Configure Okta Verify options
After you add Okta Verify as an authenticator, you configure the options that control how end users interact with Okta Verify when they authenticate. You can also enable Okta FastPass.
Before you begin
- If you activate push notification with number challenge, ensure that users can see the number challenge instructions:
- If your org uses a customized Sign-In Widget, its version must be 3.3.0 or later.
- If your org calls the Authentication API directly, update your code to handle the number challenge API response. See Response example (waiting for 3-number verification challenge response).
- If your end users are behind a firewall that restricts traffic to or from the internet, they may be unable to receive the Okta Verify push notifications. Open ports 5228, 5229 and 5230 on the firewalls to allow connectivity with Google Firebase Cloud Messaging. Allow the firewall to accept outgoing connections to all IP addresses contained in the IP blocks listed in Google's ASN of 15169.
- For security reasons, Okta doesn't allow inspection or modification of traffic between Okta Verify and its endpoints. If you use an SSL proxy in your environment, exclude your organization's default Okta domains from inspection. Usually Okta domains are *.okta.com or *.oktapreview.com . For a complete list of Okta domains, see Allow access to Okta IP addresses.
- If you restrict access to Federal Information Processing Standard (FIPS)-compliant devices:
- Android users must enable a secure PIN on their devices to make them Federal Identity, Credential, and Access Management (FICAM)-compliant. Otherwise, they can't access your org.
- Some Android hardware isn't certified as FIPS-compliant. You may have to consider the security implications of using hardware keystores against the need for FIPS compliance.
Start this task
- In the Admin Console, go to Security > Authenticators.
- In the Setup tab, go to Okta Verify and click Actions > Edit.
- In the Verification options section, choose the authentication methods that appear to end users when they authenticate.
TOTP (on by default) (Android and iOS only) Users verify their identity by entering a six-digit code generated by Okta Verify when they're attempting to authenticate. Push notification (Android and iOS only) Users verify their identity by tapping a notification pushed to their mobile device when they're attempting to authenticate. Okta FastPass (All platforms)
Select this option to enable Okta FastPass on all platforms. Users verify their identity by tapping or clicking the Use Okta Verify on this device button that appears when they’re attempting to access an app. See Configure Okta FastPass Regardless of which verification options you select, end users are still enrolled automatically in all of them. They appear in the Account Details page of the app as Authentication Code, Push Notification, and Okta FastPass.
Enrolling users in all methods automatically but letting you control which methods are shown to them when authenticating simplifies the user experience. You can add or remove methods later.
-
If you select the Okta FastPass (All platforms) option, the Okta FastPass section appears.
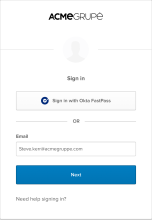
Show the "Sign in with Okta FastPass" button Select this checkbox to display the Sign in with Okta FastPass button on the Sign-In Widget.
By default, this checkbox isn't selected. End users don't see that this sign-in method is available to them, even though Okta FastPass is enabled. Consider leaving this checkbox clear if you want to deploy Okta FastPass to your users gradually.
-
From the User verification list, select if biometrics are preferred or required during authentication with Okta Verify:
Preferred
Users can enable biometrics during enrollment or at another time. Users can enroll devices that don't support biometrics.
Required
Users are prompted to set up biometrics when they create an Okta Verify account or the next time they attempt to sign in with Okta Verify on the enrolled device. If the device doesn't support biometrics, users can't set up an Okta Verify account or authenticate with Okta Verify.
After setting up biometrics, users receive a biometric prompt each time they sign in with an Okta Verify push notification.
-
In the Push notification: number challenge section, select an option to choose whether to include a number challenge with an Okta Verify push challenge.
Number challenge verifies that a sign-in attempt to a protected app came from the intended user and not from an unauthorized person. It presents a number in the sign-in instructions and pushes a notification to Okta Verify on the user's mobile device. The user selects the number in Okta Verify on their mobile device that matches what they see in the sign-in instructions. They're then allowed to access the protected app.
Number challenge helps prevent phishing by ensuring that the user possesses both Okta Verify and the device initiating the sign-in attempt.
Never
Users are never presented a number challenge regardless of the risk level of the authentication attempt.
Only for high risk sign-in attempts
You can present a number challenge to users only if the sign-in attempt is assessed to be a certain risk level, such as high risk. Admins must configure settings for sign-on policy rules. See About Risk Scoring.
All push challenges
Users are presented a number challenge with all Okta Verify push challenges regardless of risk level.
If you select the All push challenges option, Okta Verify for Android version 6.1.1 crashes for users created in Okta Identity Engine. Advise these users to update to the latest version of Okta Verify.
-
In the FIPS Compliance section, choose whether to permit any, or only FIPS-compliant Android or iOS devices, to enroll in Okta Verify.
The FIPS standards are a set of technical requirements developed by the United States government. They establish computer security guidelines for government agencies, corporations, and organizations.
When this option is enabled, Okta Verify uses FIPS 140-2 validation for all security operations. Okta also meets FedRAMP FICAM requirements by relying on FIPS-validated vendors.
FIPS compliant devices only
Users may only enroll a FIPS-compliant device in Okta Verify.
Any device
Users may enroll any device in Okta Verify.
- Click Save.
User experience
The Sign in with Okta FastPass button
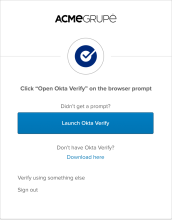
When users click Sign in with Okta FastPass, they're prompted to open Okta Verify:
Push notification: Number challenge
If you select the Only for high risk sign-in attempts or All push challenges option:
- When accessing a protected resource, an Android or iOS user enrolled in Okta Verify push notifications clicks the Get a push notification option in the sign-in instructions.
- A number appears in the sign-in instructions.
- On the mobile device, a notification with a Review option appears in Okta Verify. The user taps Review, then the number on their device that matches what they see in the sign-in instructions. Verification succeeds only if the numbers match. This ensures that the user initiated the sign-in attempt and not an unauthorized person. Details about where the sign-in attempt originated appear below the number choices. Optionally, the user can tap Cancel the sign-in attempt to deny the sign-in attempt.
See the end-user documentation: Sign in with an Okta Verify push notification (iOS) or Sign in with an Okta Verify push notification (Android).
About Risk Scoring
You can combine number challenges with Okta Risk Scoring to increase the security of sign-ins to your Okta org. Okta assesses risk based on multiple criteria, including details about the device and its location. When enabled, Risk Scoring assigns a risk level to each Okta sign-in, and admins can configure a sign-on policy rule to take different actions based on the risk level of the sign-in, such as prompting for multifactor authentication if the sign-in is considered high-risk. See Risk Scoring for instructions.
Known limitations
- Okta FastPass and push notifications aren't available for iPod Touch devices.
- Authentication with biometrics isn't supported on Apple Watch.
- For Android devices, only biometric methods classified by Google as Class 3-Strong (facial and fingerprint recognition) are supported.
- Biometrics isn't supported on Android 12 if Okta Verify is installed on the work profile. End users receive a Keystore not initialized error and they can't enable biometrics. To unblock affected users, set User verification to Preferred, and then advise end users to skip the biometrics enablement step.
- Push notification: Number challenge isn't supported in LDAPi and RADIUS environments. The three-number challenge appears in the Okta Verify app but the matching number doesn't appear in the end user's desktop browser. In this case, configure an MFA authenticator other than Okta Verify.
- Multiple user profiles aren't supported on a single macOS or Windows device if you select Okta FastPass as a verification option.
-
Okta Verify authentication doesn't function properly if HTTP Strict Transport Security (HSTS) is enabled for loopback. Users that develop, host, or debug websites locally often enable this option. If your organization doesn’t require HSTS for security reasons, advise your users to remove the Okta URL from the list of domains that require HSTS. Consult your browsers' documentation for instructions and share them with your users.
Next steps
Continue with the procedure in Enroll Okta Verify in an authentication enrollment policy.
Related topics
Configure the Okta Verify authenticator