Kerberos overview
This overview describes the components, flow and version requirements for integrating Kerberos based Windows applications and Access Gateway. For more information about Windows Kerberos architectures see Kerberos application reference architecture.
Topics:
Architecture
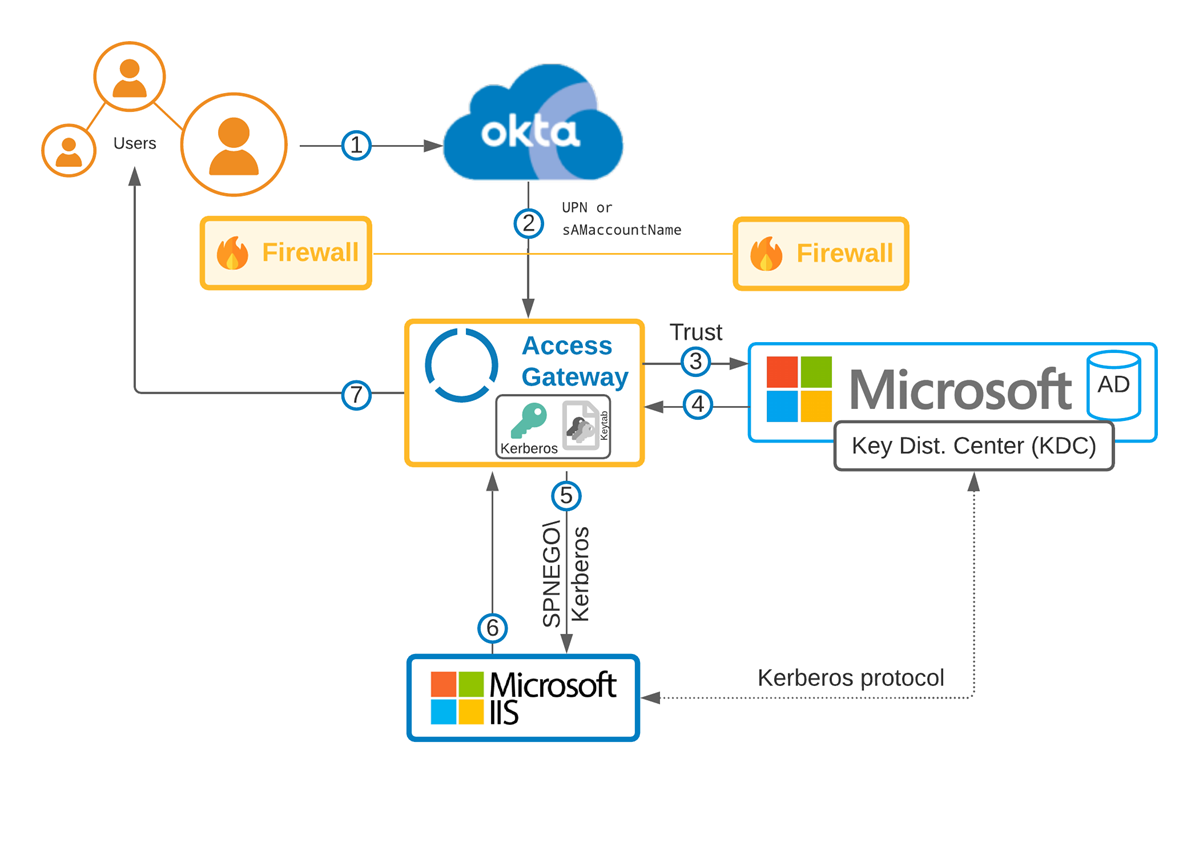
Flow
- User signs in.
- Okta sends user identity to Access Gateway.
- Access Gateway accesses the predefined KDC with credentials.
- KDC returns a Kerberos ticket.
- Access Gateway redirects to a backing application.
- Application returns completed request.
- Access Gateway performs rewrites and returns request to user.
Components and requirements
| Component | Description and requirements |
|---|---|
| Okta Access Gateway | All versions of Okta Access Gateway support Kerberos. |
| Microsoft IIS IWA or OWA IWA |
Supported versions:
|
|
Dynamic Name Services |
Access Gateway configured to use Windows DNS. See Add Access Gateway to Windows DNS for more information. |
|
Windows Access Gateway service account |
Account in the Windows domain to be used by the Kerberos service. |
|
Keytab |
A keytab, used when configuring an Access Gateway Kerberos service. See Create keytab for details of creating a keytab. |
| Okta Access Gateway Kerberos | Kerberos service instance configured. See Add Kerberos service for details of defining a Access Gateway kerberos service. |
| External URL | External URL specified by the Public Domain field> within Access Gateway. For example: https://iis.idaasgateway.net. |
