Okta Identity Engine release notes (2023)
January 2023
2023.01.0: Monthly Production release began deployment on January 17
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Improvements to the self-service registration experience
Earlier versions of the self-service registration (SSR) flow used a complicated array of templates to send activation emails to end users. The simplified SSR flow reduces this to only two email templates with customized welcome messages. If your application requires immediate verification of the end user’s email address, Okta uses the Registration - Activation template. This template includes a magic link for a smoother sign-in experience. If email verification isn't immediately required to sign in to the application, Okta uses the Registration - Email Verification template. This template includes a link for end users to complete email verification at any time after they successfully sign in to the application. See Customize email notifications and the Okta email (magic link/OTP) integration guide. This feature is currently enabled by default for new orgs only.
Revoke user sessions
Admins can end all Okta sessions for an end user when resetting their password. This option protects the user account from unauthorized access. If policy allows, Okta-sourced end users can choose to sign themselves out of all other devices when performing self-service password reset or resetting their passwords in Settings. See Revoke all user sessions. This feature is now enabled by default for all orgs.
Directory Debugger for Okta AD and LDAP agents
Admins can now enable the Directory Debugger to provide Okta Support with access to Okta AD and LDAP agent diagnostic data. This new diagnostic and troubleshooting tool accelerates issue resolution by eliminating delays collecting data and improves communication between orgs and Okta. See Enable the Directories Debugger. This feature is being re-released.
Non-associated RADIUS agents deprecated
Access for RADIUS agents that have not been associated with an application has now been disabled. See RADIUS integrations.
Unusual telephony requests blocked by machine-learning measures
SMS and voice requests are now blocked if an internal machine-learning-based toll fraud and abuse-detection model considers the requests unusual. Telephony requests that are blocked by the machine-learning model have a DENY status in the System Log.
Enhancements
View last update info for app integrations and AD/LDAP directories
Admins can view the date an app integration was last updated by going to Applications > Applications and selecting the integration. They can view the date an AD/LDAP directory integration was last updated by going to Directory > Directory Integrations and selecting the integration.
Internet Explorer 11 no longer supported
A new banner has been added on the End-User Dashboard to notify the Internet Explorer 11 users that the browser is no longer supported.
MFA report column selection
In the MFA Enrollment by User report, you can now choose which columns to hide or show in the data table. See MFA Enrollment by User report.
Early Access Features
Enhancements
AWS region support for EventBridge Log Streaming
EventBridge Log Streaming now supports all commercial AWS regions.
Fixes
General Fixes
OKTA-437264
The HEC Token field wasn't displayed correctly in the Splunk Cloud Log Stream settings.
OKTA-454996
Some users were able to access apps on non-managed devices.
OKTA-519198
Groups and apps counts displayed on the Admin Dashboard weren't always correct.
OKTA-543969
Accented characters were replaced with question marks in log streams to Splunk Cloud.
OKTA-548780
Custom domain settings were deleted during editing if the admin chose the option Bring your own certificate.
OKTA-553006
When authenticated users attempted to access an app they weren’t assigned to, they were redirected to a sign-in page with a permission error.
OKTA-553364
The Custom Authenticator allowed Android users to sign in without biometric verification even though user verification was required.
OKTA-557762
In some cases when Okta Verify wasn’t active, users couldn’t access apps if the authentication policy had OS version conditions for device assurance.
OKTA-559571
The Help link on the Administrators page directed users to the wrong URL.
OKTA-561259
On the Edit role page, the previously selected permission types weren’t retained.
OKTA-561309
A misleading error message appeared when the authentication policy rule’s possession requirements required an unavailable authenticator.
OKTA-564264
Notifications for adding or renewing fingerprint authentication were sometimes not managed correctly.
Applications
Application Update
New GitHub Teams API URL: In response to GitHub's plan to sunset deprecated Teams API endpoints over the coming months, our GitHub integration has been updated to use the new /organizations/:org_id/team/:team_id path. No action needed for Okta admins.
New Integrations
OIDC for the following Okta Verified applications:
-
Infra: For configuration information, see Infra Configuration Guide.
-
Kanbina AI: For configuration information, see the Kanbina AI Documentation.
-
Riot Single Sign-on: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Tracxn: For configuration information, see Configure SSO between Tracxn and Okta.
Weekly Updates
Fixes
General Fixes
OKTA-394045
The End-User Dashboard wasn't aligned correctly when viewed on mobile browsers.
OKTA-460054
Office 365 nested security groups sometimes failed to synchronize correctly from Okta.
OKTA-522922
Not all users deactivated in an Org2Org spoke tenant were deprovisioned in the hub tenant.
OKTA-534291
Samanage/SolarWinds schema discovery didn't display custom attributes.
OKTA-544943
When a user was deactivated in Okta, the Okta Workflows and Okta Workflows OAuth app integrations weren't removed from the user's assigned app integrations.
OKTA-547756
An incorrect error message was displayed during self-service registration when an email address that exceeded the maximum length allowed was entered.
OKTA-547978
If an admin account was deleted, certificate authorities uploaded by the admin account didn’t load on the Device Integrations page.
OKTA-548390
Enabling Agentless DSSO didn't create a default routing rule if no routing rules existed.
OKTA-549213
User's weren't able to activate Windows Hello after enrolling in Okta Verify for Microsoft Windows.
OKTA-550739
Users could request that one-time passwords for SMS, Voice, and Email activation be resent more times than allowed by the rate limit.
OKTA-556056
Group claims failed if a user who belonged to more than 100 groups appeared in the group claims expression results.
OKTA-558840
Some users were unable to complete self-service password resets and received an error.
OKTA-561264
Admins received an error when they used an internal URL to configure user help for device assurance policies.
OKTA-564242
Access tokens for some users didn’t match the lifetime specified in the access policy rule.
OKTA-565041
Group filtering failed when more than 100 groups appeared in the list of results.
OKTA-565899
An incorrect error message appeared when users saved an empty Website URL field in their on the fly app settings.
OKTA-566372
Users were sometimes unable to sign in to several Office 365 apps from Okta.
OKTA-567711
In some orgs, Email Change Confirmed Notification emails were sent unexpectedly. Admins should verify that the recipients lists audience settings are accurate for Change Email Confirmation and Email Change Confirmed Notification.
OKTA-567970
When users were created using the API (/users/${userId}/factors/questions), a null custom security question and answer were included in the response.
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Verona: For configuration information, see Configuring Provisioning for Verona.
SAML for the following Okta Verified applications:
-
Alibaba Cloud CloudSSO (OKTA-531834)
-
DoControl (OKTA-556624)
-
EasyLlama (OKTA-547466)
-
Extracker (OKTA-555971)
-
Saleo (OKTA-552314)
-
Verona (OKTA-551188)
-
Viewst (OKTA-555217)
-
WOVN.io (OKTA-551752)
OIDC for the following Okta Verified application:
- Sharry: For configuration information, see the Sharry OKTA CONFIGURATION GUIDE.
Generally Available
Content Security Policy enhancements
Over the next few months we are gradually releasing enhancements to our Content Security Policy (CSP) headers. During this time you may notice an increase in header sizes.
Fixes
General Fixes
OKTA-532840
Users created using Just-In-Time provisioning weren't assigned to a group when a group rule existed.
OKTA-537944
AD-sourced users received an error when resetting passwords while an Okta session was active in the browser.
OKTA-545918
Admin roles that were granted to a user through group membership sometimes didn't appear on the user's tab.
OKTA-551921
When a large number of profile mappings were associated with a user type, updates to the user type could time out.
OKTA-552273
Users who signed in to the End User Dashboard using a federated sign-in flow without a factor verification were shown an incorrect last sign-in time.
OKTA-552566
Users were sometimes asked to re-authenticate during an active session even though the authentication policy re-authentication frequency was set to Never re-authenticate if the session is active.
OKTA-553201
Users who scanned a Google Authenticator one-time passcode with Okta Verify received an error message and couldn't enroll in the authenticator.
OKTA-554013
Batch federation of multiple Microsoft Azure domains failed if the batch contained any child domains.
OKTA-557337
Users with apps provisioned with password sync enabled weren't challenged for multifactor authentication when they signed in from new IP addresses or a new city even though the Global Session Policy required re-authentication under those conditions.
OKTA-559661
Some org upgrades failed when a single sign-on factor was required for Admin Dashboard access and only the YubiKey, Duo Security, and Symantec VIP MFA factors were enabled but not recognized for migration.
OKTA-564420
Users couldn’t sign in to their org subdomain from okta.com if Captcha was enabled.
OKTA-566285
A threading issue caused directory imports to fail intermittently.
OKTA-566682
When an admin configured an IdP routing rule that allowed users to access certain apps, the list of available apps was blank.
OKTA-566824
Sometimes super admins encountered a timeout when listing admin users on the Administrators page in the Admin Console.
OKTA-567707
A security issue is fixed, which requires RADIUS agent version 2.18.0.
OKTA-567972
An unclear error message was returned when a group rules API call (create, update, or activate) was made to assign users to read-only groups (for example, Everyone ).
OKTA-567979
Last update information was displayed for API Service Apps and OIDC clients.
OKTA-571393
Users couldn’t enroll YubiKeys with the FIDO2 (WebAuthn) authenticator and received an error message on Firefox and Embedded Edge browsers.
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- BizLibrary: For configuration information, see Configuring SCIM with Okta.
SAML for the following Okta Verified applications:
-
Better Stack (OKTA-566261)
-
Mist Cloud (OKTA-559122)
-
Tower (OKTA-567818)
OIDC for the following Okta Verified application:
- Oyster HR: For configuration information, see Okta configuration guide | Oyster.
February 2023
2023.02.0: Monthly Production release began deployment on February 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Agents page removed from the navigation panel
The operational status of org agents moved from the Agent page of the Admin Console to the Status widget of the Admin Dashboard. See View your org agents' status.
Splunk edition support for Log Streaming integrations
The Spunk Cloud Log Streaming integration now supports GCP and GovCloud customers. You can set the Splunk edition parameter (settings.edition) to AWS (aws), GCP (gcp), or AWS GovCloud (aws_govcloud) in your log streaming integration. See Splunk Cloud Settings properties.
Custom links for personal information and password management on End-User Dashboard
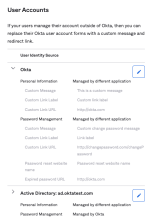
If you manage end users' personal information and passwords in an external application, you can configure that application as the User Identity Source in Customizations. Using this setting, you can provide a link to the application in the End-User Dashboard. When end users click the link, they're taken to the third-party page to update their information and password.
This setting is only applicable to the end users whose personal information and password are managed outside of Okta (for example, Active Directory). See Customize personal information and password management.
You must upgrade to Sign-in Widget version 7.3.0 or higher to use this feature. See the Sign-In Widget Release Notes.
Run delegated flows from the Admin Console
With delegated flows, admins can be assigned the ability to run Okta Workflows directly from the Admin Console. Flows that are delegated to an admin appear on the Delegated Flows page where they can be invoked without signing in to the Workflows Console. This gives super admins more granular control over their admin assignments. See Delegated flows.
Full Featured Code Editor for error pages
Full Featured Code Editor integrates Monaco code editing library into the Admin Console to make editing code for error pages more efficient and less reliant on documentation. Developers can write, test, and publish code faster with the better syntax highlighting, autocomplete, autosave, diff view, and a Revert changes button. See Customize the Okta-hosted error pages.
Phishing-resistant authentication
Phishing-resistant authentication detects and prevents the disclosure of sensitive data to fake applications or websites. When users authenticate with Okta FastPass on managed devices, they’re protected from phishing attacks. See About MFA authenticators.
Custom app login
Custom app login is now available to limited customers in Identity Engine. Only orgs that actively used the feature in Classic Engine before they upgraded may continue to do so. Orgs that don't use custom app login should continue to use the Okta-hosted sign-in experience or configure IdP routing rules that redirect users to the appropriate app to sign in. See Custom app login.
New user enumeration prevention options
Okta now allows admins to enable user enumeration prevention for authentication or recovery flows, or both. This enhancement blocks attackers from attempting to identify user accounts and authenticator enrollments in a more granular way. See User enumeration prevention.
Enhancements
Enhanced MFA System Log event
The new user.mfa.factor.activate System Log event for FIDO2 (WebAuthn) enrollments has been enhanced. Whenever a user enrolls in the FIDO2 (WebAuthn) authenticator, Okta now records the credential's AAGUID value, whether the credential can be backed up, and allow-list authenticator group names that include the make and model of the authenticator device that was enrolled.
Log Streaming status messages
Log streaming status messages now include a prefix related to the log streaming operation.
Updated AWS EventBridge supported regions for Log Stream integrations
The list of supported AWS EventBridge regions has been updated based on configurable event sources. See the list of available AWS regions for Log Stream integrations.
Informative error messages for SAML sign-in
Error messages presented during a SAML sign-in flow now provide an informative description of the error along with a link to the sign-in page.
Early Access Features
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-493073
An authentication policy error message wasn't applicable in some use cases.
OKTA-493531
Users were unable to sign in using passcodes when Permit Automatic Push for Okta Verify Enrolled Users was enabled.
OKTA-501372
The People page used an incorrect field name as the sorting key.
OKTA-540894
Users who attempted to cancel a Sign in with PIV/CAC card request weren't redirected back to the custom domain.
OKTA-544814
Clicking Show More in the tab resulted in an Invalid search criteria error.
OKTA-552341
After users completed an MFA challenge and signed out, their full Okta username appeared on the Sign In page.
OKTA-554006
Clicking Save and Add another to add new attributes on the Profile Editor page didn’t consistently function as expected.
OKTA-555768
Improved New Device Behavior Evaluation incorrectly identified a previously used device as new when the admin accessed the Okta Admin Dashboard.
OKTA-560752
In the Admin Console, the Japanese version of the MFA Enrollment by User report contained some English.
OKTA-566469
The Coupa integration URL displayed under the application Sign On tab was incorrect.
OKTA-567511
Users weren’t assigned to applications through group assignments following an import from AD into Okta.
OKTA-567991
Signing in to the End-User Dashboard through a third-party IdP displayed an incorrect error message if the password had expired.
OKTA-568319
In the End-User Dashboard, the link to access the Okta Browser Plugin installation guide redirected users to a broken page.
OKTA-572600
Sometimes, custom email domain configurations didn’t appear on the Domains page in the Admin Console.
OKTA-572333
After an org upgraded to Identity Engine, some apps with the default app sign-on policy weren’t assigned to the Classic Migrated policy.
OKTA-468178
In the Tasks section of the End-User Dashboard, generic error messages were displayed when validation errors occurred for pending tasks.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
Paychex Online (OKTA-573082)
Applications
Application Update
The HubSpot Provisioning integration is updated with a new HubSpot Roles attribute. See Configuring Provisioning for HubSpot.
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Better Stack: For configuration information, see Integrate Okta SSO & SCIM with Better Stack.
- Cafe: For configuration information, see Okta SCIM Configuration Guide.
- Kakao Work: For configuration information, see Kakao Work SCIM Setup.
- Torii: For configuration information, see Torii's SCIM Setup with Okta.
OIDC for the following Okta Verified applications:
-
Craftable: For configuration information, see Single Sign On with Okta.
-
LeadLander: For configuration information, see the LeadLander Okta configuration guide.
-
Loxo: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Mobius Conveyor: For configuration information, see Okta SSO Configuration Guide.
-
MyInterskill LMS: For configuration information, see SSO – Okta Configuration Guide.
-
ngrok: For configuration information, see Okta SSO (OpenID Connect).
-
Paramify: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
Weekly Updates
Fixes
General Fixes
OKTA-537710
Users on M1 MacBooks were unable to sign in to organizations provisioned with an OS-specific workflow.
OKTA-550348
Device authorization returned an error if the authentication policy had a condition for registered devices.
OKTA-552996
If JIT provisioning wasn’t enabled for a SAML IdP, users who tried to sign in received an error message instead of being redirected to the Okta sign-in page.
OKTA-556133
End users received email notifications of new sign-on events even though such notifications were disabled in the org security settings.
OKTA-561269
The YubiKey Report wasn’t generated when certain report filters were applied.
OKTA-564518
The ordering of authenticators on the Verify with something else page of the Sign-In Widget sometimes changed when the page was accessed again.
OKTA-565300
Accessibility issues on the password verification page of the End-User Dashboard prevented screenreaders from reading the text.
OKTA-565984
Case sensitivity caused usernames sent in SAML 2.0 IdP assertions not to match usernames in the destination org if a custom IdP factor was used and the name ID format was unspecified.
OKTA-566892
Sometimes MFA prompts overlapped portions of the browser sign-in pages.
OKTA-567776
Super admins weren't able to access the profile of deactivated users in some Preview environments.
OKTA-572091
Some QR codes for Okta Verify enrollment weren't scannable by iOS devices.
OKTA-572416
The Help Center link on the Resources menu directed users to the wrong URL.
OKTA-574624
In , the Org Admin description was incorrect.
App Integration Fixes
The following SWA apps weren't working correctly and are now fixed:
-
Adobe Stock (OKTA-564445)
-
Adyen (OKTA-561677)
-
Airbnb (OKTA-559114)
-
AlertLogic (OKTA-560876)
-
American Express @ Work (OKTA-565294)
-
BlueCross BlueShield of Texas (OKTA-564224)
-
Drilling Info (OKTA-558048)
-
Empower (OKTA-552346)
-
Endicia (OKTA-557826)
-
Glassdoor (OKTA-564363)
-
hoovers_level3 (OKTA-562717)
-
MailChimp (OKTA-554384)
-
MY.MYOB (OKTA-553331)
-
myFonts (OKTA-566037)
-
OpenAir (OKTA-545505)
-
Paychex (OKTA-561268)
-
Paychex Online (OKTA-564325)
-
Regions OnePass (OKTA-568163)
-
Truckstop (OKTA-552741)
-
VitaFlex Participan (OKTA-562503)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Akamai Enterprise Application Access: For configuration information, see SCIM provisioning with Okta.
- ArmorCode: For configuration information, see SCIM Configuration Guide Instructions.
SAML for the following Okta Verified applications:
-
Articulate 360 (OKTA-544737)
-
Kakao Work (OKTA-556713)
-
Pleo (OKTA-564884)
-
Tower (OKTA-567818)
Generally Available
Fixes
General Fixes
OKTA-431900
The People > Enroll FIDO2 Security Key button was visible to admins who didn’t have permission to enroll authentication factors.
OKTA-452990
When a user clicked the Admin button on the End-User Dashboard using a mobile device, Okta didn't check if the user's session was still active.
OKTA-495146
The MFA Usage report and various API responses displayed different authenticator enrollment dates for users.
OKTA-503419
App catalog search results didn't include SCIM functionality labels.
OKTA-516494
Group imports from AD to Okta sometimes failed.
OKTA-558628
Some orgs experienced an error when using legacy endpoints.
OKTA-566637
The agentless DSSO just-in-time provisioning flow imported ineligible AD groups in to Okta.
OKTA-566891
Users with multiple Windows Okta Verify enrollments received an error when they attempted to log in with Windows Okta Verify.
OKTA-568575
Orgs couldn’t upgrade to Identity Engine if their app sign-on policy rules contained On Network or Off Network location settings.
OKTA-572089
Browsing the Provisioning tab for an app triggered a System Log update.
OKTA-574711
The sign-in process didn't exit after users selected No, It's Not Me in Okta Verify.
OKTA-574890
When the End-User Dashboard was in grid view, screen readers couldn't recognize apps as clickable links.
OKTA-576067
Custom domains couldn't be validated if there were uppercase characters in a subdomain.
OKTA-578439
Some event hook requests failed to send in Preview orgs.
OKTA-579157
For orgs that were updated to SCIM 2.0, Workplace by Facebook profile pushes that included the manager attribute failed.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Adobe Creative (OKTA-555215)
-
Asana (OKTA-566187)
-
ManageEngine Support Center Plus (OKTA-529921)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Samsung Knox Manage: For configuration information, see Configure Knox Manage SCIM Connector and Okta for automatic user provisioning.
-
Shortcut: For configuration information, see Configuring Okta to Manage Shortcut Users with SCIM.
-
Ziflow: For configuration information, see SCIM provisioning with Okta.
SAML for the following Okta Verified applications:
-
Scalr.io (OKTA-552065)
-
Trusaic (OKTA-559106)
OIDC for the following Okta Verified applications:
-
Activaire Curator: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Arrivy: For configuration information, see How to set up OIDC Okta Single sign-on with Arrivy.
-
ConductorOne: For configuration information, see Set up ConductorOne using Okta,
-
HacWare: For configuration information, see SSO Login via Okta and HacWare.
-
Jatheon Cloud: For configuration information, see How to Set Up Okta SSO Integration.
-
Kadence: For configuration information, see Okta Single Sign-On (SSO) Setup Guide.
-
Oort Identity Security: For configuration information, see Okta Integration Network SSO Instructions.
-
Skye: For configuration information, see Single Sign-On (SSO) - Okta.
-
Solarq: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Tabled: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Tackle.io: For configuration information, see Okta SSO Setup Guide.
-
TaskCall: For configuration information, see Okta Integration Guide.
-
TestMonitor: For configuration information, see How to set up Okta Single Sign-on in TestMonitor.
March 2023
2023.03.0: Monthly Production release began deployment on March 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
Okta LDAP agent, version 5.16.0
This version of the agent contains:
- Use of FIPS 140-2 validated cryptographic security modules
- bc-fips: Version 1.0.2.3
- bcpkix-fips: Version 1.0.6
- bctls-fips: Version 1.0.13
- Support for LDAP agent auto-update
- This version allows support for LDAP agent auto-update. Stay tuned for the self-service EA feature within Okta that will enable LDAP agent auto-update when available.
- Upon agent installation on Linux platforms, we now grant the OktaLDAPService user permission to automatically install the newest agent version using the auto-update feature.
- Bug fixes
- Security enhancements
Agents page added to the navigation panel
The operational status of org agents can now be viewed by selecting the Agents page from the navigation panel. See View your org agents' status.
Device management signal collection
Device management attestation signals are collected only when an associated endpoint management configuration is present.
Rate limit increased for Event Hooks
The number of events that can be delivered to Event Hooks is now 400,000 events per org, per day. See Hooks.
New error pages
Authenticator enrollment flow errors now redirect to user-friendly error pages.
Updated Okta logo
New Okta branding is now used for the Admin Console, the sign-in page, and the browser page flavicon.
Manage the Okta loading animation for custom apps
You can now disable the default Okta loading animation (interstitial page) that appears when users are redirected to custom applications. End users are shown a blank interstitial page, instead. This allows you to present a more branded end user experience. For more information, see
SAML logout metadata
SAML app integration metadata details now includes logout URL information when Single Logout is enabled.
OIN Manager enhancements
The OIN Manager now includes text to support API Service integrations.
Enhanced Admin Console search
The Admin Console search now displays your search results in a user-friendly drop-down list. The list provides Top results, People, Apps, and Groups filters so you can quickly and easily find what you’re looking for. See Admin Console search.
Improvements to self-service account activities for AD and LDAP users
Previously, the self-service unlock (SSU) and self-service password reset (SSPR) flows created unnecessary friction for AD and LDAP users. This enhancement introduces a seamless magic link in emails sent to unlock accounts and reset passwords. Users no longer need to provide consent when using the same browser. In addition, after successfully unlocking their account, clicking the email magic link counts towards the application's assurance policy. After the assurance requirements are met, the user is signed in directly to the application. See Configure the Email authenticator.
Optional consent settings for OAuth 2.0 scopes
OAuth 2.0 Optional Consent provides an Optional setting that enables a user to opt in or out of an app's requested OAuth scopes. When Optional is set to true, the user can skip consent for that scope. See Create API access scopes .
SAML setup parameters
More setup parameters are now visible when configuring SAML as a sign-in method for app integrations. See Configure Single Sign-On options.
Log Streaming
While Okta captures and stores its System Log events, many organizations use third-party systems to monitor, aggregate, and act on event data.
Log Streaming enables Okta admins to more easily and securely send System Log events to a specified system such as Amazon Eventbridge in real time with simple, pre-built connectors. They can easily scale without worrying about rate limits, and no admin API token is required. See Log streaming.
OIDC Identity Providers private/public key pair support
Previously, Okta only supported the use of client secret as the client authentication method with an OpenID Connect-based Identity Provider. Okta now supports the use of private/public key pairs (private_key_jwt) with OpenID Connect-based Identity Providers. Additionally, the Signed Request Object now also supports the use of private/public key pairs. See Create an Identity Provider in Okta.
Early Access Features
Verify Zoom users with Okta
Zoom users can now attest and verify a user’s identity between two independent parties using Okta-signed tokens.
Fixes
OKTA-520182
Self-service account unlock sometimes displayed an error message even though inputs were correct.
OKTA-530926
Authentication sometimes failed for LDAP users due to a null pointer exception. The issue is fixed in LDAP agent version 5.16.0.
OKTA-544910
Target types for authentication policies and profile enrollment rules in the System Log didn’t match all policy types.
OKTA-548568
Password validation caused an unexpected error during a self-service password reset.
OKTA-554109
Read-only admins were able to edit application integration pages.
OKTA-561769
A user with a Custom Administrator role could make changes to the End-User Dashboard but couldn't preview the dashboard.
OKTA-562113
Auto-population of non-English variable names in the Profile Editor didn't work as expected.
OKTA-564673
Empty groups caused LDAP delegated authentication testing to fail.
OKTA-578615
Some users could request a new one-time passcode after exceeding the limit for failed MFA attempts.
OKTA-580307
The Sign-in Widget sometimes failed to load for testing LDAP authentication.
OKTA-581530
Missing logos on the Groups page were displayed as broken links.
Applications
New Integrations
New SCIM integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- BeProduct: For configuration information, see How to set up Okta Single Sign-On integration.
- Forkable: For configuration information, see How to set up Okta SCIM integration.
- RudderStack: For configuration information, see Okta SCIM Configuration.
- scalr.io: For configuration information, see Configure Okta.
SAML for the following Okta Verified application:
-
Wistia (OKTA-561362)
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Adobe (OKTA-569857)
-
Adobe Stock (OKTA-564445)
-
Brex (OKTA-573146)
-
Criteo (OKTA-577154)
-
CTCC OncoEMR (OKTA-576358)
-
Lucidchart (OKTA-566188)
-
MyFonts (OKTA-566037)
-
Washington Post (OKTA-575907)
Weekly Updates
Generally Available
Fixes
OKTA-401654
Users were able to perform an unlimited number of Security Question authentication attempts.
OKTA-464288
SMS customization wasn't restricted in free developer orgs.
OKTA-544970
When orgs used email template injection, some internal class information was visible in the message.
OKTA-551444
Device EDR rules that used Okta Expression Language were ignored if EDR signals weren't collected.
OKTA-562755
On the Admin Dashboard, the Total admins and Individually assigned counts were incorrect.
OKTA-565487
After an org was upgraded to Identity Engine, email was auto-enrolled as an authenticator for deactivated users.
OKTA-567399
A deactivated Identity Provider couldn't be reactivated.
OKTA-567906
Admins were able to configure an authenticator enrollment policy that allowed the Okta Verify Push mode but didn't allow the one-time password mode.
OKTA-570664
BambooHR reported an error when Okta attempted to update a value using the value of a custom attribute.
OKTA-576483
Admins weren't able to add a network zone with the name BlockedIPZone.
OKTA-578561
Enrollment policy rules weren't applied when the user enrolled an authenticator from the End User Settings page.
OKTA-578983
During self-service registration, users who didn’t complete enrollment of optional authenticators were blocked from signing in to their apps.
OKTA-584624
Some orgs with custom domains were unable to upgrade to Identity Engine.
OKTA-585688
The client-initiated backchannel authentication flow didn't appear as a grant type option for OIDC native app integrations.
OKTA-585800
Some Cornerstone profiles failed to import due to missing information.
OKTA-589114
When orgs used daylight savings time, the Admin Dashboard and the System Log events timestamps were one hour behind.
Applications
Application update
The Front SCIM integration is updated to support group push.
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
O'Reilly Learning Platform: For configuration information, see Configure SCIM for user provisioning.
OIDC for the following Okta Verified applications:
- BrandShield: For configuration information, see BrandShield Okta Single-Sign-On (SSO) - Integration Guide.
- Edify: For configuration information, see Set up an Okta SSO configuration (Edify Console).
- ellie.ai: For configuration information, see Okta configuration guide for ellie.ai.
- HaileyHR: For configuration information, see Integration with Okta.
SAML for the following Okta Verified application:
-
ASP.NET (OKTA-575640)
App Integration Fixes
The following SWA apps weren't working correctly and are now fixed:
-
Acorns (OKTA-579034)
-
GoToMeeting (OKTA-566182)
-
PayPal (OKTA-562742)
Generally Available
Fixes
OKTA-503099
Admins were able to modify the auth_time claim for an access token using a token inline hook.
OKTA-535435
During password resets, some text strings in the Sign-In Widget weren't translated.
OKTA-545664
Active Directory Single Sign-On couldn’t be completed in iFrames.
OKTA-565953
After iPhone users signed in to a SAML app through Okta, the app opened in a browser window instead of the native app window.
OKTA-566659
DocuSign group pushes failed when removing users from a group.
OKTA-568170
Some orgs couldn't disable the New Sign-On Notifications email.
OKTA-568376
Users couldn't enroll an IdP as an authentication factor if their username didn't match the case of the username in their IdP profile.
OKTA-579088
In Agents > On-premise, the Description link next to each of the agents was incorrect.
OKTA-584216
A suffix was added to the application label for new Onspring instances.
OKTA-587063
An older version of the OAuth library was included in the Okta Provisioning agent. The issue is fixed in Okta Provisioning agent 2.0.14.
OKTA-588262
The favicons for the Admin Console and End-User Dashboard were misaligned.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Spiro.ai: For configuration information, see Connecting your Okta Account with Spiro.
- Venue: For configuration information, see Integrating Venue with Okta.
SAML for the following Okta Verified application:
-
Laurel (OKTA-586151)
OIDC for the following Okta Verified application:
- Fullview: For configuration information, see Fullview Okta configuration guide.
App Integration Fix
The following SWA app wasn't working correctly and is now fixed:
-
Poll Everywhere (OKTA-585747))
Fixes
OKTA-573597
In Identity Engine orgs that were upgraded from Classic Engine, authentication policy rules that included groups and users weren't applied correctly.
OKTA-576159
On the IdP configuration page, searching for groups under JIT Settings sometimes returned an error.
OKTA-581158
System Log events for manual imports showed that the import was scheduled by Okta.
OKTA-582181
When a user requested a password reset and user enumeration prevention was enabled, the password reset error was incorrect.
OKTA-585107
The hidden permissions count on the Edit role page was incorrect.
OKTA-585478
App sign-on events with usernames that exceeded 100 characters weren't always added to the System Log.
OKTA-587347
On mobile devices, users with long email addresses couldn’t see all the options in their settings dropdown menu.
OKTA-588528
When users attempted to connect to a remote server using an Okta Verify Push prompt and Number Matching Challenge wasn't enabled, an error occurred.
OKTA-592074
Screen readers read apps on the End-User Dashboard as buttons instead of links.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Mitimes: For configuration information, see IT Admin - SSO - Okta.
- Envoy: For configuration information, see Envoy Okta App Integration Configuration Guide.
- Insightly: For configuration information, see Setting Up SAML and SCIM Integrations.
- Riskpal: For configuration information, see Riskpal integration with okta.
- TrackTik: For configuration information, see Set up and use provisioning for Okta.
- Truly: For configuration information, see SCIM Configuration Guide.
- Xledger: For configuration information, see Configure SCIM Provisioning between Xledger and Okta.
SAML for the following Okta Verified applications:
-
Bitdefender GravityZone (OKTA-575873 - Okta-hosted instructions)
-
CorporateFitness.app (OKTA-575873 - Okta-hosted instructions)
-
RevSpace: For configuration information, see How to Configure SAML 2.0 for RevSpace.
OIDC for the following Okta Verified applications:
- AcquireTM: For configuration information, see AcquireTM Single Sign-on Setup Guide.
- NordPass: For configuration information, see How to set up SSO with Okta for organization members.
- Xledger: For configuration information, see Configure SSO between Xledger and Okta.
API service app for the following Okta Verified application:
- Calero - SaaS Expense Management: For configuration information, see Calero.com Okta SSO Connector Setup.
April 2023
2023.04.0: Monthly Production release began deployment on April 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
Okta AD agent, version 3.14.0
This version of the agent contains the following changes:
-
Security enhancements.
-
Bug fixes.
-
Installer will show a warning if the service account isn't a member of Pre-Windows 2000 Compatible Access.
-
Migration of the Windows installer from Internet Explorer to Edge.
The installer now requires Edge WebView2. WebView2 is downloaded automatically during the agent installation if your machine is connected to the internet. If not, you must manually install it before installing the new agent version. See Okta Active Directory agent version history.
Okta Provisioning agent, version 2.0.14
This version of the agent contains security fixes. See Okta Provisioning agent and SDK version history.
OAuth 2.0 authentication for inline hooks
Okta inline hook calls to third-party external web services previously provided only header-based authentication for security. Although sent with SSL, the header or custom header authentication didn’t meet more stringent security requirements for various clients and industries.
To improve the security of inline hooks, Okta now supports authentication with OAuth 2.0 access tokens. Tokens ensure secure calls to external web services.
When creating inline hooks in the Admin Console (or by API), administrators or developers can now select OAuth 2.0 authentication and choose between two methods of OAuth 2.0: Client Secret or Private Key. A new Key Management API and Admin Console page is also available to create public/private key pairs for use with OAuth 2.0 inline hooks. See Manage keys.
Using the OAuth 2.0 framework provides better security than Basic Authentication, and is less work than setting up an IP allowlisting solution. Clients also have the ability to use access tokens minted by their own custom authorization servers to guarantee that Okta is calling their client web services and it isn't triggered by any external actors. See Add an inline hook
API Service Integrations
Using a more secure OAuth 2.0 connection than access tokens, this integration type uses the Core Okta API to access or modify resources like System Logs, apps, sessions, and policies. See API Service Integrations.
OIN Manager support for Workflow Connector submission
ISV_PORTAL_CONNECTOR_SUBMISSIONS GA PREVIEW 2023.03.0 GA PROD 2023.04.0
Okta Workflows is a no-code, if-this-then-that logic builder that Okta orgs can use to automate custom or complex employee onboarding and offboarding flows in your application. You can now publish Workflow connectors that you create with the [Workflows Connector Builder](connector-builder.htm) in the Okta Integration Network (OIN) catalog. Publishing a Workflows Connector with Okta allows your customers to deeply integrate your product with all other connectors in the catalog. Submit your Workflow Connector by using the OIN Manager. See Submit an integration for Workflows connectors.
Configurable rate limits available for OAuth 2.0 apps
Rate limit violations mainly occur on authenticated endpoints. Currently, it isn't clear which OAuth 2.0 authenticated app consumes all the rate limits for an org. This increases the risk that one app consumes the entire rate limit bucket. To avoid this possibility, Okta admins can now configure how much rate limit capacity an individual OAuth 2.0 app can consume by editing the Application rate limits tab for each app. By setting a capacity on individual OAuth 2.0 apps, Okta admins have a new tool to monitor and investigate rate limit violations, and have the ability to view rate limit traffic generated by individual OAuth 2.0 apps. See Rate limit dashboard bar graph.
Authentication policy rule enhancement
When admins select the Any 1 factor type option in an authentication policy, the Possession factor constraints are section isn't shown. This helps guide admins in making configuration choices that achieve the desired level and type of assurance. There is also a new advanced mode view that shows the JSON code of the authentication policy rule. It appears when admins edit a rule that was created before this feature was enabled, when their org has any authentication policy rules in which the Any 1 factor type option was selected, and when possession factor constraints were configured. This provides admins with a summary of the options that were selected before this feature was activated. See Add an authentication policy rule.
Support added for DPoP with service apps
Okta now supports Demonstrating Proof-of-Possession for service apps. However, service apps can provide the same level of security by using private_key_jwt for client authentication. See Configure OAuth 2.0 Demonstrating Proof-of-Possession and Client authentication.
Multiple IdP profiles in Google Workspace
The Google Workspace integration now supports multiple IdP profiles. See How to Configure SAML 2.0 for Google Workspace.
Okta FastPass enhancements
Okta FastPass silently collects device signals in every authentication attempt.
Early Access Features
Demonstrating Proof-of-Possession
OAuth 2.0 Demonstrating Proof-of-Possession (DPoP) is a security feature that adds an extra layer of protection to OAuth 2.0 access tokens. It enables the client to demonstrate that it possesses a particular key or secret associated with the access token. OAuth 2.0 DPoP can help prevent certain attacks, such as token theft or token replay attacks, where an attacker intercepts a legitimate access token and uses it to gain unauthorized access to a protected resource. See Create OIDC app integrations.
Third-generation Sign-In Widget
The third-generation Sign-In Widget is more accessible and uses modern frameworks that provide a better end user and developer experience. Okta built the experience from the ground up for Identity Engine, which allows for better velocity, customization, accessibility, and globalization. See Sign-In Widget (third generation).
Okta LDAP Agent automatic update support
Admins can now initiate or schedule automatic updates to Okta LDAP agents from the Admin Console. With agent auto-update functionality, admins no longer need to manually uninstall and then reinstall Okta LDAP agents when a new agent version is released. Agent auto-updates keep your agents up to date and compliant with the Okta support policy, and help ensure your org has the latest Okta features and functionality. Single or multiple agents can be updated on demand, or updates can be scheduled to occur outside of business hours to reduce downtime and disruption to users. See Automatically update Okta LDAP agents.
Import users to Office 365 using Microsoft Graph API
This feature allows Okta to process imports using the Microsoft Graph API. This background process doesn’t change existing procedures and makes imports more scalable, supporting Microsoft 365 tenants with larger numbers of users, groups, and group memberships. See Import users to Office 365 using Microsoft Graph API.
Fixes
OKTA-511637
If users clicked the reveal password icon in the Sign-In Widget before they entered their password, blank spaces were removed upon submission.
OKTA-528821
Verification pages in the Sign-In Widget were inconsistent for the self-service password recovery and self-service unlock flows.
OKTA-557115
SSO on mobile devices where an OIDC token exchange occurred between two apps sometimes failed for the second app.
OKTA-562885
Some users were prompted to sign in with a username and password even if Sign in with Okta FastPass was selected.
OKTA-567476
Users could not sign in to Office 365 using SWA due to an error in the SSO rule.
OKTA-570362
The End-User Dashboard displayed email confirmation notifications for users who didn't change their primary email.
OKTA-573667
The dates on the Agent auto-update settings page in the Admin Dashboard were missing the year.
OKTA-578369
The Expired Password URL was displayed instead of the password reset flow when a user's password was about to expire.
OKTA-581516
HTML wasn't formed correctly in SAML responses.
OKTA-586482
Sometimes users couldn't enroll in or set up On-Prem MFA or RSA SecurID.
OKTA-588390
Token Preview for custom authorization servers failed for group claims with more than 100 groups.
OKTA-592588
The Routing rules tab on the Identity Providers page wasn't hidden for users without admin permissions.
OKTA-593452
The Everyone group in Okta couldn't be imported through the Okta Org2Org app.
Applications
New Integrations
SAML for the following Okta Verified applications:
- WalkMe: For configuration information, see WalkMe SAML Integration with Okta.
- WalkMe (encrypted assertions): For configuration information, see WalkMe SAML Integration with Okta.
OIDC for the following Okta Verified application:
- WalkMe: For configuration information, see WalkMe OpenID Connect (OIDC) Integration with Okta.
Weekly Updates
Fixes
-
OKTA-529298
Renaming an individually selected organizational unit in Active Directory caused it to be unselected in Okta when imported.
-
OKTA-571266
Token exchange errors occurred when users selected Keep me signed in during sign-in flows for Native SSO or the Okta AWS CLI.
-
OKTA-573682
Some of the widgets on the Admin Dashboard didn’t use the correct date and time format.
-
OKTA-578310
Some labels and error messages related to assigning applications were untranslated.
-
OKTA-584757
Sometimes group push operations to ServiceNow failed.
-
OKTA-586222
If orgs upgraded to Identity Engine with a Factor Sequencing chain, users couldn't enroll authenticators when they signed in.
-
OKTA-586995
Some text strings in the Authenticator enrollment pages weren't translated.
-
OKTA-588493
Some text strings in the Authentication policy Add Rule dialog weren't translated.
-
OKTA-592839
In orgs with user enumeration prevention enabled, users in a staged status received an error when they tried to sign in.
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Hiver: For configuration information, see Configuration of Okta integration.
- Productboard: For configuration information, see Setting up SCIM provisioning with OKTA.
SAML for the following Okta Verified application:
-
Obsidian Security: For configuration information, see How to Configure SAML 2.0 for Obsidian Security.
OIDC for the following Okta Verified application:
-
Sclera: For configuration information, see Okta Integration with Sclera.
App Integration Fix
The following SWA app wasn't working correctly and is now fixed:
-
Adobe Stock (OKTA-564445)
Generally Available
Okta Verify for Windows EXE bundle
On the Admin Console Downloads page, the Okta Verify for Windows app is now available as a single EXE bundle that includes MSI files. A separate MSI file is no longer available for this app. See Deploy Okta Verify to Windows devices.
Fixes
-
OKTA-475223
On the Admin Dashboard, the Tasks menu Pending and Complete labels overlapped with the dropdown icon.
-
OKTA-500841
RADIUS server agent was incorrectly listed among Disconnects and reconnects under System notifications.
-
OKTA-541966
The Back to sign in link sometimes failed to return the user to the sign-in page.
-
OKTA-549472
In identifier-first sign-in flows, users weren’t notified when they exceeded the password lock out setting.
-
OKTA-555152
The shortcut URL /login/default didn't always go to the End User Dashboard.
-
OKTA-564388
When Multibrand was enabled, orgs couldn’t add an email domain that they’d previously deleted.
-
OKTA-566659
Pushing group changes to Docusign failed when a member was removed from a group or a group push mapping was removed in Okta.
-
OKTA-567763
After orgs were upgraded to Identity Engine, the IWA tab and IWA Agents were still displayed on the Agents page available from the Admin Dashboard.
-
OKTA-568489
Pushing groups for provisioning to Office 365 failed if the groups already existed.
-
OKTA-568851
Some URLs on multifactor authentication app pages pointed to incorrect destinations.
-
OKTA-571178
When orgs using custom sign-out URLs upgraded to Identity Engine, users received misleading error messages.
-
OKTA-573390
When users attempted to edit their profiles, they received an Okta Verify Push prompt and their profile page remained in read-only mode after they responded to the prompt. If they tried to edit their profile again, users encountered an authentication loop.
-
OKTA-579360
Users were still active in the hub org after being deactivated in a spoke org.
-
OKTA-583585
Admins were unable to update passwords for SWA apps in orgs with certain configurations.
-
OKTA-585424
When session authentication method references (session.amr) were expected in SAML responses, multiple channel authentication (mca) information was missing for IdP plus phone authentication.
-
OKTA-585741
Empty values for attribute statements in SAML assertions didn't remove previously specified values.
-
OKTA-586713
The variable ${baseURL} in the HTML for some email templates didn't resolve in the browser.
-
OKTA-587325
After activating their accounts, users who enrolled through the Sign up link received an error if they clicked Set up later on the Security methods page.
-
OKTA-588140
The Delegated flows page was visible to orgs that hadn't configured any delegable flows.
-
OKTA-588408
Admins could configure the Maximum Okta session lifetime setting for a global session policy rule that denied access.
-
OKTA-591800
When the sign-in page was edited using the code editor, the event type system.custom_error.update was logged.
-
OKTA-592655
After upgrading to Identity Engine, production orgs failed to redirect users to Salesforce for SP-initiated SSO.
-
OKTA-593131
Some attributes previously added to user profiles from incoming SAML responses weren't cleared when the attribute was later omitted.
-
OKTA-594051
Sometimes new users created through self-service registration applications received inaccurate errors when they signed in.
-
OKTA-594268
Multiple Smart Card IdPs couldn't be added or updated on the Smart Card IdP Authenticator Settings page.
-
OKTA-595042
A successful MFA that followed unsuccessful MFA attempts mistakenly locked out users.
-
OKTA-596437
When the API Service Integration feature was disabled, a query for inactive app integrations incorrectly returned a list with revoked API service integrations.
-
OKTA-597697
When Multibrand was enabled, orgs couldn’t reset the default application for the Sign-In Widget.
-
OKTA-599024
In Okta Expression Language, user.status returned incorrect values.
-
OKTA-599062
On the Push Groups to Active Directory page Okta admins were unable to view all the organizational unit.
-
OKTA-599243
When the redesigned resource editor feature was enabled, admins could save the Add Resource screen without selecting a resource.
-
OKTA-602563
In orgs that were upgraded to Identity Engine, some users received a 404 error when they opened the Okta Verify app to approve a push notification.
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
KSOC: For configuration information, see KSOC Configuration Guide (you need KSOC permissions to view).
-
MANTL: For configuration information, see Okta Provisioning Using SCIM.
-
Salesbricks: For configuration information, see Okta OIN configuration guide.
SAML for the following Okta Verified applications:
-
ProcessBolt AUS: For configuration information, see ProcessBolt AUS Okta Config Guide.
-
TimeRewards: For configuration information, see Okta Single Sign-On (SSO) integration.
-
WebCE (OKTA-571275)
OIDC for the following Okta Verified applications:
-
Agora: For configuration information, see Setting up Okta SSO.
-
MANTL: For configuration information, see Okta OIDC SSO Integration.
-
TimeRewards: For configuration information, see Okta Single Sign-On (SSO) integration.
App Integration Fix
The following SWA app wasn't working correctly and is now fixed:
-
Louisiana Medicaid (OKTA-578791)
Fixes
-
OKTA-570851
Some app provisioning error strings weren't translated.
-
OKTA-578140
End users could delete all of their enrolled factors.
-
OKTA-587935
If a new user abandoned and then resumed an activation flow, they received an activation email with the ${oneTimePassword} macro visible.
-
OKTA-588661
When users clicked expired email sign-in tokens, they received incorrect error messages.
-
OKTA-591232
Logos weren't correctly displayed on email templates.
-
OKTA-597761
Some unsupported apps were included in the authentication policy mapping count.
-
OKTA-599684
When Active Directory users were added through an import or JIT provisioning, their application groups were retrieved from an incorrect domain. This caused an internal error that prevented users from signing in to Okta.
-
OKTA-601320
When an OpenID Connect authorization request included an empty IdP query parameter, users were sent to a blank sign-in page.
-
OKTA-604536
An older library was being used by the toolkit used by Okta Confluence Authenticator and Okta Jira Authenticator. The issue is fixed in version 3.2.2 of the toolkit.
-
OKTA-607199
ThreatInsight temporarily prevented non-malicious users from accessing Okta.
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Agora: For configuration information, see Setting up Okta SCIM provisioning.
-
anecdotes: For configuration information, see SCIM Provisioning of Users with OKTA.
-
Huntress: For configuration information, see SAML SSO Setup for Okta.
-
MaestroQA - EU: For configuration information, see MaestroQA/Okta SCIM configuration guide.
-
Reclaim.ai - EU: For configuration information, see Okta SSO Setup Guide - App Catalog.
-
SGNL: For configuration information, see Configuring Single Sign-On with Okta.
SAML for the following Okta Verified applications:
-
MaestroQA - EU: For configuration information, see How to Configure SAML 2.0 for MaestroQA-EU.
-
TalentQuest: For configuration information, see How to Configure SAML 2.0 for TalentQuest.
May 2023
2023.05.0: Monthly Production release began deployment on May 15
* Features may not be available in all Okta Product SKUs.
Generally Available Features
Okta AD agent, version 3.15.0
This version of the agent contains the following changes:
-
Bug fixes. Active Directory (AD) agent auto-update health check caused auto-update to fail when upgrading from version 3.13.0 to 3.14.0.
Okta On-Prem MFA agent, version 1.7.0
This version includes support for extended client session timeout. See Install the agent.
Confluence Authenticator, version 3.2.2
This release contains security fixes. See Okta Confluence Authenticator version history.
Okta Jira Authenticator, version 3.2.2
This release contains security fixes. See Okta Jira Authenticator Version History.
Import users to Office 365 using Microsoft Graph API
This feature allows Okta to process imports using the Microsoft Graph API. This background process doesn’t change existing procedures and makes imports more scalable, supporting Microsoft 365 tenants with larger numbers of users, groups, and group memberships. See Import users to Office 365 using Microsoft Graph API. This feature will be gradually made available to all orgs.
OAuth 2.0 On-Behalf-Of Token Exchange
Exchange helps retain the user context in requests to downstream services. It provides a protocol approach to support scenarios where a client can exchange an access token received from an upstream client with a new token by interacting with the authorization server. See Set up OAuth 2.0 On-Behalf-Of Token Exchange.
Number Matching Challenge for Okta Verify
When an org enables the Number Matching Challenge feature, it’s always enforced for Okta Verify during self-service password resets.
Okta Expression Language matches operator deprecated
The Okta Expression Language matches operator that is used to evaluate a string against a regular expression is deprecated. This feature is currently enabled by default for new orgs only.
Okta administrators group for all org admins
A default Okta administrators group is now available in every Okta org. The new group allows you to create sign-on policies that automatically apply to all admins in your org. See About groups.
Improved email magic link authentication experience
Email magic links have been enhanced to allow end users to authenticate in two different contexts. They can authenticate in the same location where they click the link and quickly return to the application context. Or, if the end user clicks the link in a different browser, they can enter a one-time password to proceed with authentication. Previously when using email magic links to sign in to an application, end users had to return to the original browser location where they initiated the sign-in attempt. Okta ensures that end users can prove ownership of both the originating tab and the tab where they clicked the email magic link. See Configure the Email authenticator and Sign in to resources protected by Okta. This feature is now enabled by default for all orgs.
Improvements to the self-service registration experience
Earlier versions of the self-service registration (SSR) flow used a complicated array of templates to send activation emails to end users. The simplified SSR flow reduces this to only two email templates with customized welcome messages. If your application requires immediate verification of the end user’s email address, Okta uses the Registration - Activation template. This template includes a magic link for a smoother sign-in experience. If email verification isn't immediately required to sign in to the application, Okta uses the Registration - Email Verification template. This template includes a link for end users to complete email verification at any time after they successfully sign in to the application. See Customize email notifications and the Okta email (magic link/OTP) integration guide. This feature is now enabled by default for all orgs.
Improvements to the self-service password reset experience
Previously, the self-service password reset (SSPR) flow created unnecessary friction in the user experience. The newly enhanced SSPR feature introduces a seamless magic link experience for password reset emails. Users no longer need to provide consent when using the same browser. After a successful password reset where the password meets the application’s assurance policy, the user is signed directly to the app. See Configure the Email authenticator. This feature is now enabled by default for all orgs.
Improvements to the self-service unlock process
Earlier versions of the self-service unlock (SSU) flow created unnecessary friction in the end user experience. The newly enhanced SSU feature introduces a seamless magic link experience in emails sent out to unlock accounts. Users no longer need to provide consent when using the same browser. In addition, after successfully unlocking their account, clicking the email magic link counts towards the application's assurance policy. After the assurance requirements are met, the user is signed directly in to the application. See Configure the Email authenticator. This feature is now enabled by default for all orgs.
Improvements to self-service account activities for AD and LDAP users
Previously, the self-service unlock (SSU) and self-service password reset (SSPR) flows created unnecessary friction for AD and LDAP users. This enhancement introduces a seamless magic link in emails sent to unlock accounts and reset passwords. Users no longer need to provide consent when using the same browser. In addition, after successfully unlocking their account, clicking the email magic link counts towards the application's assurance policy. After the assurance requirements are met, the user is signed in directly to the application. See Configure the Email authenticator. This feature is now enabled by default for all orgs.
Help links for standard admin roles
In Administrators > Roles, each standard admin role now provides a link to its corresponding help page. This allows admins to quickly and easily locate the documentation that supports their standard role assignments.
Unauthorized IdP setup options hidden
Two group-related options on the IdP configuration page were visible to admins in a custom role that lacked group viewing permissions: Auto-Link Restrictions in Authentication Settings and Group Assignments in JIT Settings. Now these settings are visible only when the user has the appropriate permissions.
More events eligible for hooks
The following System Log events are now eligible for event hooks:
-
group.application_assignment.add
-
group.application_assignment.remove
-
group.application_assignment.update
New legal disclaimer in Okta Trial accounts
A new legal disclaimer is displayed on the Add Person dialog in Okta trial accounts to prevent sending unsolicited and unauthorized activation emails.
Okta branding changes for the Admin Console
Branding updates to headings, fonts, colors, borders, and logos are now available in the Admin Console.
Additional measures to counter toll fraud
For SMS and voice authentications, additional mitigation measures now help counter phone number-based toll fraud.
Early Access Features
Event hook filters
You can now filter individual events of the same event type based on custom business logic hosted in Okta. These filters reduce the amount of events that trigger hooks, removing an unnecessary load on your external service.
This feature includes an improved creation workflow for event hooks and a new Filters tab that you can use to create event filters with direct Expression Language statements or with a simple UI format.
Using event hook filters significantly reduces the amount of event hook requests and the need for custom code on your respective services. See Edit an event hook filter.
-
OKTA-566113
After changing the display language for an Okta org from English to another language, some text was still displayed in English.
-
OKTA-580684
In the Okta Expression Language, the isMemberOfGroupNameContains expression couldn't differentiate underscores and hyphens, which caused unexpected user membership assignments.
-
OKTA-587429
Admins saw Okta FastPass listed in the GET /api/v1/users/{{userId}}/factors response for users who didn't enable the factor.
-
OKTA-595053
Users who clicked Back to sign in before setting up their security methods were incorrectly notified that their configuration was successful. This occurred only in orgs with custom domains.
-
OKTA-596444
Users received an error message after successfully performing a self-service account unlock.
-
OKTA-596600
For apps with Group Push enabled, the tab displayed incorrect dates and times.
-
OKTA-597396
Pushing groups from Okta to Microsoft Office 365 sometimes failed if an empty group description was updated.
-
OKTA-599408
GMT timezones couldn't be selected correctly in the System Log.
-
OKTA-600867
The Yubikey Reports page wasn't properly translated.
-
OKTA-600874
When a user responded to a Custom Push prompt while attempting to edit their profile, the profile displayed in read-only mode. If the user tried to edit their profile again, an authentication loop occurred.
-
OKTA-603305
On the Edit resource set page, an error appeared when an admin deleted a resource type and then added it again. This occurred when the redesigned resource editor feature was enabled.
-
OKTA-607249
Service clients with the correct permissions couldn't modify policies that contained the Okta Administrator Group.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog:
-
360Learning: For configuration information, see OKTA: configuration guide.
-
Forest Admin: For configuration information, see Forest Admin User Guide.
-
Pigeonhole Live: For configuration information, see Configuring Provisioning for Pigeonhole Live.
-
Recurly: For configuration information, see SCIM for Okta.
-
Tines: For configuration information, see How to Configure SAML 2.0 for Tines for admins.
SAML for the following Okta Verified applications
-
Demio: For configuration information, see How to Configure SAML 2.0 for Demio.
-
Flagsmith: For configuration information, see Okta Configuration Guide.
- Sendoso (OKTA-543675)
OIDC for the following Okta Verified applications
-
cmBuilder: For configuration information, see Okta Single Sign-On (SSO) - Configuration Guide.
-
Vozzi: For configuration information, see Okta Integration Configuration Guide.
Weekly Updates
Fixes
-
OKTA-542869
Users were prompted to set up voice call authentication even though SMS authentication was already set up in the Phone authenticator.
-
OKTA-570696
Some placeholder values in the Password Changed email template weren't translated.
-
OKTA-588667
After creating accounts, some users weren't able to complete the sign-in process.
-
OKTA-596446
Error summary messages weren't written to the System Log when custom errors occurred during an import inline hook operation.
-
OKTA-597490
The LDAP interface didn't return any result for a deactivated user when the cn value was combined with other filters.
-
OKTA-597959
Okta users authenticating through Agentless Desktop SSO (ADSSO) were sometimes incorrectly shown a migration-check error message.
-
OKTA-601618
Email change confirmation notices came from an Okta test account rather than a brand-specific sender.
-
OKTA-603731
Macros in email subjects weren't processed correctly for some email templates.
-
OKTA-604404
Imports performed during UltiPro maintenance resulted in inconsistent data being returned.
-
OKTA-604914
When the redesigned resource editor feature was enabled, admins couldn’t add individual applications to their resource sets.
-
OKTA-609336
Incorrect descriptions were displayed on the Agents > On-premise tab.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog:
- Apollo.io: For configuration information, see Configure SCIM User Provisioning in Okta for Your Apollo Account.
- CrashPlan: For configuration information, see How to provision users to CrashPlan from Okta.
SAML for the following Okta Verified applications
- Apollo.io: For configuration information, see Set Up Single Sign-On (SSO) with Okta for Your Apollo Account.
- COSgrid MicroZAccess: For configuration information, see How to Configure SAML 2.0 for COSGrid Networks for admins.
- Digital Pigeon: For configuration information, see Okta SSO Configuration (OIN Guide).
- Kallidus HR: For configuration information, see Kallidus Sapling - Okta Integration Guide.
- Reach Security: For configuration information, see SAML Onboarding (you need to sign in to view this documentation).
- Sauce Labs: For configuration information, see Configuring SSO in Okta.
OIDC for the following Okta Verified applications
- Cledara: For configuration information, see Integrate with Okta.
- DNSimple: For configuration information, see Okta as an Identity Provider.
Fixes
-
OKTA-414791
LDAP requests resulted in an error if the memberOf filter didn't include a Group DN.
-
OKTA-423781
The Privacy link on the Okta dashboard wasn't translated.
-
OKTA-585123
When the Full Featured Code Editor was enabled, some admins couldn't edit the Sign-In Widget version or their sign-in page draft changes.
-
OKTA-591228
Admins with a custom role couldn’t receive user reports of suspicious activity in email notifications.
-
OKTA-592530
A deleted policy rule was still referenced in the System Log when a user signed in to Office 365.
-
OKTA-594682
Sometimes user session IDs weren't unique per session.
-
OKTA-595145
After a user enrolled in Okta Verify, the session displayed inconsistent AMR values.
-
OKTA-599276
SSO on mobile devices where an OIDC token exchange occurred between two apps sometimes failed for the second app.
-
OKTA-599817
Scope grant requests failed if any of the scope names contained periods.
-
OKTA-602635
Some text on the Administrator assignment by role page wasn’t translated properly.
-
OKTA-602794
Token inline hooks failed even when a URL claim name was correctly encoded with a JSON pointer.
-
OKTA-602932
FastPass Smart Signal Collection attempted to gather signals from users without Okta Verify.
-
OKTA-603996
WebAuthn enrollment sometimes failed if the authentication policy enforced hardware-protected possession constraints.
-
OKTA-604825
When an admin added the Manage users permission to a role, any existing permission conditions were removed. Also, admins with restricted profile attributes could edit those attributes on their own profile.
-
OKTA-609070
Some users couldn't unlock their accounts if they had multiple Okta Verify and phone authenticator enrollments.
-
OKTA-613226
Some of the new Okta branding changes weren’t displayed in the Admin Console.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog:
- Dagster Cloud: For configuration information, see Dagster Cloud Okta user provisioning guide with SCIM.
SAML for the following Okta Verified applications
- Amplified: For configuration information, see Okta SAML integration.
- Healthfeed: For configuration information, see Healthfeed Customer Configuration.
API service app for the following Okta Verified applications
- Kandji Device Trust: For configuration information, see Okta Device Trust.
- Sevco Security: For configuration information, see Configure the Sevco Security app in Okta.
OIDC for the following Okta Verified applications
- Amplified: For configuration information, see Okta OIDC SSO integration.
- Debricked OIDC SSO: For configuration information, see Set up Single Sign On (SSO) for Debricked.
- DNSimple: For configuration information, see Okta as an Identity Provider.
- Software Analytics: For configuration information, see Okta Setup.
- Zesty.io: For configuration information, see Okta SSO Configuration Guide.
Fixes
-
OKTA-516583
The application logo wasn't displayed on the Groups page for some groups.
-
OKTA-554024
Some users received a Bad Request message after successfully unlocking their accounts.
-
OKTA-566503
When no tokens were listed on the API Tokens page, the displayed message wasn't translated.
-
OKTA-572820
Deleting large numbers of IdP routing rules with API calls caused System Log discrepancies.
-
OKTA-577794
The destination in SAML responses sometimes didn't match the Assertion Consumer Service URL in signed authentication requests.
-
OKTA-583072
The System Log showed that an MFA reset notification email was sent when that notification option was disabled and no email was sent.
-
OKTA-595603
The Forgot Password link didn't work unless orgs enabled User Enumeration Prevention and disabled Profile Enrollment.
-
OKTA-597009
The Microsoft Team Exploratory licenses weren't imported correctly into Okta, which prevented users from provisioning the correct licenses.
-
OKTA-599540
HTTP replies to SP-initated SAML requests contained two session IDs, which sometimes caused user sessions to expire unexpectedly.
-
OKTA-599994
The Honor Force Authentication SAML setting didn't work with Agentless Desktop Single Sign-on (ADSSO).
-
OKTA-602946
On password hash import, users couldn't change their passwords even after the minimum password age setting period.
-
OKTA-604985
Approvers received duplicate task approval requests when users requested an app from the End-User Dashboard.
-
OKTA-605016
In the Add Dynamic Zone dialog, the Bagmati region of Nepal was missing from the State/Region dropdown menu.
-
OKTA-605955
Users were prompted for Okta FastPass or WebAuthn after they'd satisfied the possession requirements of an authentication policy.
-
OKTA-606914
Some orgs weren't migrated to newly deployed default app versions.
-
OKTA-607167
The search bar in the Groups tab on the user profile page didn't display the placeholder text correctly.
-
OKTA-610185
When the Conditions for Admin Access feature was enabled, restricted profile attributes were visible in > for imported users.
-
OKTA-611235
After upgrading to Identity Engine, some orgs experienced undesired behavior with apps that shared authentication policies.
-
OKTA-611867
The Active User Statuses field didn't appear in some configurations.
-
OKTA-612177
Some users in China didn't receive one-time passwords through SMS.
-
OKTA-612312
Admins couldn't delete a custom email domain if it was used by multiple orgs.
-
OKTA-612972
When the redesigned resource editor feature was enabled, large sets of resources were displayed outside of the Add Resource dialog, and the tooltip didn’t specify the resource limit.
-
OKTA-613226
Some of the Okta branding changes weren’t displayed in the Admin Console.
-
OKTA-613979
The Microsoft Office 365 Sign On tab displayed incorrect information in the Metadata details section.
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog:
- Cisco Webex Identity SCIM 2.0: For configuration information, see Okta users and groups provisioning integration with Cisco Webex Identity SCIM 2.0.
- Foxit Admin Console: For configuration information, see Automatically Provision Licenses for OKTA.
- Outgage: For configuration information, see Configure user provisioning with Okta.
SAML for the following Okta Verified applications
- BugBase: For configuration information, see SSO with SAML.
- Currents: For configuration information, see Setting up SAML2.0 SSO with Okta as an IdP - Cypress SSO.
- Experian Right to Work: For configuration information, see Experian Right To Work SSO App.
- Foxit Admin Console: For configuration information, see How to integrate Foxit Admin Console with Okta.
- Mimoto: For configuration information, see Setting up single sign-on (SSO).
- National Crime Check: For configuration information, see Enable SSO for Okta.
- Rapidr: For configuration information, see Integrate with an identity provider and sign in with SAML SSO.
- Raydiant Employee Experience: For configuration information, see How to Configure SAML 2.0 for Raydiant.
- Scytale: For configuration information, see Configure Okta SSO.
- SellerCrowd: For configuration information, see Configuring SSO using OKTA.
- Sitejabber: For configuration information, see SiteJabber Okta Guidelines (you need Sitejabber credentials to view this documentation).
- Stack Identity Cloud IAM Ops: For configuration information, see OKTA SSO Guide.
API service app for the following Okta Verified application
- SGNL: For configuration information, see Creating and Configuring an Okta System of Record.
OIDC for the following Okta Verified applications
- Digioh: For configuration information, see Digioh Okta Configuration Guide.
- Moveworks: For configuration information, see OKTA SSO Configuration Guide.
- RefNow: For configuration information, see Setup Okta SSO.
- Stomio for Managers: For configuration information, see Setup SSO with Okta.
- Uplifter: For configuration information, see Using Okta for Single Sign On (SSO).