Add Kerberos application
Use the Access Gateway Admin UI console to add a Kerberos application with Okta.
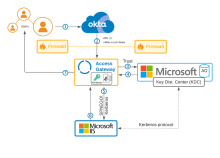
Architecture and flow
|
| See Kerberos overview |
Before you begin
Ensure that:
- Access Gateway is installed and configured. See Manage Access Gateway deployment.
- Access Gateway uses your Okta tenant as an Identity Provider (IdP). See Configure your Okta org as an Identity Provider.
- You have administrator rights on your Okta tenant and can create groups and assign applications.
- You have a Windows server configured with IIS application and Active Directory Services running as a Domain Controller (DC) and implementing Kerberos (IWA) SSO. This is an example architecture, as it would be unusual in large production environments to have an application server (IIS) also be a DC.
- The Windows DNS server serves the Access Gateway DNS.
- You're using a supported release of Kerberos:
- Microsoft IIS IWA: IIS 7 or later
- Microsoft OWA IWA: IIS 7 or later
If you're hosting Access Gateway in a customer environment, you can make DNS changes using the command line management console. See Manage DNS Settings.
Typical workflow
| Task | Description |
|---|---|
| Create a containing group |
Create an optional group for use with the application. |
| Add Access Gateway to Windows DNS |
Windows is the DNS provider for Access Gateway. Add DNS entries for Access Gateway instances. |
| Create Windows Access Gateway service account |
Create a service account. Access Gateway requires a set of known Windows credentials, which the instance uses to configure the Kerberos service. |
| Create keytab |
Create a keytab file. |
| Add Kerberos service |
Create and configure a Kerberos service. |
| Configure Windows Server IIS for constrained delegation |
Kerberos requires that Window IIS is configured for constrained delegation |
| Create application |
Create a Microsoft IIS IWA application. |
| Test the application |
Test the application using header and policy simulation. |
| Troubleshoot |
Troubleshoot the integration. |