Not protected application reference architecture
The not, or none, protected application Access Gateway really isn't an protected architecture at all, as it represents a baseline or a starting point after an application is integrated with Access Gateway but before any steps are taking to significantly deny direct access to the backing protected web resource.
In this architecture, a single application, referred to as protected web resource, is served to requesting clients using Access Gateway. All URLs (Access Gateway and the backing protected web resource) are typically resolvable using a single DNS server and accessible to all.
This architecture meets the following requirements:
- No specialized configuration.
- URLs (Access Gateway and application) are entered into DNS but no further action is taken.
- Can be used as a baseline for testing and development.
Benefits and drawbacks
| Benefits | Drawbacks |
|---|---|
|
|
Architecture
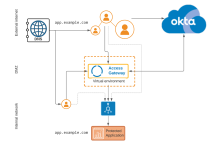
In this architecture, external clients can access the application directly if they know the internal URL/IP. Likewise internal network clients can also access the application directly. Represented by neither dotted access path being blocked.
Components
|
Location |
Component | Description |
|---|---|---|
| External internet | External URL | External URL used by clients to access Access Gateway on behalf of the protected web resource. |
|
DNS |
DNS server providing DNS resolution for both the external URL and the internal (protected web resource |
|
| DMZ | Access Gateway | Access Gateway cluster, located in the DMZ is used to provide access to applications used by external internet clients. Typically hosted in a virtual environment such as Amazon Web Services, MS Azure, Oracle OCI or something similar. See Manage Access Gateway deployment. |
| Internal network |
Internal URL |
Internal URL, represented by protected web resource in Access Gateway. |
| Application | Protected web resource (application) | |
