Add SharePoint (On-Premises) in Okta
Before you begin
-
Install a supported version of Microsoft SharePoint:
- SharePoint Foundation 2013
- SharePoint Server 2013
- SharePoint Server 2016
- SharePoint Server 2019
- Run the prerequisites from the SharePoint installer.
- Fulfill hardware requirements.
-
Fulfill version-specific requirements:
Version Requirements SharePoint People Picker (versions before 2.3.0.0) Install .NET Framework 3.5+ SharePoint People Picker version 2.3.0.0 Ensure TLS 1.2 is supported by your server. SharePoint 2013, 2016, or 2019 Install .NET Framework 4.5+, which supports TLS 1.2.
OR
Install .NET Framework 3.5+ and one of the patches provided here.
-
A valid API token for the Okta People Picker plugin to read users and groups from Okta. See API token management.
The API token is only visible upon creation and cannot be retrieved later. If the token is lost, it must be revoked, regenerated, and reconfigured in the People Picker configuration.
Start this procedure
-
Add the SharePoint (On-Premises) app.
Go to Applications > Applications > Add Application and search for the app.
-
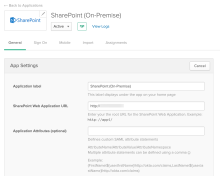
From the General tab, go to App Settings and fill in the appropriate fields. These fields are used to connect and send information as part of the SAML assertion to SharePoint:
- SharePoint Web Application URL: This points to the web application that is running on SharePoint. For example,
https://app1. There can be multiple apps running on SharePoint, each of which needs a SharePoint app within Okta. -
Application attributes: Admins can send information about Okta user profile attributes to SharePoint for auditing or logging purposes. Sending any custom Okta attributes is also supported. This information is not used for authentication or authorizing apps in SharePoint. Okta typically sends UPN and email data as part of the assertion.
Acceptable formats for application attributes are:
- Group filter: This field is sent as part of a SAML assertion. This is used for checking permissions in SharePoint.
- SharePoint Web Application URL: This points to the web application that is running on SharePoint. For example,
-
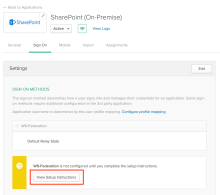
Go to SharePoint (On-Premise) app > Sign On > View Setup Instructions to install and configure SharePoint People Picker 2.3.0.0.
Okta Group Push is not currently supported with the SharePoint On-Premises application.
We recommend you use only AD groups or only Okta groups in order to configure authorization to your SharePoint server. Configuring Push Groups to your Active Directory and attempting to use these groups for SharePoint authorization will result in problems accessing the application.
Next steps
Configure Okta as Claims Provider in SharePoint (On-Premises)