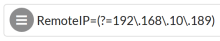Example Access Gateway policy
- Protected policy
- Protected rule policy
- Allow any authenticated user access
- Allow any authenticated user in the IDP Everyone group access
- Allow no authentication access
- Allow specific users access
- Allow specific groups access
- Allow specific groups and users access (multiple matches)
- Deny specific groups or users access
- Allow or deny specific RemoteIP access
- Allow or deny specific USER_AGENT access
The document provides examples on how to configure various policy access rules. These rules can be configured using the Policy Application Editor.
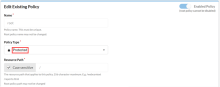
Protected policy
| Field | Value |
|---|---|
| Enabled Policy | Enable or disable policy. |
|
Policy Type |
Protected or Not Protected. |
|
Name |
A unique name for the policy. |
|
Resource Path |
The resource path to the resource you want this policy to manage. |
|
Description |
An admin friendly description to help describe the policy for future reference. |
Protected rule policy
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule. |
|
Name |
A unique name for the policy. |
|
Resource Path |
The resource path to the resource you want this policy to manage. |
|
Resource Matching Rule |
This field allows you to define the regular expression for the policy. See Protected rule resource matching rule expressions. |
|
Description |
An admin-friendly description to help describe the policy for future reference. |
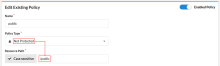
Allow any authenticated user access
The default rule of all protected applications is set to allow any authenticated user. When enabled, the following policy allows any authenticated user to access the root URL (/):
| Field | Value |
|---|---|
|
Resource Rule |
Protected |
|
Resource Path |
/ |
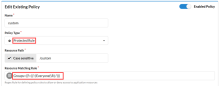
Allow any authenticated user in the IDP Everyone group access
If many policies are being configured for an application and a deep link needs to use the default authentication behavior, configure the policy to allow the Everyone group.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/custom |
|
Resource Matching Rule |
Groups=((?=(|.:)Everyone(R|:.*))) |
Allow no authentication access
If there's a URL that needs to be accessed by anyone regardless of authentication, set the Resource Rule as Not Protected.
| Field | Value |
|---|---|
|
Resource Rule |
Not Protected |
|
Resource Path |
/public |
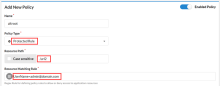
Allow specific users access
If there's a URL that needs to be accessed by a specific user, set the Matching Rule Regex to the username to allow for the policy. The following example is set to allow the user admin@domain.com access to the URL /uri2.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri2 |
|
Resource Matching Rule |
UserName=admin@domain.com |
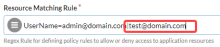
To separate multiple usernames, use the vertical bar (|) key. In the next example, you allow access to both users: admin@domain.com and test@domain.com.
If you need to allow multiple users, use the vertical bar key (|) to separate the username. The following example expands on the previous example to allow both admin@domain.com and test@domain.com.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri2 |
|
Resource Matching Rule |
UserName=admin@domain.com | test@domain.com |
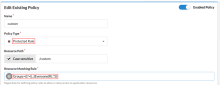
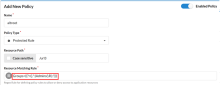
Allow specific groups access
If there's a URI that needs to be accessed by a specific group, set the Matching Rule Regex to the group name to allow for the policy. The following example sets the Matching Rule option to allow the Group: Admins to access to the URI /uri3.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri3 |
|
Resource Matching Rule |
Groups=((?=(|.*:)Admins(\R|:.*))) |
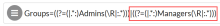
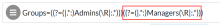
If you need to allow the option of multiple groups use the vertical bar key (|) to separate them. This is an OR condition. The following example allows Group: Admins OR Group: Managers.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri3 |
|
Resource Matching Rule |
Groups=((?=(|.*:)Admins(\R|:.*)))|((?=(|.*:)Managers(\R|:.*))) |
If you require multiple groups, you can use an AND condition. The following example allows Group: Admin AND Group: Managers:
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri3 |
|
Resource Matching Rule |
Groups=((?=(|.*:)Admins(\R|:.*)))((?=(|.*:)Managers(\R|:.*))) |
Allow specific groups and users access (multiple matches)
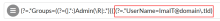
If there's a URI that needs to be accessed by a specific group and user, set the Matching Rule Regex to the group name to allow for the policy. The following example sets the Resource Matching Rule to allow the Group: Admin AND User: IamIT@domain.tld.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri3 |
|
Resource Matching Rule |
(?=.*Groups=((?=(|.*:)Admin(\R|:.*))))(?=.*UserName=ImaIT@domain\.tld) |
Deny specific groups or users access
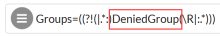
If there's a URI that should be accessible by everyone except a certain group, set the Matching Rule Regex to the group name and allow for the policy. The following example sets the Matching Rule option to allow users in any group except the those in Group: DeniedGroup.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri3 |
|
Resource Matching Rule |
Groups=((?!(|.*:)DeniedGroup(\R|:.*))) |
The following example expands on our previous example, setting the Matching Rule option to multiple constraints. If Group: Admins contains anyone with the UserName=denied@domain.tld, they won't be allowed to access the URI.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri3 |
|
Resource Matching Rule |
(?=.*Groups=((?=(|.*:)Admins(\R|:.*))))(?=.*UserName=(?!denieduser@domain\.tld)) |
Allow or deny specific RemoteIP access
If there's a URI that you only want to be accessed by a specific RemoteIP, set the Matching Rule Regex to the RemoteIP to allow for the policy. The following example sets the Matching Rule option to allow the RemoteIP address 192.168.10.189 access.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri4 |
|
Resource Matching Rule |
RemoteIP=(?=192\.168\.10\.189) |
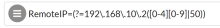
The following example expands on our previous example, setting the Matching Rule option to allow a range of RemoteIPs. The following example sets the Resource Matching Rule to allow RemoteIPs within the range of 192.168.10.200 to 192.168.10.250.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri4 |
|
Resource Matching Rule |
RemoteIP=(?=192\.168.10.2([0-4][0-9]|50)) |
If there's a URI that you would like to deny access to by a specific RemoteIP set the Matching Rule Regex to the RemoteIP to deny for the policy. The following example sets the Resource Matching Rule option to deny the RemoteIP address 192.168.10.209 access.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri4 |
|
Resource Matching Rule |
RemoteIP=(?!192.168.10.209) |
The following example expands on our previous example, setting the Matching Rule option to deny a range of RemoteIPs. The following example sets the Matching Rule option to deny RemoteIPs within the range of 192.168.10.100 to 192.168.10.200.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri4 |
|
Resource Matching Rule |
RemoteIP=(?!192\.168\.10\.(1([0-9][0-9])|200)) |
Allow or deny specific USER_AGENT access
If there's a URI that you only want to be accessed by a specific USER_AGENT (browser) set the Matching Rule Regex to the USER_AGENT to allow for the policy. The following example sets the Matching Rule option to allow the USER_AGENT to only access the URI using Google Chrome.
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri5 |
|
Resource Matching Rule |
USER_AGENT=(?=.*Chrome) |
The following example expands on our previous example, instead setting the Resource Matching Rule option to deny USER_AGENT access to Google Chrome, thereby forcing access using another agent (browser).
| Field | Value |
|---|---|
|
Resource Rule |
Protected Rule |
|
Resource Path |
/uri5 |
|
Resource Matching Rule |
USER_AGENT=(?!.*Chrome) |