manage Group Push.
Password change notifications for LDAP-sourced users
Password change email notifications may now be sent to LDAP-sourced users.
LDAP-sourced users secondary email prompt on first sign in
Admins now have the option to prompt LDAP-sourced users for a secondary email when they sign in to Okta for the first time. When a secondary email is provided, password reset and activation notifications are sent to the user’s primary and secondary email addresses. Duplicating these notifications increases the likelihood they are seen by users and reduces support requests. See Configure optional user account fields.
Directory Debugger for Okta AD and LDAP agents
Admins can now enable the Directory Debugger to provide Okta Support with access to Okta AD and LDAP agent diagnostic data. This new diagnostic and troubleshooting tool accelerates issue resolution by eliminating delays collecting data and improves communication between orgs and Okta. See Enable the Directories Debugger.
Enhancements
Improved SIW error messages
The Sign-In Widget now has improved JIT error messages.
OIN Manager enhancements
The OIN Manager includes the following updates for ISV submissions:
-
It clarifies that OID and SAML integrations must support multi-tenancy.
-
It clarifies that only one OIDC mode can be selected for an OID integration.
-
It allows the format ${app.domain}/redirect_url for URIs.
-
It no longer allows ISV submissions for the Social Login and Log Streaming categories. See OIN App Integration Catalog.
-
It allows the use of app instance properties when configuring single logout (SLO) for SAML app integrations.
-
It requires that ISV submissions specify one or more use cases. Existing submissions may need to be updated to change from previous categories to the new use cases.
SHA type displayed for SAML certificates
SHA type is now displayed for SAML certificates in the Admin Console.
Fixes
General Fixes
OKTA-420065
Launch on sign-in apps on the Okta End-User Dashboard launched multiple times after the user signed in.
OKTA-448006
Some branded pages used an org’s previously uploaded logo rather than their new theme logo.
OKTA-452612
User context wasn’t included in some orgs' token inline hook request data.
OKTA-453969
Some Duo users were unable to authenticate after upgrading to Okta Identity Engine.
OKTA-454206
Some admins without super admin permissions could view a link to the Admin role assignments report. This occurred for orgs with the Custom Admin Roles feature enabled.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Bendigo Bank (OKTA-454211)
-
EdgeCast (OKTA-453148)
-
Maxwell Health (OKTA-454213)
-
My T-Mobile (OKTA-455732)
-
Redis (OKTA-454218)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Javelo: For configuration information, see Okta SCIM - Javelo App.
- Workstream: For configuration information, see Configuring SCIM for Workstream.
SAML for the following Okta Verified application:
-
Regal Voice (OKTA-448791)
Weekly Updates
Fixes
General Fixes
OKTA-443601
In the User Accounts section of the Customizations page, the incorrect term User Identity Master was used instead of User Identity Source.
OKTA-450647
When the Custom Admin Roles feature was enabled, the Admin role assignments report included deactivated admins.
OKTA-454965
Admins couldn’t unsubscribe from Okta AD agent auto-update email notifications because the Agent auto-update notifications: AD agent checkbox wasn’t available in the System notifications area of the Settings page.
OKTA-458760H
When the New Social Identity Provider integrations feature was enabled, IdP profiles weren't always saved and the Redirect Domain field wasn't available.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Circulation (OKTA-456780)
-
CWT (OKTA-455733)
-
Key Bank (OKTA-455731)
-
MyFitnessPal (OKTA-455735)
-
Shutterstock (OKTA-456777)
-
The Hartford EBC (OKTA-454220)
-
TimeLog (OKTA-457372)
-
Verizon Wireless Business (OKTA-455729)
-
Xfinity (OKTA-457369)
Applications
New Integrations
SAML for the following Okta Verified applications:
-
Blingby Live (OKTA-455293)
-
BrightHire (OKTA-456906)
-
Jones (OKTA-453595)
-
TrackJS (OKTA-456630)
Generally Available
Fixes
General Fixes
OKTA-288443
Links from an expired session didn't redirect users to the Okta End-User Dashboard when they signed in.
OKTA-332414
The All apps filter in the Okta End-User Dashboard catalog was incorrectly translated.
OKTA-414419
Admins with the View application and their details permission could view the Push Status drop-down menu and the Push Groups, Refresh App Groups, and Bulk Edit buttons on the Application > Push Groups tab. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-416052
The Sort Apps button and its drop-down menu were covered by the left navigation bar on mobile devices.
OKTA-419846
RADIUS agent API tokens contained scopes beyond what was required for agent operation.
OKTA-441218
When the Custom Admin Roles feature was enabled, third-party admins could view their admin email notification settings.
OKTA-443467
Admins were unable to sign in to the Admin Console if they had first signed in with a non-admin user account.
OKTA-443980
Admins couldn’t select a new Default Application for Sign-In Widget if the app they’d previously used was deleted.
OKTA-446224, OKTA-455268
New admins weren’t always provisioned for Salesforce Help Center.
OKTA-446449
Memberships to Salesforce Public Groups were removed from Salesforce when group memberships were updated in Okta.
OKTA-447069
Some users were unable to access their bookmark apps after migrating to the new Okta End-User Dashboard.
OKTA-447114
Okta sent MFA reset email notifications even though the factor deactivation didn’t take effect.
OKTA-447813
Sometimes, admins were unable to remove apps from the Create a resource set page. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-454385
Password change email notifications were incorrectly sent to end users in orgs with URLs containing api/v1/user.
OKTA-457225
Users who entered their username incorrectly during enrollment in Okta Verify were shown Internal server error instead of a descriptive error message.
OKTA-457233
The default zone name for legacy IP zones was hardcoded in English and displayed in the Admin Console as a text string that could not be localized.
OKTA-457592
On the Admin assignment by admin and Admin assignment by role pages, an error sometimes appeared when the admin removed an existing standard role from the assignment and replaced it with another role. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-459977
When a user accessed some SAML apps, the sign-in flow was initiated twice.
OKTA-460597
When the Custom Admin Roles and CSV Directory features were enabled, admins with the Manage applications permission couldn’t access the Directory Integrations page.
OKTA-460636
When the Custom Admin Roles and Application Entitlement Policy features were enabled, admins with the Edit application's user assignments permission couldn’t assign apps to users.
OKTA-460767
Admins could click Finish multiple times after adding or updating a custom domain certificate. This resulted in duplicate API calls.
OKTA-460908
Some lengthy app names caused UI errors on the Okta End-User Dashboard.
OKTA-462342
When a user copied their username in the app drawer, they were incorrectly notified that the app's password was copied to the clipboard.
OKTA-466809H
A script error occurred when users with an embedded Internet Explorer browser attempted to sign in to Okta.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Allegra (OKTA-449137)
-
Clio (OKTA-458076)
-
DocuSign (OKTA-456094)
-
Expedia (OKTA-455734)
-
FreeAgent (OKTA-454216)
-
Go to Connect (OKTA-454638)
-
QuickBooks (OKTA-457705)
-
SuccessFactors (OKTA-449132)
-
TeamPassword (OKTA-456778)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Almanac: For configuration information, see Almanac - Okta SCIM Configuration.
- Dashworks: For configuration information, see Dashworks Integration with Okta- OpenID Connect.
- Offishall: For configuration information, see User provisioning with Okta.
- Opal: For configuration information, see Setting up Opal's Okta SCIM Integration.
- Xakia: For configuration information, see Okta App SCIM Configuration Guide.
SAML for the following Okta Verified applications:
-
Almanac (OKTA-456412)
-
Observe (OKTA-455308)
-
ReviewInc (OKTA-457711)
-
Spherexx (OKTA-453592)
-
Transform (OKTA-457712)
-
VidCruiter (OKTA-461233)
OIDC for the following Okta Verified applications:
- Atomic Dashboard: For configuration information, see Atomic Dashboard OKTA OIN App Configuration Guide.
- Fellow.app: For configuration information, see Fellow Okta Integration Guide (SSO).